1 802.1x configuration, 1x overview, Architecture of 802.1x – H3C Technologies H3C S5120 Series Switches User Manual
Page 379: 1x configuration
1-1
1
802.1X Configuration
This chapter includes these sections:
z
z
802.1X Configuration Task List
z
z
Guest VLAN and VLAN Assignment Configuration Example
z
ACL Assignment Configuration Example
802.1X Overview
The 802.1X protocol was proposed by IEEE 802 LAN/WAN committee for security of wireless LANs
(WLANs). However, it has been widely used on Ethernet as a common port access control mechanism.
As a port-based network access control protocol, 802.1X authenticates devices connected to the
802.1X-enabled LAN ports to control their access to the LAN.
To get more information about 802.1X, go to these topics:
z
z
Authentication Modes of 802.1X
z
z
z
z
802.1X Authentication Triggering
z
Authentication Process of 802.1X
z
z
Features Working Together with 802.1X
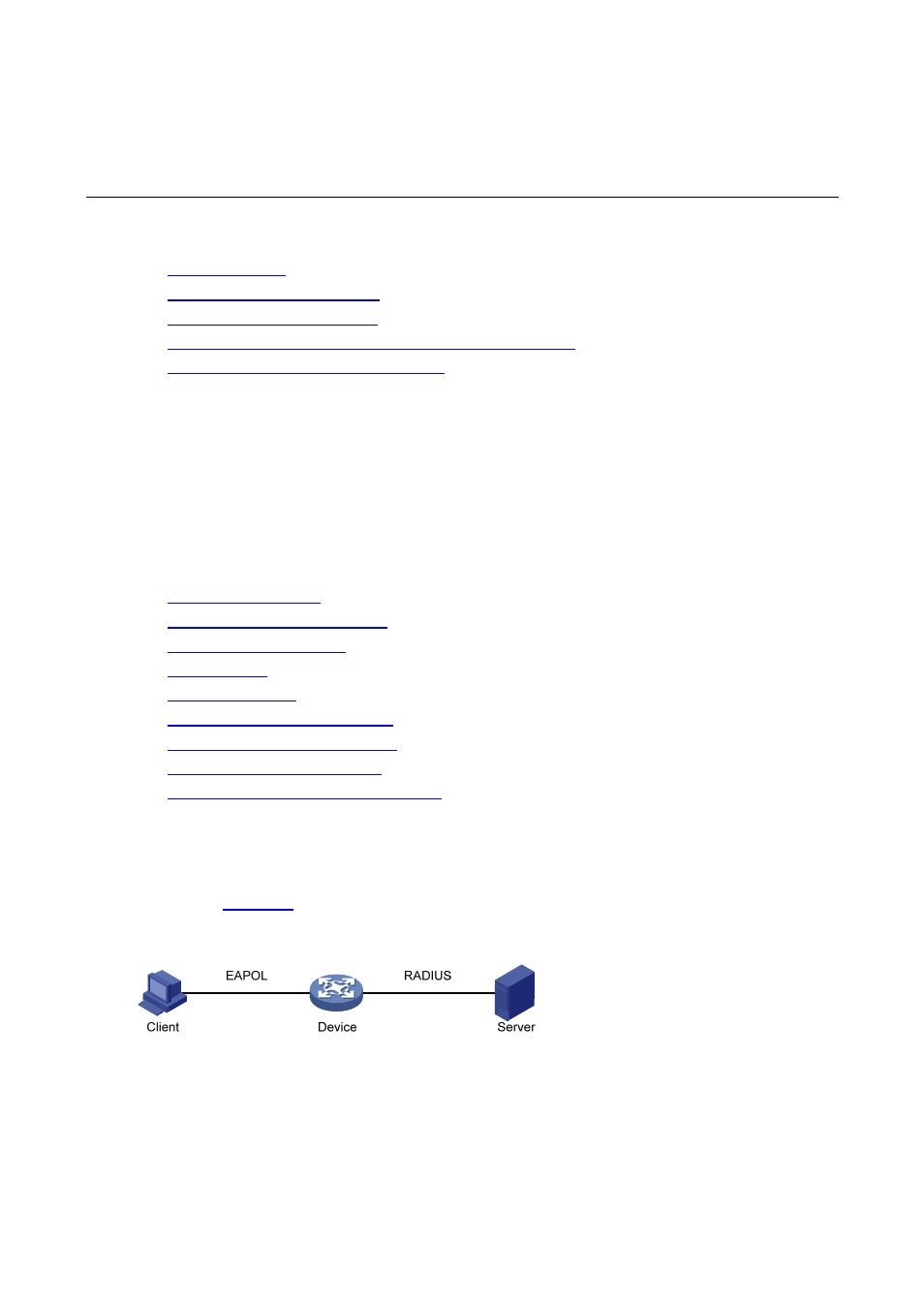
Architecture of 802.1X
802.1X operates in the typical client/server model and defines three entities: Client, Device, and Server,
as shown in
.
Figure 1-1 Architecture of 802.1X
z
Client is an entity seeking access to the LAN. It resides at one end of a LAN segment and is
authenticated by Device at the other end of the LAN segment. Client is usually a user-end device
such as a PC. 802.1X authentication is triggered when an 802.1X-capable client program is
launched on Client. The client program must support Extensible Authentication Protocol over LAN
(EAPOL).
