Controlled and uncontrolled ports – Brocade Multi-Service IronWare Security Configuration Guide (Supporting R05.6.00) User Manual
Page 317
Multi-Service IronWare Security Configuration Guide
299
53-1003035-02
How 802.1x port security works
8
Supplicant PAE – The Supplicant PAE supplies information about the client to the Authenticator PAE
and responds to requests from the Authenticator PAE. The Supplicant PAE can also initiate the
authentication procedure with the Authenticator PAE, as well as send logoff messages.
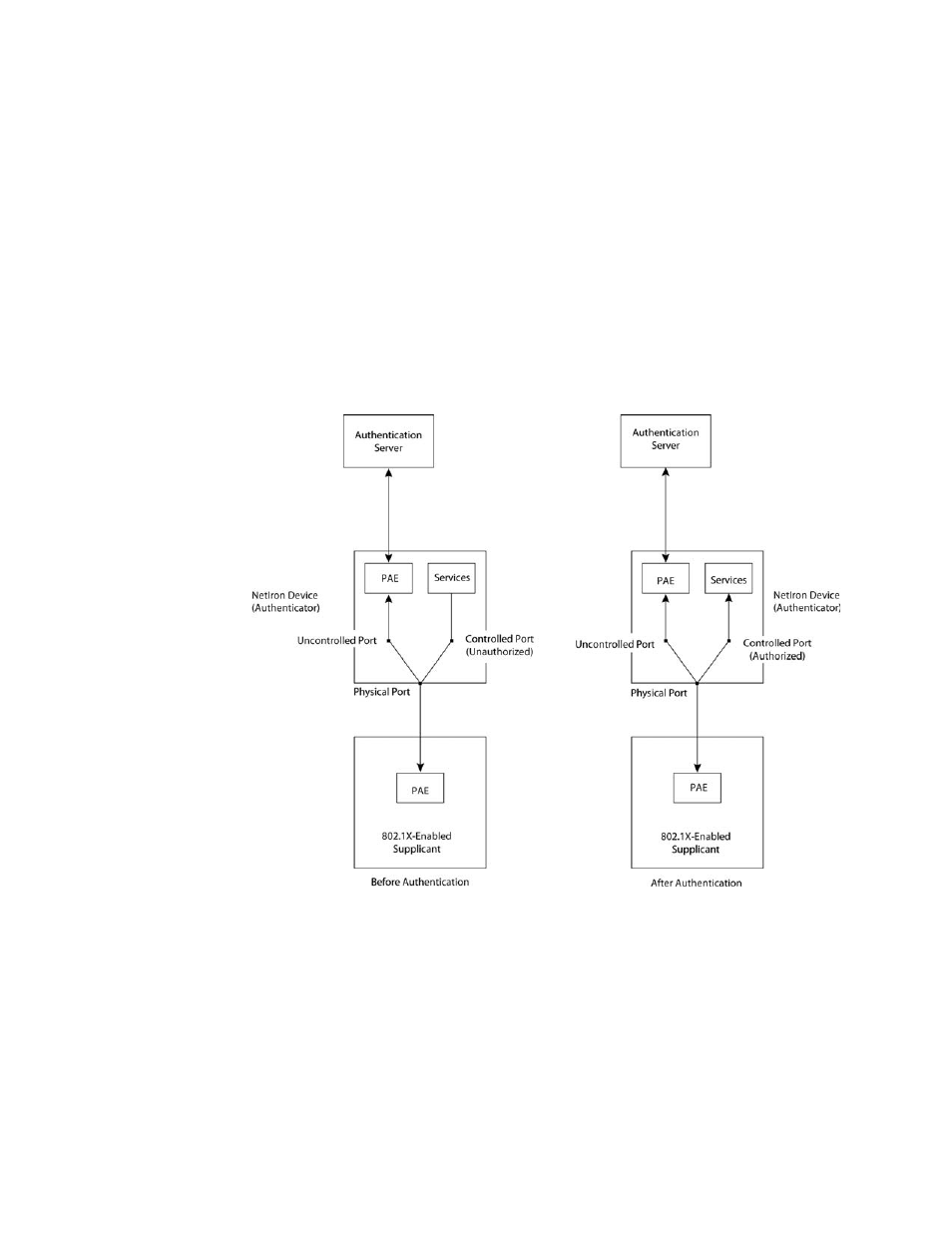
Controlled and uncontrolled ports
A physical port on the device used with 802.1x port security has two virtual access points: a
controlled port and an uncontrolled port. The controlled port provides full access to the network.
The uncontrolled port provides access only for EAPOL traffic between the client and the
Authentication Server. When a client is successfully authenticated, the controlled port is opened to
the client.
illustrates this concept.
FIGURE 4
Controlled and uncontrolled ports before and after client authentication
Before a client is authenticated, only the uncontrolled port on the Authenticator is open. The
uncontrolled port allows only EAPOL frames to be exchanged between the client and the
Authentication Server. The controlled port is in the unauthorized state and allows no traffic to pass
through.
During authentication, EAPOL messages are exchanged between the Supplicant PAE and the
Authenticator PAE, and RADIUS messages are exchanged between the Authenticator PAE and the
Authentication Server. Refer to
“Message exchange during authentication”
for an example of this
process. If the client is successfully authenticated, the controlled port becomes authorized, and
traffic from the client can flow through the port normally.
