H3C Technologies H3C S5120 Series Switches User Manual
Page 234
2-6
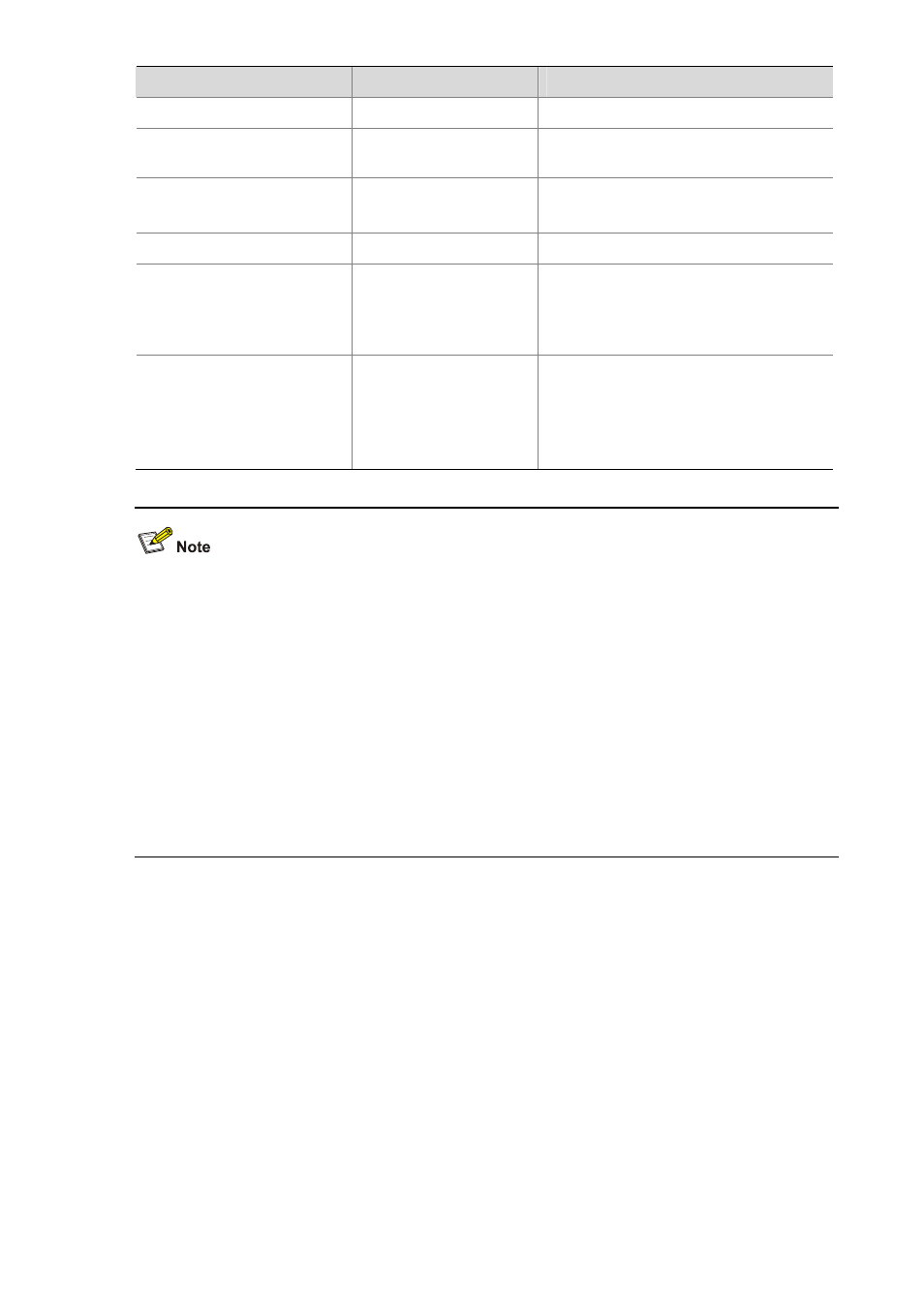
To do…
Use the command…
Remarks
Return to system view
quit
—
Enter Ethernet interface view
interface interface-type
interface-number
—
Configure the port as a
trusted port
arp detection trust
Optional
The port is an untrusted port by default.
Return to system view
quit
—
Specify an ARP attack
detection mode
arp detection mode
{ dhcp-snooping |
dot1x | static-bind }
Required
No ARP attack detection mode is
specified by default; that is, all packets
are considered to be invalid by default.
Configure a static IP-to-MAC
binding for ARP detection
arp detection
static-bind ip-address
mac-address
Optional
Not configured by default.
If the ARP attack detection mode is
static-bind, you need to configure static
IP-to-MAC bindings for ARP detection.
z
If all the detection types are specified, the system uses IP-to-MAC bindings first, then DHCP
snooping entries, and then 802.1X security entries. If an ARP packet fails to pass ARP detection
based on static IP-to-MAC bindings, it is discarded. If the packet passes this detection, it will be
checked against DHCP snooping entries. If a match is found, the packet is considered to be valid
and will not be checked against 802.1X security entries; otherwise, the packet is checked against
802.1X security entries. If a match is found, the packet is considered to be valid; otherwise, the
packet is discarded.
z
Before enabling ARP detection based on DHCP snooping entries, make sure that DHCP snooping
is enabled.
z
Before enabling ARP detection based on 802.1X security entries, make sure that 802.1X is
enabled and the 802.1X clients are configured to upload IP addresses.
Configuring ARP Detection Based on Specified Objects
You can also specify objects in ARP packets to be detected. The objects involve:
z
src-mac: Checks whether the sender MAC address of an ARP packet is identical to the source
MAC address in the Ethernet header. If they are identical, the packet is forwarded; otherwise, the
packet is discarded.
z
dst-mac: Checks the target MAC address of ARP replies. If the target MAC address is all-zero,
all-one, or inconsistent with the destination MAC address in the Ethernet header, the packet is
considered invalid and discarded.
z
ip: Checks both the source and destination IP addresses in an ARP packet. The all-zero, all-one or
multicast IP addresses are considered invalid and the corresponding packets are discarded. With
this object specified, the source and destination IP addresses of ARP replies, and the source IP
address of ARP requests are checked.
