Policing, Marking and discarding with a policer, Figure 14-4 – Cisco 15327 User Manual
Page 213
14-5
Ethernet Card Software Feature and Configuration Guide, R7.2
Chapter 14 Configuring Quality of Service
Policing
Policing
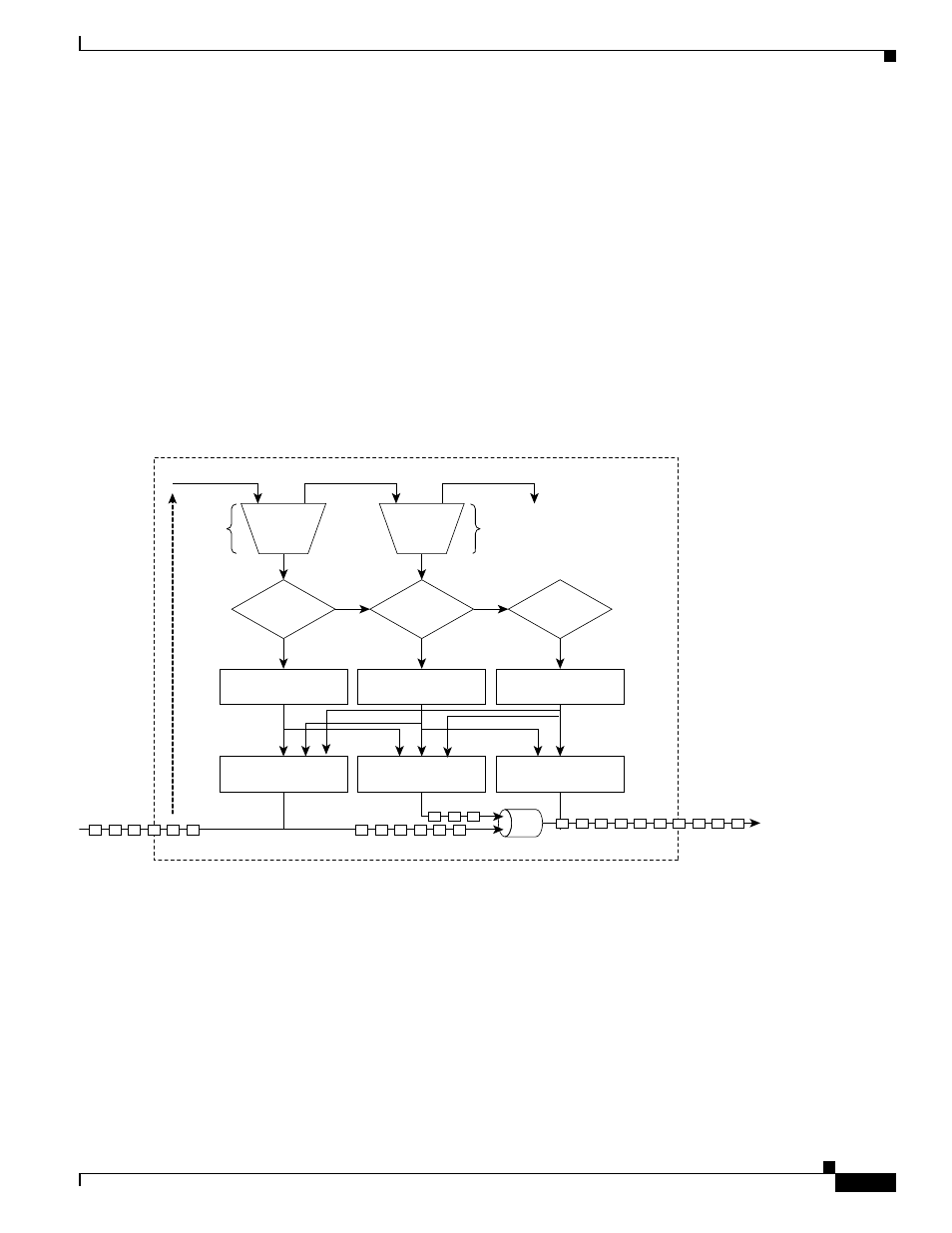
Dual leaky bucket policer is a process where the first bucket (CIR bucket) is filled with tokens at a known
rate (CIR), which is a parameter that can be configured by the operator.
illustrates the dual
leaky bucket policer model. The tokens fill the bucket up to a maximum level, which is the amount of
burstable committed (BC) traffic on the policer. The nonconforming packets of the first bucket are the
overflow packets, which are passed to the second leaky bucket (the PIR bucket). The second leaky bucket
is filled with these tokens at a known rate (PIR), which is a parameter that can be configured by the
operator. The tokens fill the PIR bucket up to a maximum level (BP), which is the amount of peak
burstable traffic on the policer. The nonconform packets of the second bucket are the overflow packets,
which can be dropped or marked according to the policer definition.
On the dual leaky bucket policer, the packets conforming to the CIR are conform packets, the packets
not conforming to CIR but conforming to PIR are exceed packets, and the packets not conforming to
either the PIR or CIR are violate packets.
Figure 14-4
Dual Leaky Bucket Policer Model
Marking and Discarding with a Policer
On the ML-Series card’s policer, the conform packets can be transmitted or marked and transmitted. The
exceed packets can be transmitted, marked and transmitted, or dropped. The violating packets can be
transmitted, marked and transmitted, or dropped. The primary application of the dual-rate or three-color
policer is to mark the conform packets with CoS bit 2l, mark the exceed packet with CoS bit 1, and
discard the violated packets so all the subsequent network devices can implement the proper QoS
treatment per frame/packet basis based on these priority marking without knowledge of each SLA.
96497
Tokens
Ingress
Packets
Queued
Packets
Bc
OverflowTokens
Conform
OverflowTokens
Size Transmit Yes No Bp Exceed Size>=Tc+Tp Remark Set DE bit Yes No Violate Size>=Tc+Tp Drop Yes
