9 port isolation – Interlogix NS3502-8P-2S User Manual User Manual
Page 129
IFS NS3502-8P-2S User Manual
129
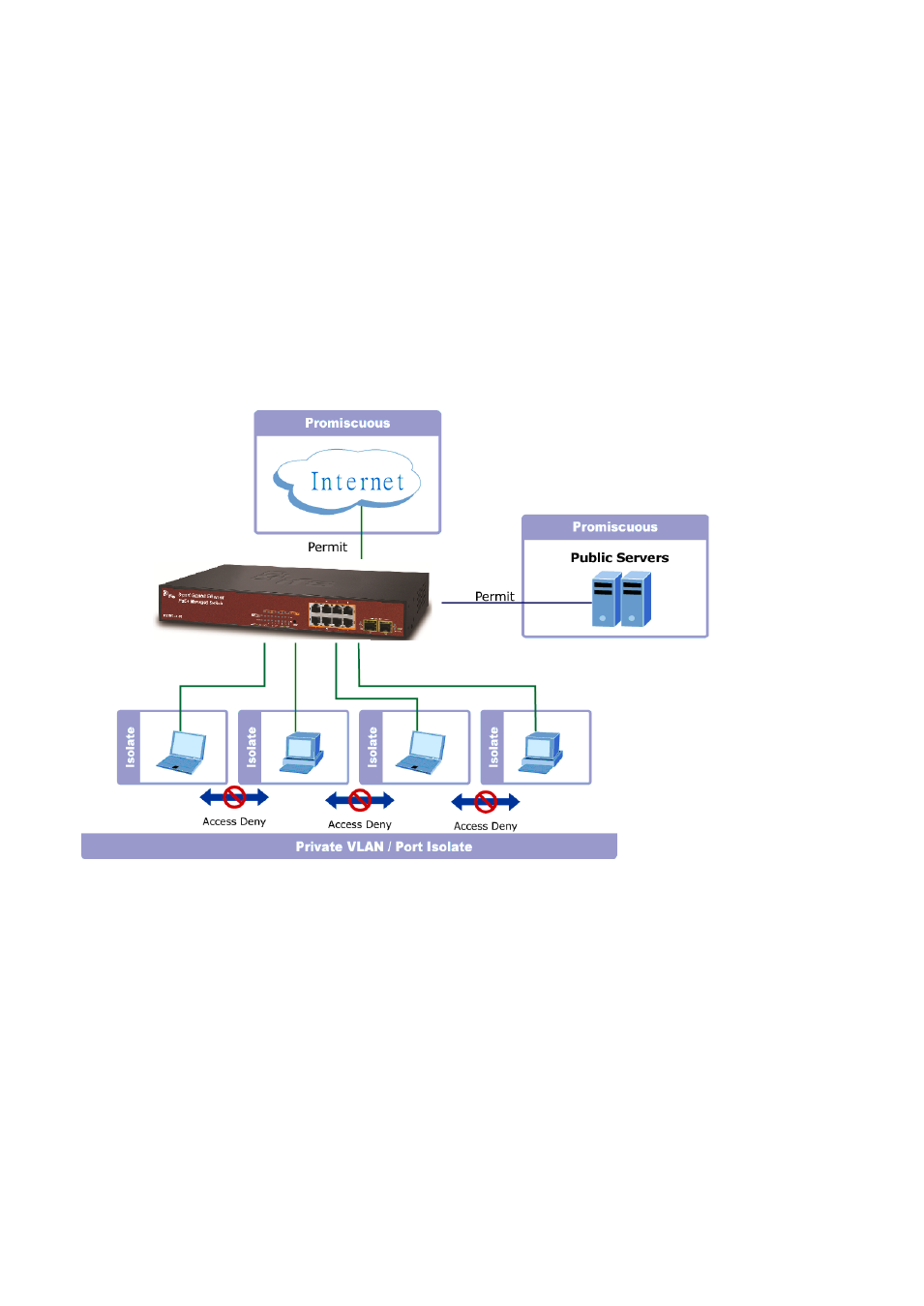
4.6.9 Port Isolation
Overview
When a VLAN is configured to be a private VLAN, communication between ports within that VLAN can
be prevented. Two application examples are provided in this section:
• Customers connected to an ISP can be members of the same VLAN, but they are not allowed to
communicate with each other within that VLAN.
• Servers in a farm of web servers in a Demilitarized Zone (DMZ) are allowed to communicate with
the outside world and with database servers on the inside segment, but are not allowed to
communicate with each other
For private VLANs to be applied, the switch must first be configured for standard VLAN operation when
this is in place, one or more of the configured VLANs can be configured as private VLANs. Ports in a
private VLAN fall into one of these two groups:
Promiscuous ports
— Ports from which traffic can be forwarded to all ports in the private VLAN
— Ports which can receive traffic from all ports in the private VLAN
Isolated ports
— Ports from which traffic can only be forwarded to promiscuous ports in the private VLAN
— Ports which can receive traffic from only promiscuous ports in the private VLAN
The configuration of promiscuous and isolated ports applies to all private VLANs. When traffic comes in
on a promiscuous port in a private VLAN, the VLAN mask from the VLAN table is applied. When traffic
comes in on an isolated port, the private VLAN mask is applied in addition to the VLAN mask from the
