Hardware security system, Boot memory execution, In section “boot memory execution – Rainbow Electronics AT89C5132 User Manual
Page 20: D in section “hardware security system
20
AT8xC5132
4173A–8051–08/02
Extra Row Space
This space is composed of two Bytes:
•
The Software Boot Vector (SBV see Table 22).
This byte is used by the software bootloader to build the boot address.
•
The Software Security Byte (SSB see Figure ).
This byte is used to lock the execution of some bootloader commands.
Hardware Security
System
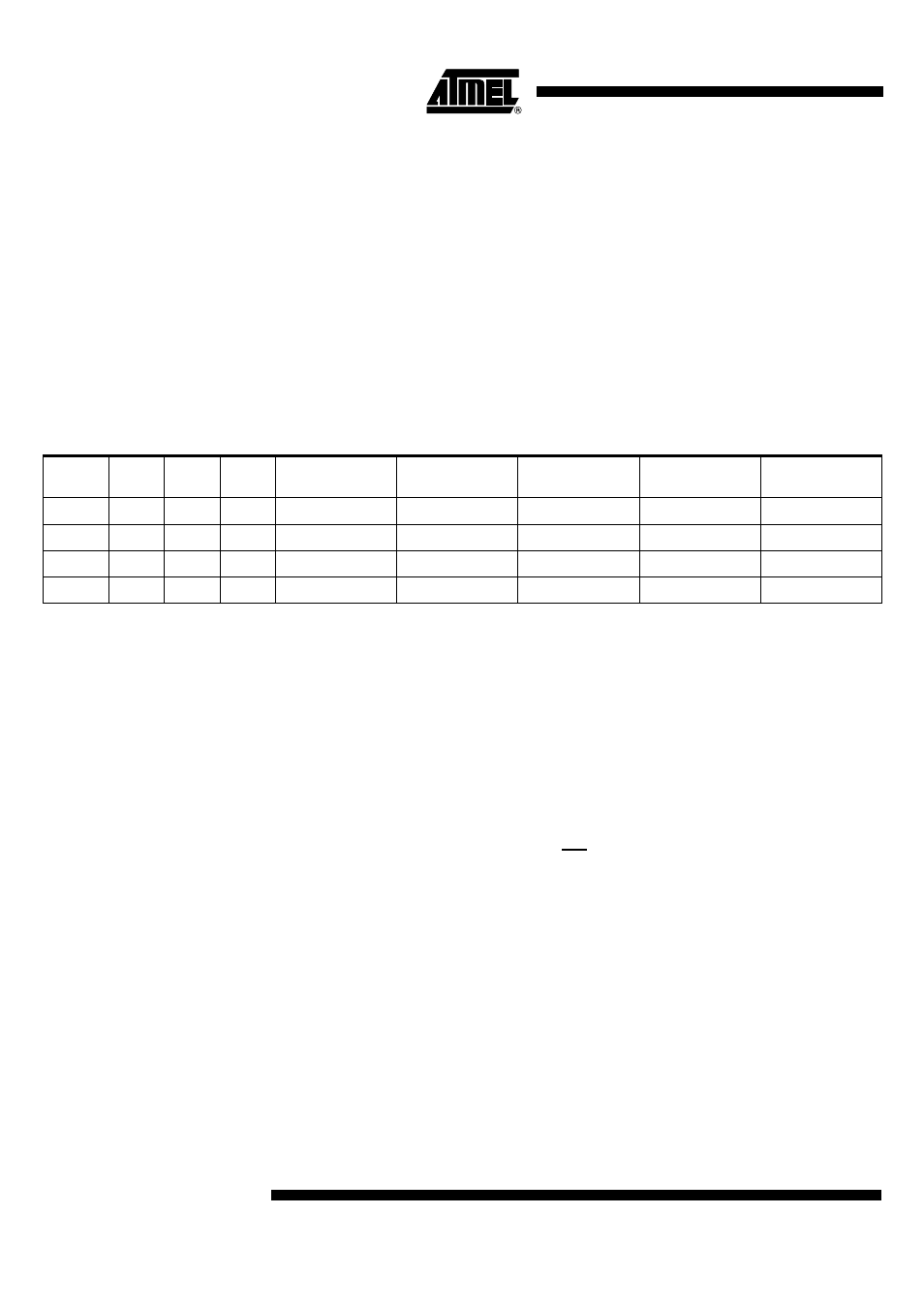
The AT89C5132 implements three lock Bits LB2:0 in the LSN of HSB (see Table 21)
providing three levels of security for user’s program as described in Table 21 while the
AT83C5132 is always set in read disabled mode.
•
Level 0 is the level of an erased part and does not enable any security feature.
•
Level 1 locks the hardware programming of both user and boot memories.
•
Level 2 locks hardware verifying of both user and boot memories.
•
Level 3 locks the external execution.
Notes:
1. U means unprogrammed, P means programmed and X means don’t care (programmed or unprogrammed).
2. LB2 is not implemented in the AT8xC5132 products.
3. AT89C5132 products are delivered with third level programmed to ensure that the code programmed by software using ISP
or user’s bootloader being secured from any hardware piracy.
Boot Memory Execution
As internal C51 code space is limited to 64K Bytes, some mechanisms are implemented
to allow boot memory to be mapped in the code space for execution at addresses from
F000h to FFFFh. The boot memory is enabled by setting the ENBOOT bit in AUXR1
(see Table 20). The three ways to set this bit are detailed in the following sections.
Software Boot Mapping
The software way to set ENBOOT consists in writing to AUXR1 from the user’s soft-
ware. This enables bootloader or API routines execution.
Hardware Condition Boot
Mapping
The hardware condition is based on the ISP pin. When driving this pin to low level, the
chip reset sets ENBOOT and forces the reset vector to F000h instead of 0000h in order
to execute the bootloader software.
As shown in Figure 14, the hardware condition always allows in-system recovery when
user’s memory has been corrupted.
Programmed Condition Boot
Mapping
The programmed condition is based on the Bootloader Jump Bit (BLJB) in HSB. As
shown in Figure 14, when this bit is programmed (by hardware or software programming
mode), the chip resets ENBOOT and forces the reset vector to F000h instead of 0000h,
in order to execute the bootloader software.
Level
LB2
(2)
LB1
LB0
Internal Execution
External Execution
Hardware
Verifying
Hardware
Programming
Software
Programming
0
U
U
U
Enable
Enable
Enable
Enable
Enable
1
U
U
P
Enable
Enable
Enable
Disable
Enable
2
U
P
X
Enable
Enable
Disable
Disable
Enable
3
(3)
P
X
X
Enable
Disable
Disable
Disable
Enable
