Chapter 19 arp guard configuration, 1 introduction to arp guard, Ntroduction to – QTECH QSW-8300 Инструкция по настройке User Manual
Page 151: Guard
+7(495) 797-3311 www.qtech.ru
Москва, Новозаводская ул., 18, стр. 1
150
Chapter 19 ARP GUARD Configuration
19.1 Introduction to ARP GUARD
There is serious security vulnerability in the design of ARP protocol, which is any network
device, can send ARP messages to advertise the mapping relationship between IP address
and MAC address. This provides a chance for ARP cheating. Attackers can send ARP
REQUEST messages or ARP REPLY messages to advertise a wrong mapping relationship
between IP address and MAC address, causing problems in network communication. The
danger of ARP cheating has two forms: 1. PC4 sends an ARP message to advertise that the IP
address of PC2 is mapped to the MAC address of PC4, which will cause all the IP messages
to PC2 will be sent to PC4, thus PC4 will be able to monitor and capture the messages to PC2;
2. PC4 sends ARP messages to advertise that the IP address of PC2 is mapped to an illegal
MAC address, which will prevent PC2 from receiving the messages to it. Particularly, if the
attacker pretends to be the gateway and do ARP cheating, the whole network will be collapsed.
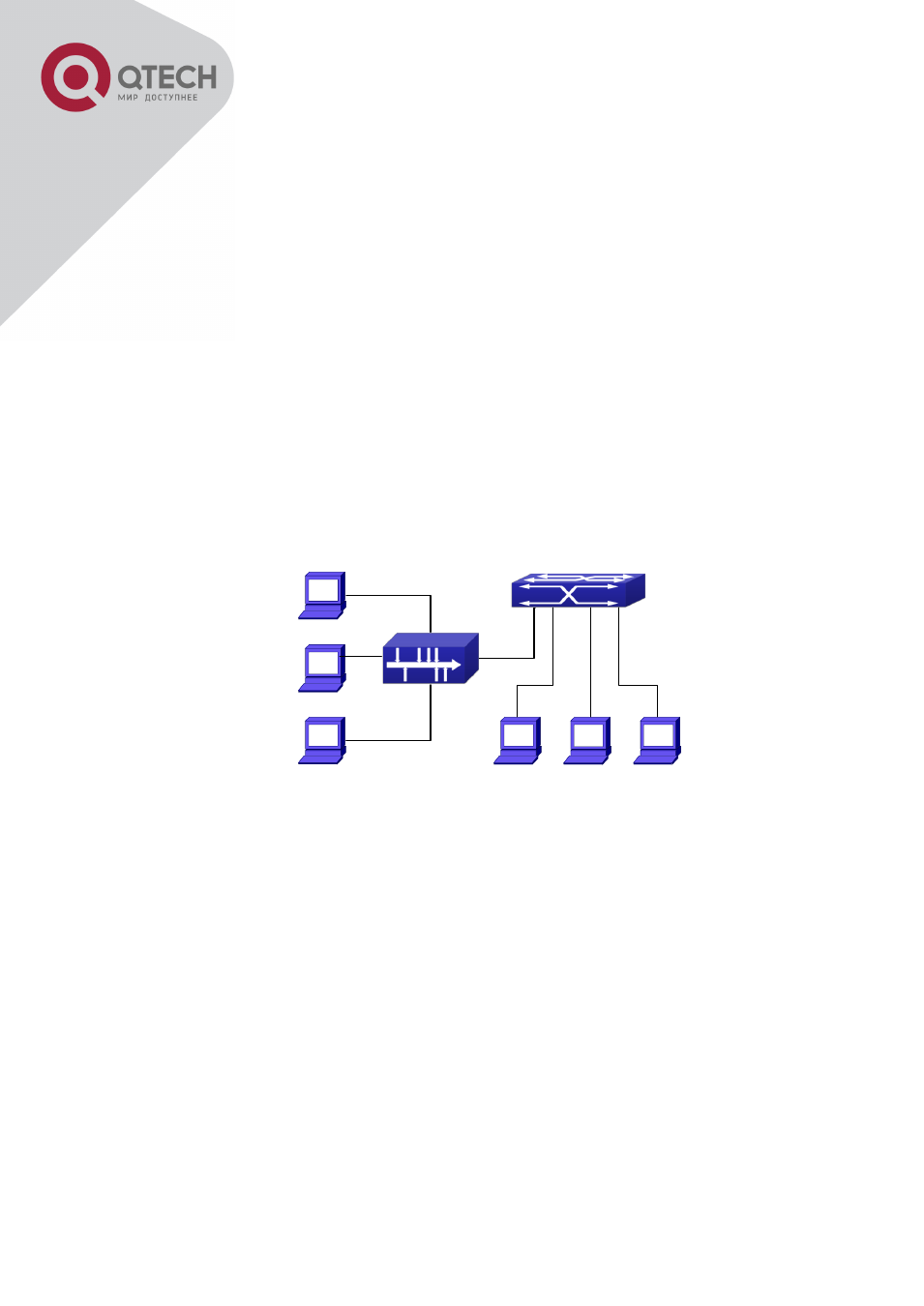
ARP GUARD schematic diagram
We utilize the filtering entries of the switch to protect the ARP entries of important network
devices from being imitated by other devices. The basic theory of doing this is that utilizing the
filtering entries of the switch to check all the ARP messages entering through the port, if the
source address of the ARP message is protected, the messages will be directly dropped and
will not be forwarded.
ARP GUARD function is usually used to protect the gateway from being attacked. If all the
accessed PCs in the network should be protected from ARP cheating, then a large number of
ARP GUARD address should be configured on the port, which will take up a big part of FFP
entries in the chip, and as a result, might affect other applications. So this will be improper. It is
recommended that adopting FREE RESOURCE related accessing scheme. Please refer to
relative documents for details.
Switch
PC1
PC2
PC3
PC4
PC5
PC6
HUB
A B C D
