The ciscosecure acs paradigm, The cisco secure acs paradigm – Cisco 3.3 User Manual
Page 42
Chapter 1 Overview
The Cisco Secure ACS Paradigm
1-2
User Guide for Cisco Secure ACS for Windows Server
78-16592-01
–
Accessing the HTML Interface, page 1-32
–
Logging Off the HTML Interface, page 1-33
–
Online Help and Online Documentation, page 1-33
The Cisco Secure ACS Paradigm
Cisco Secure ACS provides authentication, authorization, and accounting
(AAA—pronounced “triple A”) services to network devices that function as AAA
clients, such as a network access server, PIX Firewall, or router. The AAA client
in
represents any such device that provides AAA client functionality
and uses one of the AAA protocols supported by Cisco Secure ACS.
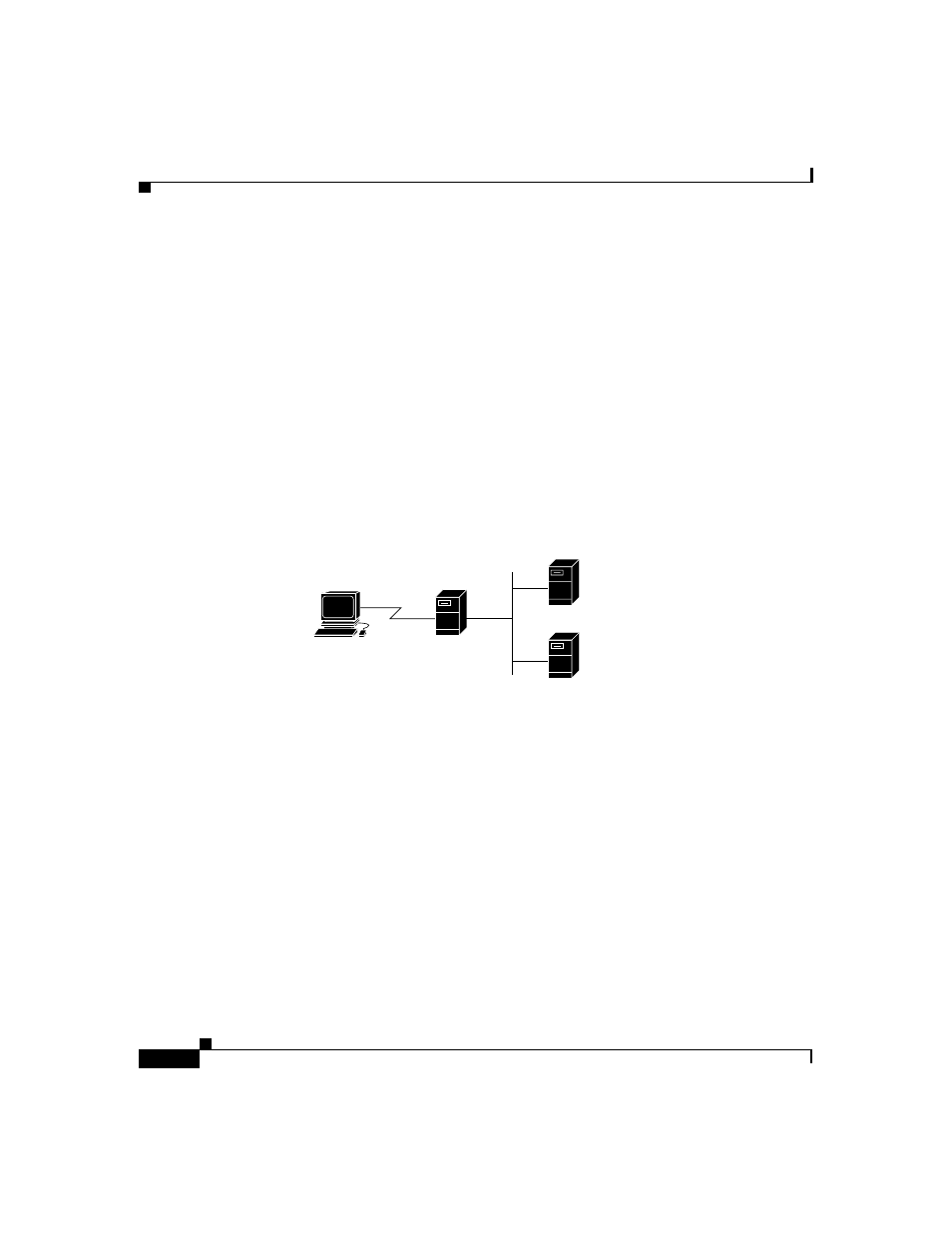
Figure 1-1
A Simple AAA Scenario
Cisco Secure ACS centralizes access control and accounting, in addition to router
and switch access management. With Cisco Secure ACS, network administrators
can quickly administer accounts and globally change levels of service offerings
for entire groups of users. Although the external user database shown in
is optional, support for many popular user repository implementations
enables companies to put to use the working knowledge gained from and the
investment already made in building their corporate user repositories.
Cisco Secure ACS supports Cisco AAA clients such as the Cisco 2509, 2511,
3620, 3640, AS5200 and AS5300, AS5800, the Cisco PIX Firewall, Cisco
Aironet Access Point wireless networking devices, Cisco VPN 3000
Concentrators, and Cisco VPN 5000 Concentrators. It also supports third-party
devices that can be configured with the Terminal Access Controller Access
Control System (TACACS+) or the Remote Access Dial-In User Service
(RADIUS) protocol. Cisco Secure ACS treats all such devices as AAA clients.
Cisco Secure ACS uses the TACACS+ and RADIUS protocols to provide AAA
67472
End-user client
AAA client
Cisco Secure
Access Control Server
External user
database
