Host information—personalities tab, Host information—security tab, 150 host information—security tab – HP SAN Virtualization Services Platform User Manual
Page 150: Host personalities tab fields, Host security tab fields
Description
Display field
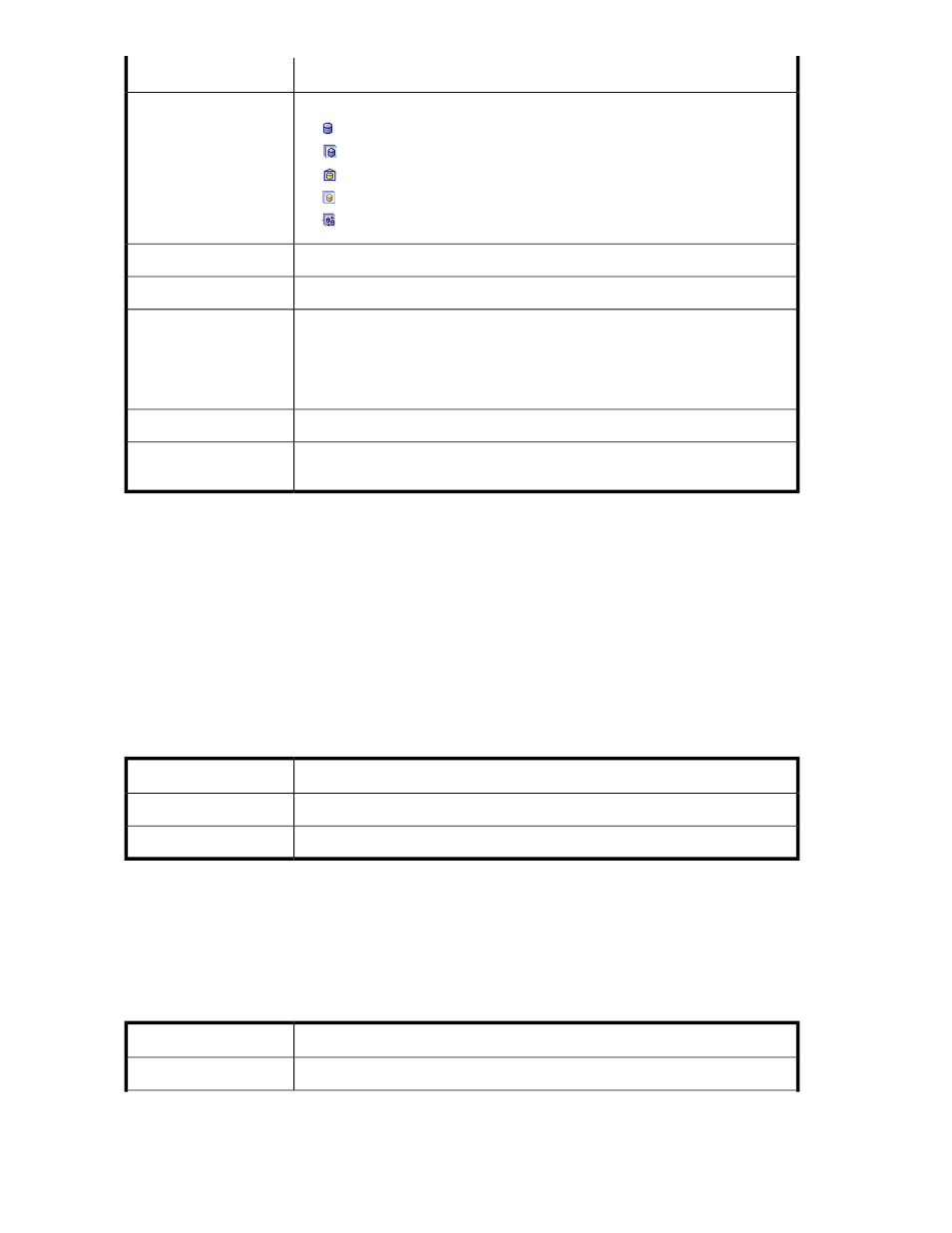
An icon representing a VSM storage element assigned to the host. Possible values:
•
—A virtual disk.
•
—A VDG.
•
—A snapshot.
•
—A VDG snapshot.
•
—A synchronous mirror group.
Type
The name of the VSM storage element.
Name
The status of the VSM storage element.
Status
Yes indicates that the virtual disk or VDG is defined as a cluster resource. This
setting tunes the SVSP system behavior when the virtual disk is permitted to multiple
hosts (configured as a resource in a cluster application). For a description of
configuring virtual disks for cluster applications, see “
Clustered
The type of permission the host has to access the element.
Permission
The LUN by which the element is presented to the host. Relevant only for UDH
hosts.
LUN
Host information—Personalities tab
The Personalities tab displays the SCSI personality that was set for the selected host, if applicable.
SCSI personality is only relevant for UDH hosts. The personality defines the way in which the DPM
presents virtual disks (LUNs) to the host. The DPM supports different personalities for different host
operating systems. The combination of operating system–specific multipath software running on the
host and the matching personality enable features such as failover and failback between DPMs.
The personality of a host is defined upon host creation. You can change the personality of a UDH.
For information about changing a UDH’s personality, see
“
Changing the UDH operating system or personality
Table 61 Host Personalities tab fields
Description
Property
The row number.
No
The personality of the host.
Personality
Host information—Security tab
The Security tab displays the access permissions of users and user groups for the selected host. For
information about configuring permissions, see
“
Configuring security permissions for entities
Table 62 Host Security tab fields
Description
Display field
The row number.
No
Working with hosts
150
