1 habp configuration, Introduction to habp, Habp configuration – H3C Technologies H3C S5120 Series Switches User Manual
Page 522
1-1
1
HABP Configuration
When configuring HABP, go to these sections for the information you are interested in:
z
z
z
Displaying and Maintaining HABP
z
Introduction to HABP
The HW Authentication Bypass Protocol (HABP) is used to enable the downstream network devices of
an 802.1X enabled access device to bypass 802.1X authentication.
HABP is usually adopted at the access layer of a campus or enterprise network. This feature is useful
when 802.1X authentication or MAC address authentication is adopted on the management switch of a
cluster, in which case you must configure HABP to allow the packets between the member devices of
the cluster to bypass 802.1X authentication because network devices usually do not support 802.1
client. Otherwise, the management device will fail to perform centralized management of the cluster
member devices. For more information about the cluster function, refer to Cluster Configuration.
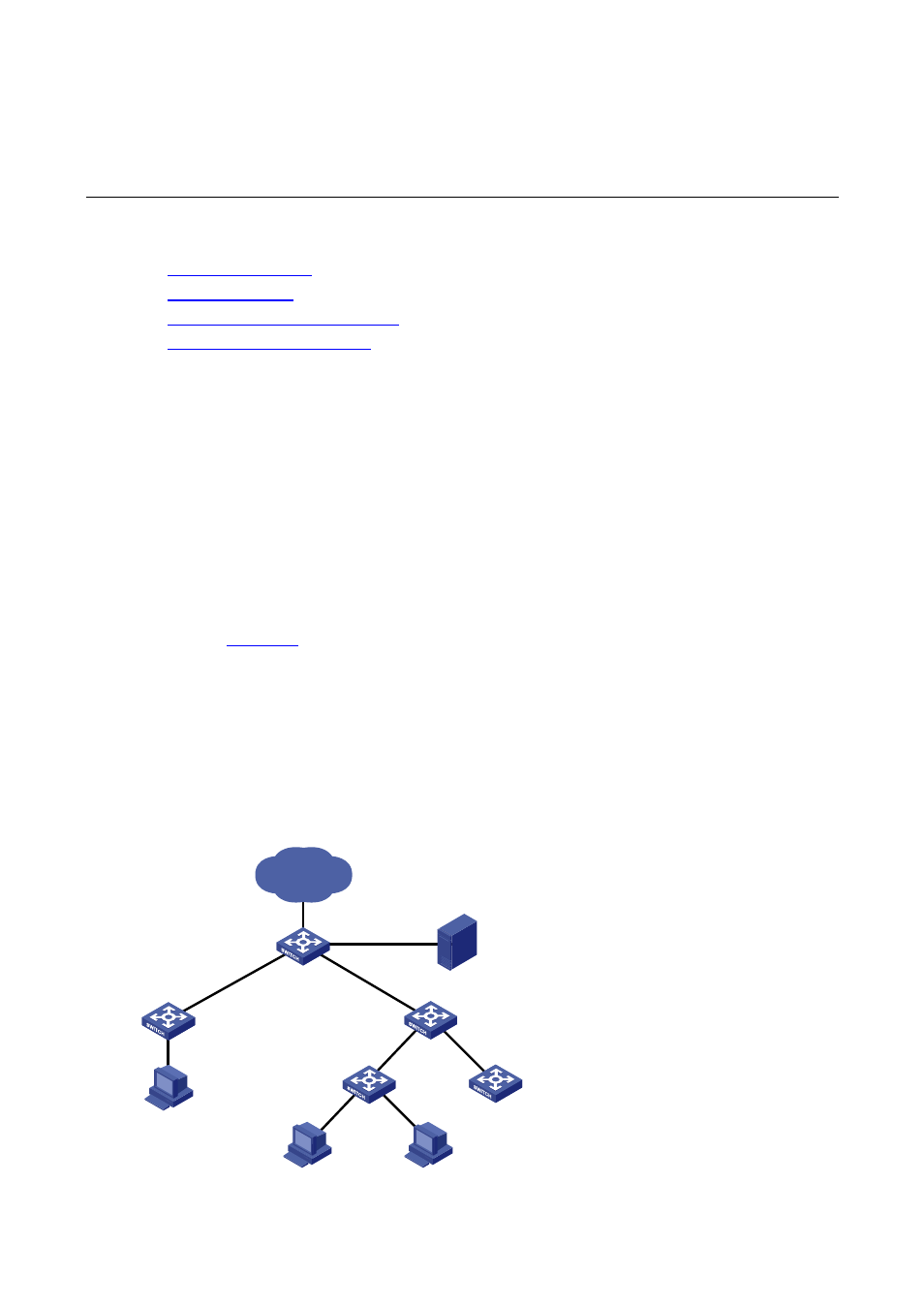
As shown in
, 802.1X authenticator Switch A has two switches attached to it: Switch B and
Switch C. On Switch A, 802.1X authentication is enabled globally and on the ports connecting the
downstream network devices. The end-user devices (the supplicants) run the 802.1X client software for
802.1X authentication. For Switch B and Switch D, where 802.1X client is not supported (which is
typical of network devices), the communication between them will fail because they cannot pass 802.1X
authentication and their packets will be blocked on Switch A. To allow the two switches to communicate,
you can use HABP.
Figure 1-1 Network diagram for HABP application
Internet
Switch B
Switch C
Authenticator
Supplicant
Switch A
Supplicant
Supplicant
Switch D
Switch E
Authentication
server
