Protecting volumes from erroneous copy operations – HP XP P9500 Storage User Manual
Page 143
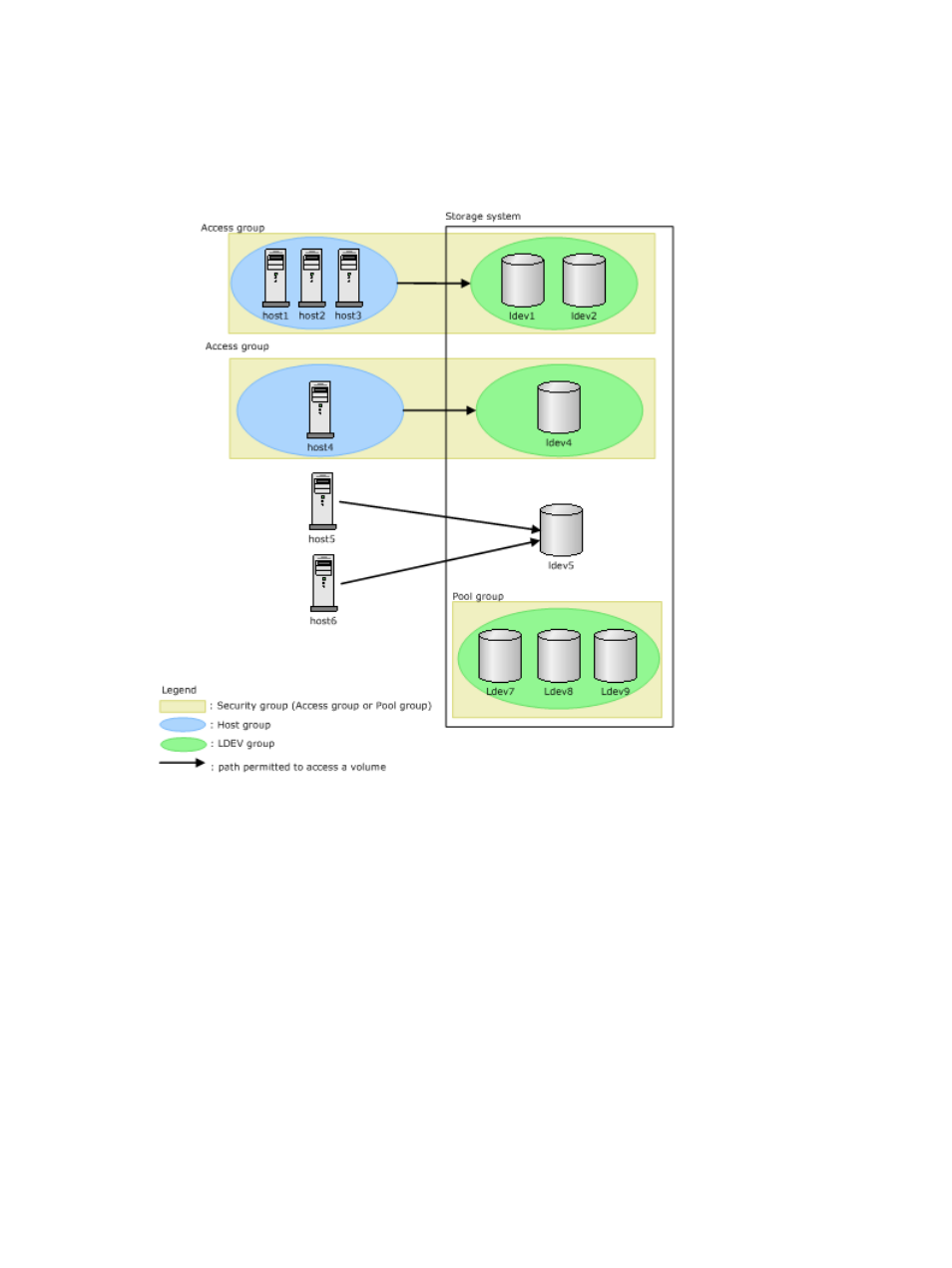
volumes (vol_A and vol_B) in a pool group, all the mainframe hosts connected to your storage
system will be unable to access vol_A and vol_B. To register volumes in a pool group, you must
create an LDEV group, register the volumes in the LDEV group, and then register the LDEV group
in the desired pool group. A pool group may contain only one LDEV group.
In the next figure, volumes ldev7, ldev8, and ldev9 in the pool group are inaccessible from all
hosts:
Protecting Volumes from Erroneous Copy Operations
When P9500 copy software (Continuous Access Synchronous Z (Cnt Ac-S Z), Continuous Access
Journal Z (Cnt Ac-J Z), Business Copy for Mainframe (BC Z), Compatible FlashCopy, or FICON(R)
Data Migration is used to perform copy operations, data is overwritten on the secondary volumes
, the copy destination volumes. If a volume that contains important data is specified as a secondary
volume by mistake, P9500 copy software operations could overwrite important data on the volume,
causing data loss.
With Volume Security for Mainframe you can prevent a volume from being used as a secondary
volume to avoid data loss.
Secondary volumes, referred to as Continuous Access Synchronous remote volumes or R-VOLs
Business Copy target volumes or T-VOLs See P9000 Continuous Access Synchronous for Mainframe
Systems User Guide and P9000 Business Copy for Mainframe Systems User Guide.
Protecting Volumes from I/O Operations at Mainframe Hosts
143
