Brocade FastIron Ethernet Switch Stacking Configuration Guide User Manual
Page 28
•
Authentication of secure-setup packets provides verification that these packets are from a
genuine Brocade stack unit. MD5-based port verification confirms stacking ports.
•
Superuser password is required to allow password-protected devices to become members of a
traditional stack.
•
The stack disable command. When this command is issued, a unit does not listen for or send
stacking packets, which means that no other device in the network can force the stacking-
disabled unit to join a traditional stack.
Secure-setup can also be used to add units to an existing traditional stack and to change the stack IDs
of stack members.
When secure-setup is issued on a unit that is not already the active controller, this unit becomes the
active controller. If this unit does not already have an assigned priority, secure-setup will assign this
unit a priority of 128 by default, if no other units in the stack have a priority higher than 128. If another
unit in the stack has a priority of 128 or higher, secure-setup will give the active controller a priority
equal to the highest priority unit in the stack (which is by default the standby controller). When the
active controller and the standby controller have identical priorities, during a reset, the old active
controller cannot reassume its role from the standby controller (which has become the active controller
at the reset).
If the previous active controller again becomes active, and you want it to resume the role of active
controller, you should set the priority for the standby controller to a priority lower than 128. If you do
not want the previous active controller to remain active controller, you can set the same priority for
both active and standby controllers (higher than or equal to 128).
NOTE
Secure-setup works for units within a single stack. It does not work across stacks.
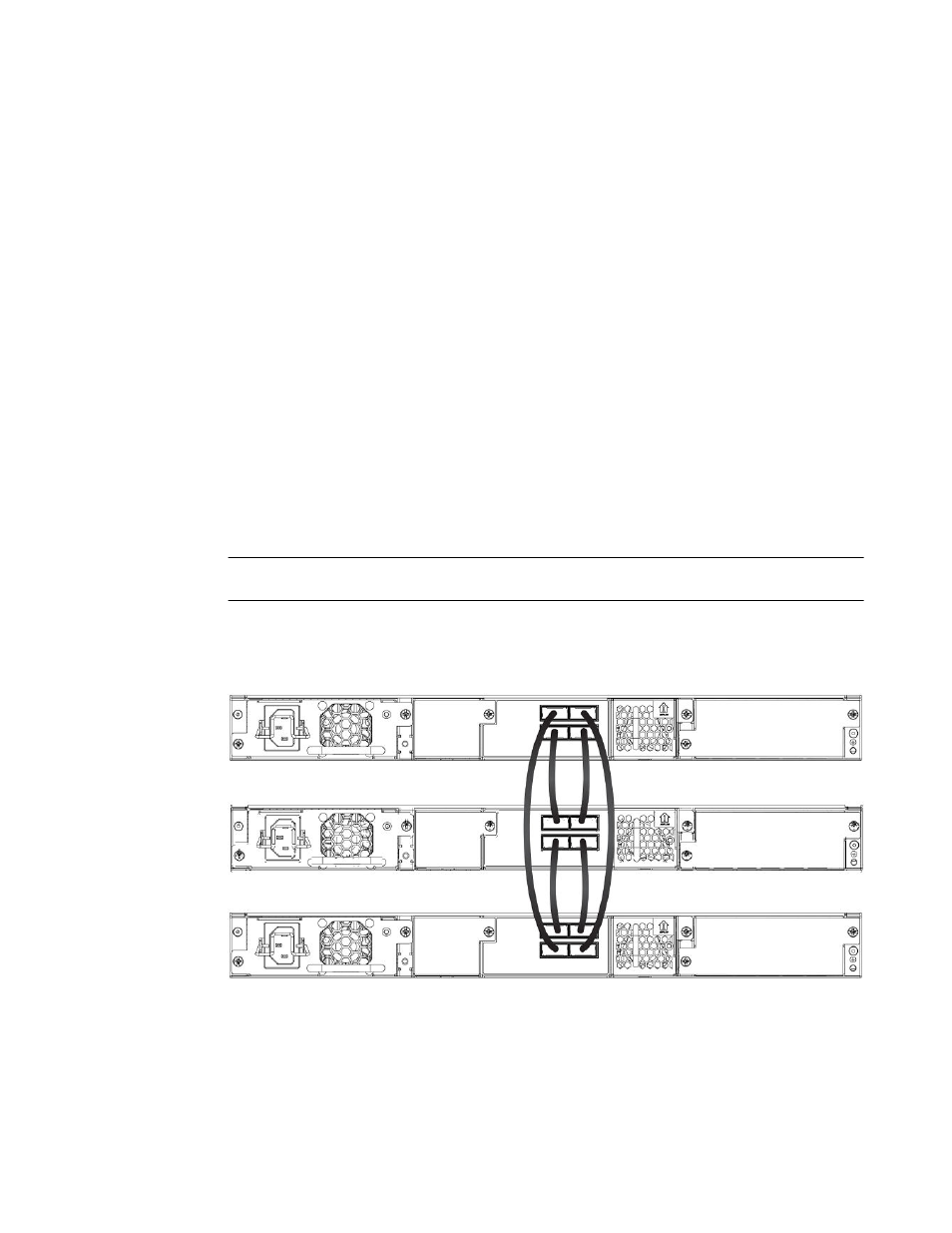
The following figure shows a traditional stack with three units in a ring topology. Refer to this figure as
you follow the procedure steps for this scenario.
FIGURE 12 Traditional stack with ring topology
Configuring a three-member traditional stack in a ring topology using secure-setup
1.
Connect the devices using the stacking ports and stack cabling. For more information, refer to the
appropriate hardware installation guides.
2.
Power on the units.
Configuring a three-member traditional stack in a ring topology using secure-setup
26
FastIron Ethernet Switch Stacking Configuration Guide
53-1003090-02
