Figure 240 menu 27.1.1.1 ike setup, Table 142 menu 27.1.1.1 ike setup – ZyXEL Communications P-335WT User Manual
Page 405
P-335 Series User’s Guide
Chapter 39 VPN/IPSec Setup
405
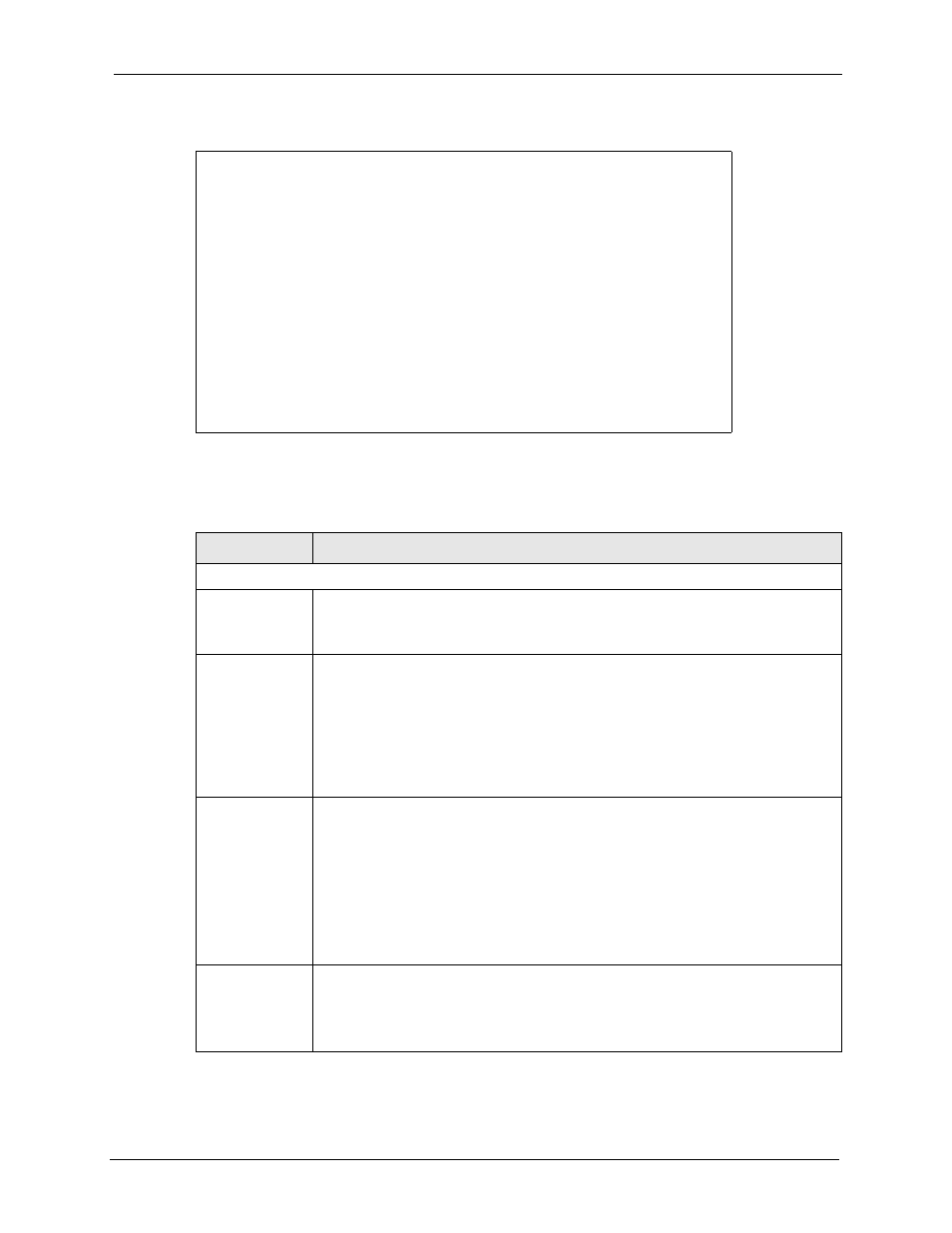
Figure 240
Menu 27.1.1.1 - IKE Setup
Phase 1
Negotiation Mode= Main
PSK= qwer1234
Encryption Algorithm= DES
Authentication Algorithm= MD5
SA Life Time (Seconds)= 28800
Key Group= DH1
Phase 2
Active Protocol= ESP
Encryption Algorithm= DES
Authentication Algorithm= SHA1
SA Life Time (Seconds)= 28800
Encapsulation= Tunnel
Perfect Forward Secrecy (PFS)= None
Press ENTER to Confirm or ESC to Cancel:
Menu 27.1.1.1 IKE Setup
The following table describes the fields in this menu.
Table 142 Menu 27.1.1.1 IKE Setup
FIELD
DESCRIPTION
Phase 1
Negotiation
Mode
Press [SPACE BAR] to choose from Main or Aggressive and then press [ENTER].
See earlier for a discussion of these modes. Multiple SAs connecting through a
secure gateway must have the same negotiation mode.
PSK Prestige gateways authenticate an IKE VPN session by matching pre-shared keys.
Pre-shared keys are best for small networks with fewer than ten nodes. Enter your
pre-shared key here. Enter up to 31 characters. Any character may be used, includ-
ing spaces, but trailing spaces are truncated.
Both ends of the VPN tunnel must use the same pre-shared key. You will receive a
“PYLD_MALFORMED” (payload malformed) packet if the same pre-shared key is
not used on both ends.
Encryption
Algorithm
When DES is used for data communications, both sender and receiver must know
the same secret key, which can be used to encrypt and decrypt the message or to
generate and verify a message authentication code. Prestige DES encryption algo-
rithm uses a 56-bit key.
Triple DES (3DES), is a variation on DES that uses a 168-bit key. As a result, 3DES
is more secure than DES. It also requires more processing power, resulting in
slightly increased latency and decreased throughput.
Press [SPACE BAR] to choose from 3DES or DES and then press [ENTER].
Authentication
Algorithm
MD5 (Message Digest 5) and SHA1 (Secure Hash Algorithm) are hash algorithms
used to authenticate packet data. The SHA1 algorithm is generally considered stron-
ger than MD5, but is slightly slower.
Press [SPACE BAR] to choose from SHA1 or MD5 and then press [ENTER].
