3 encrypted memory, Ncrypted, Emory – Maxim Integrated Secure Microcontroller User Manual
Page 76
Secure Microcontroller User’s Guide
76 of 187
9.3 Encrypted Memory
The heart of secure microcontroller security is the memory encryption function. Since the NV RAM is
visible, the memory contents and memory bus are encrypted. That is, in real-time, the addresses and data
moving between the RAM and the microcontroller are scrambled by on-chip encryption circuits. Thus, an
attacker that observes the RAM contents or memory bus sees unintelligible addresses and data.
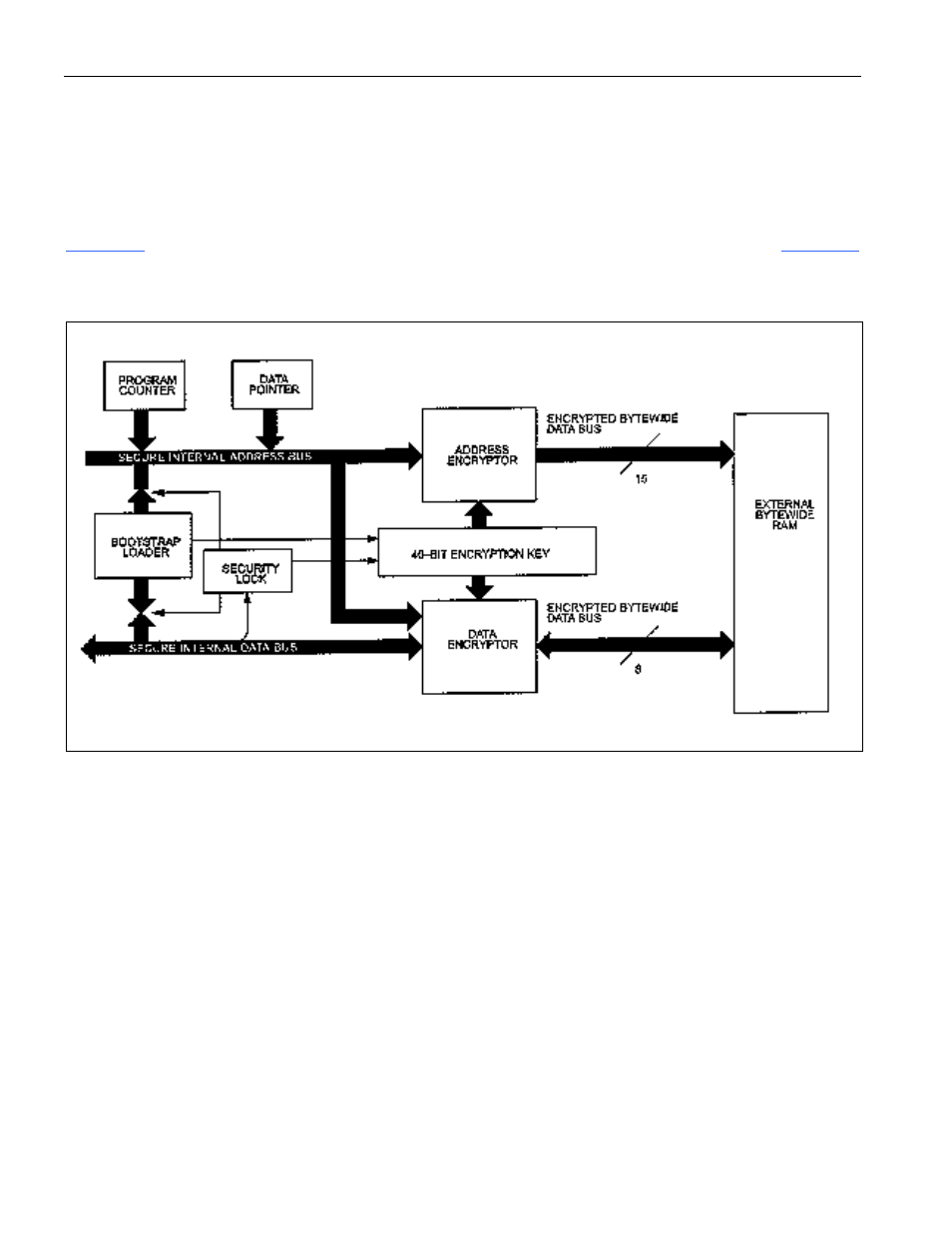
shows the conceptual diagram of the memory encryptor for a DS5000 series device.
shows the encryptor for a DS5002.
Figure 9-1. DS5000 Software Encryption Block Diagram
In a DS5000, the encryption feature is optional. A DS5000 can be locked irrespective of its encryption
and encrypted irrespective of the lock. Neither makes much sense by itself. The encryption process is
enabled by loading an Encryption Key for the first time. Prior to loading a Key, the DS5000 remains in a
nonencrypted state. Once encrypted, the memory interface will remain so until a part is locked, then
unlocked. The process of clearing the Security Lock deactivates the encryption circuits. Note that an
Encryption Key of zero is still a valid Key. The DS5002FP is a superior security device, as it has
encryption enabled at all times and generates its own security keys.
Encryption logic consists of an address encryptor and a data encryptor using separate but related
algorithms. These encryptors are high-speed, bidirectional, and repeatable circuits that are transparent to
the application software. Addresses and data that are scrambled prior to writing to RAM will be correctly
unscrambled when reading. Each encryptor operates with its own algorithm but both are dependent on the
Encryption Key. Encryptors operate while programs are being loaded so that the memory contents are
stored in its scrambled form. When program memory is fetched, the process is reversed. Thus the actual
program or data is only present in its “true” form while inside the microcontroller.
