How 802.1x port security works, Device roles in an 802.1x configuration – Brocade Multi-Service IronWare Security Configuration Guide (Supporting R05.6.00) User Manual
Page 315
Multi-Service IronWare Security Configuration Guide
297
53-1003035-02
How 802.1x port security works
8
How 802.1x port security works
This section explains the basic concepts behind 802.1x port security, including device roles, how
the devices communicate, and the procedure used for authenticating clients.
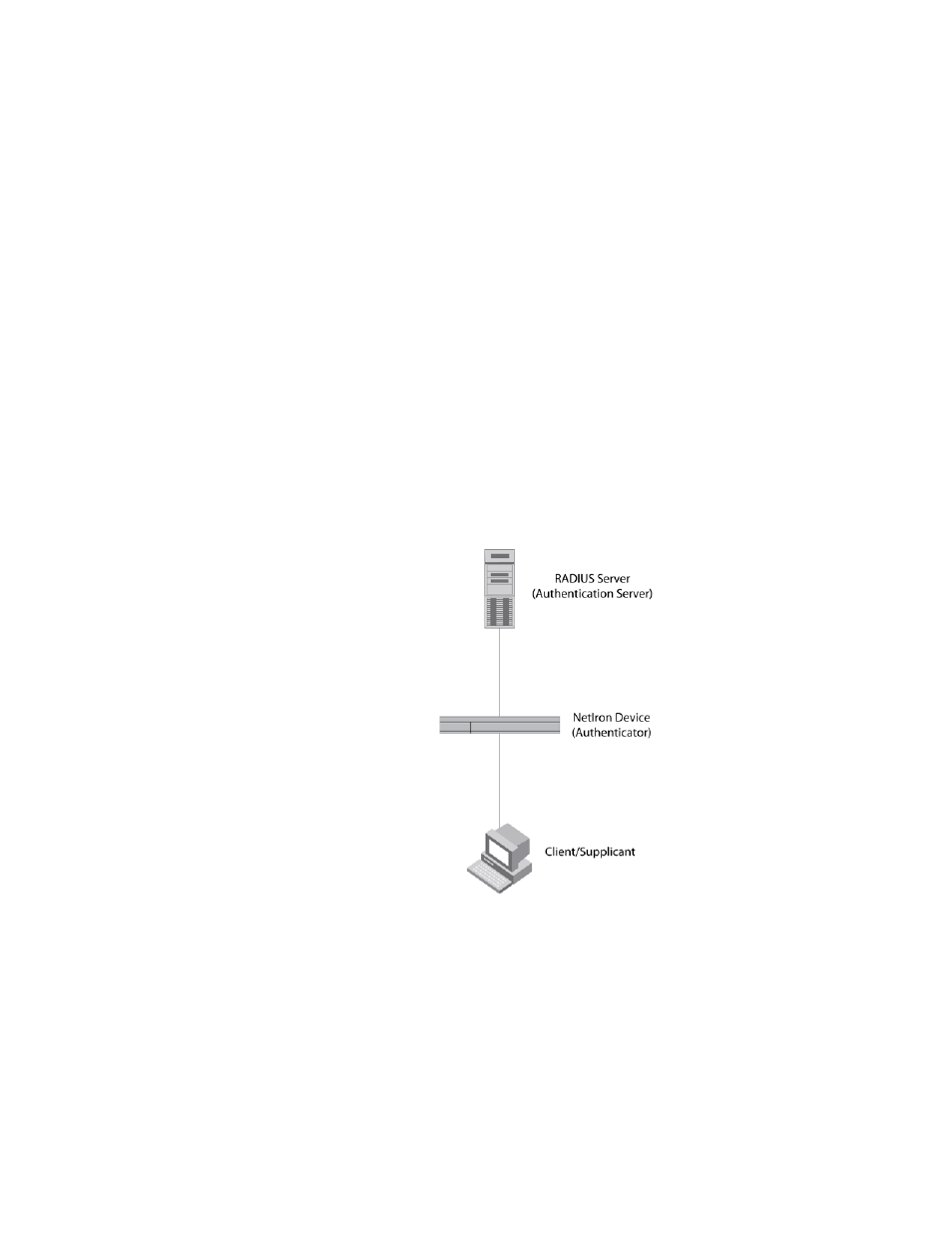
Device roles in an 802.1x configuration
The 802.1x standard defines the roles of client or Supplicant, Authenticator, and Authentication
Server in a network.
The client (known as a Supplicant in the 802.1x standard) provides username or password
information to the Authenticator. The Authenticator sends this information to the Authentication
Server. Based on the client's information, the Authentication Server determines whether the client
can use services provided by the Authenticator. The Authentication Server passes this information
to the Authenticator, which then provides services to the client, based on the authentication result.
illustrates these roles.
FIGURE 2
Authenticator, client or supplicant, and authentication server in an 802.1x
configuration
Authenticator – The device that controls access to the network. In an 802.1x configuration, the
device serves as the Authenticator. The Authenticator passes messages between the client and the
Authentication Server. Based on the identity information supplied by the client, and the
authentication information supplied by the Authentication Server, the Authenticator either grants or
does not grant network access to the client.
client or supplicant – The device that seeks to gain access to the network. clients must be running
software that supports the 802.1x standard (for example, the Windows XP operating system).
clients can either be directly connected to a port on the Authenticator, or can be connected by way
of a hub.
