Cisco 3.3 User Manual
Page 81
2-5
User Guide for Cisco Secure ACS for Windows Server
78-16592-01
Chapter 2 Deployment Considerations
Basic Deployment Requirements for Cisco Secure ACS
Note
We tested Cisco Secure ACS on computers that have only one
network interface card.
•
If you want to have Cisco Secure ACS use the “Grant Dial-in Permission to
User” feature in Windows when authorizing network users, this option must
be selected in the Windows User Manager or Active Directory Users and
Computers for the applicable user accounts.
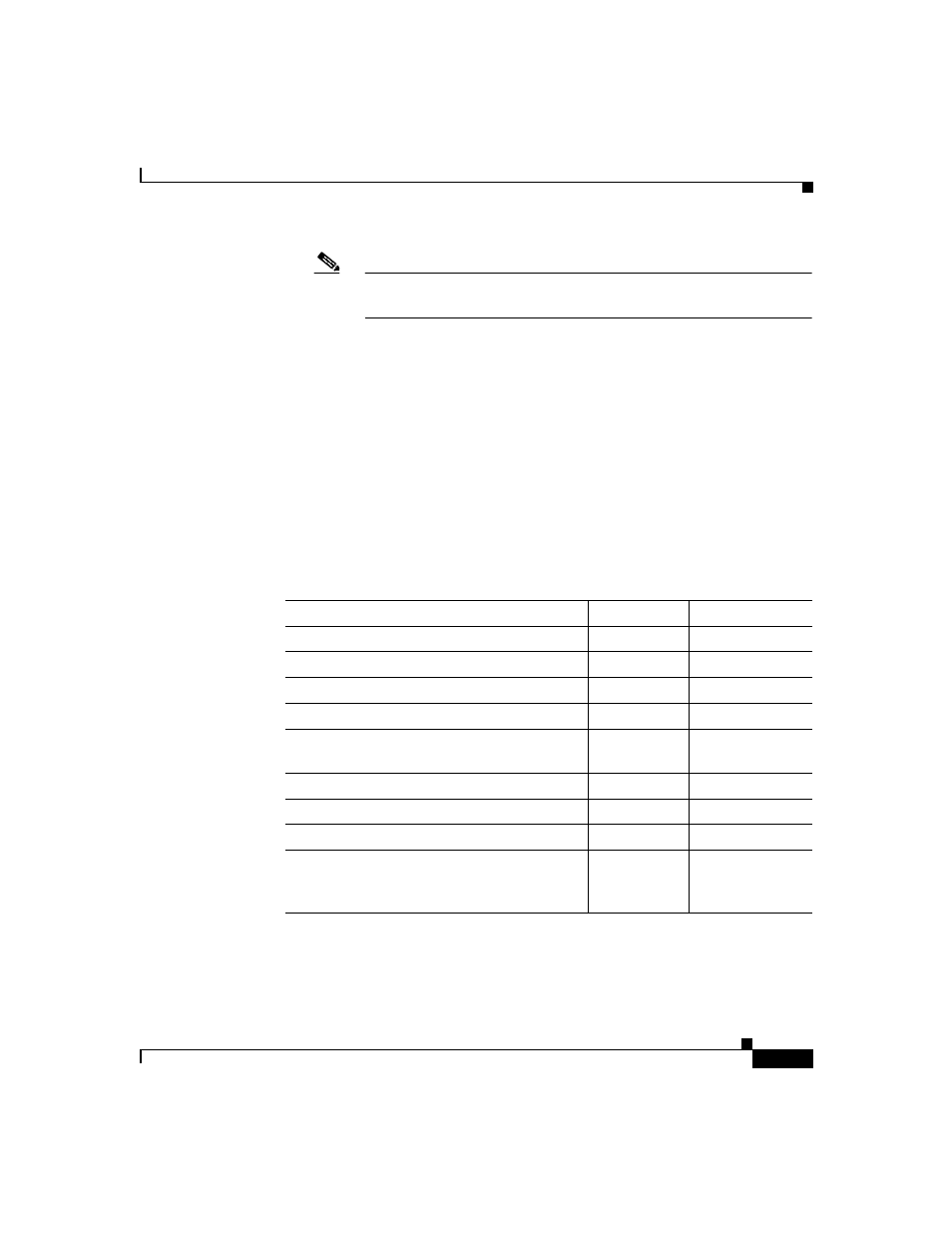
lists the ports that Cisco Secure ACS listens to for communications with
AAA clients, other Cisco Secure ACSes and applications, and web browsers.
Cisco Secure ACS uses other ports to communicate with external user databases;
however, it initiates those communications rather than listening to specific ports.
In some cases, these ports are configurable, such as with LDAP and RADIUS
token server databases. For more information about ports that a particular external
user database listens to, see the documentation for that database.
Table 2-1
Ports that Cisco Secure ACS Listens To
Feature/Protocol
UDP or TCP?
Ports
RADIUS authentication and authorization
UDP
1645, 1812
RADIUS accounting
UDP
1646, 1813
TACACS+
TCP
49
CiscoSecure Database Replication
TCP
2000
RDBMS Synchronization with
synchronization partners
TCP
2000
User-Changeable Password web application
TCP
2000
Logging
TCP
2001
Administrative HTTP port for new sessions
TCP
2002
Administrative HTTP port range
TCP
Configurable;
default 1024
through 65535
