Port-level security, Port-level security implementation – HP XP P9500 Storage User Manual
Page 141
Port-Level Security
Usually, hosts are connected to two or more ports with cables and have access to volumes through
these ports. In the security example shown in the previous figure, hosts can access volumes in their
access group through any port connected to the hosts.
With the Volume Security Port Security Option for Mainframe you can permit or prohibit hosts from
accessing volumes through specified ports. For example, if host1 is connected to port1 and port2,
you can permit host1 to access volumes through port1 and prohibit host1 from accessing volumes
though port2.
Port-Level Security Implementation
To implement port-level security, you must determine the ports that can be used by hosts to access
volumes and register ports in host groups. For example, you could register host1 and port1 in a
host group called hg1. If you then register hg1 in an access group, host1 could access volumes
through port1 but not through port2.
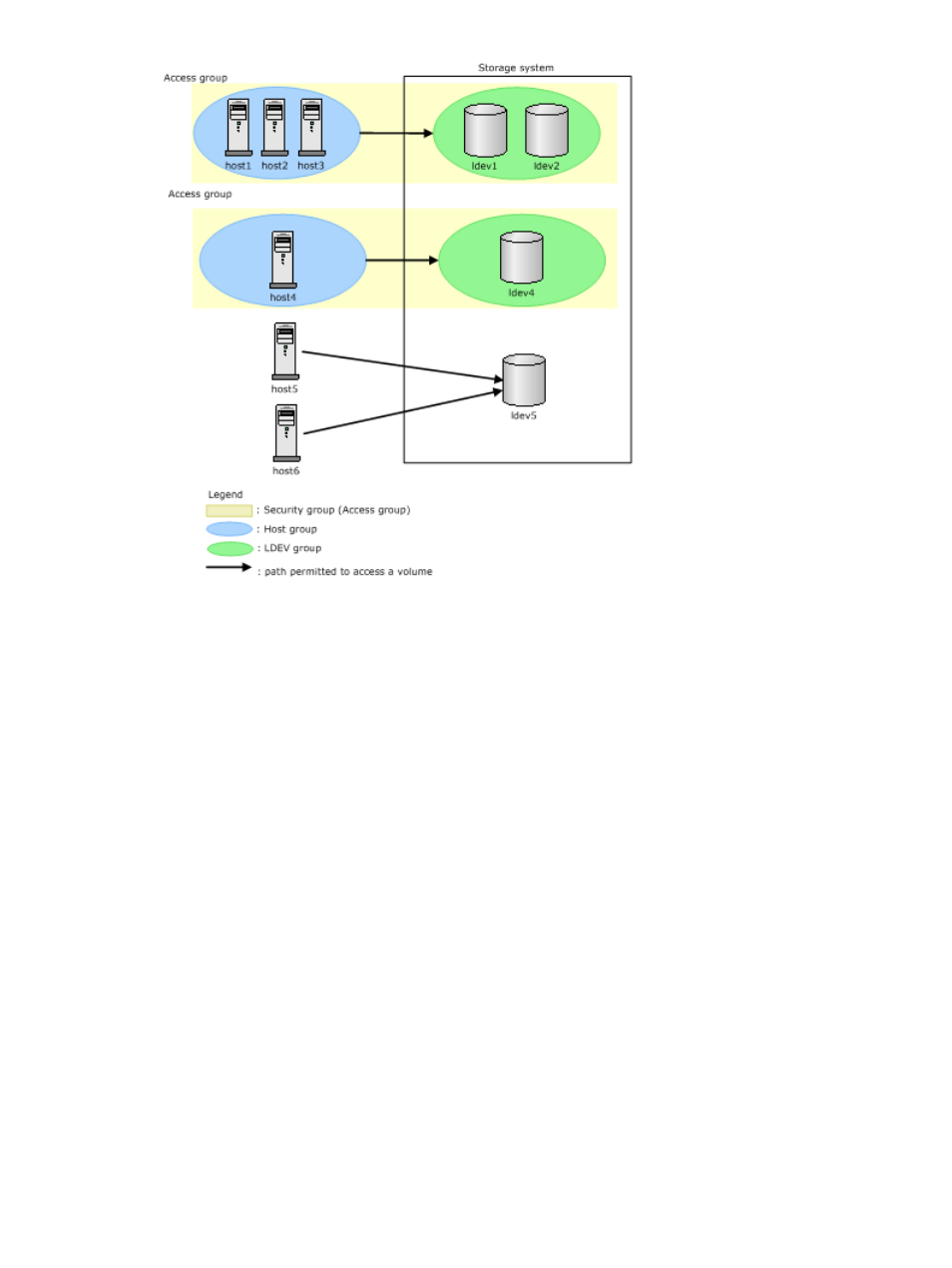
In next figure, the following security settings are applied:
•
The hosts host1, host2, and host3 can access volumes ldev1 and ldev2 through port1, port2,
and port3. However, the hosts cannot access the volumes through other ports.
•
The host host4 can access the volume ldev4 through port4. However, the host cannot access
the volume through other ports.
Protecting Volumes from I/O Operations at Mainframe Hosts
141
