Configuring command authorization – Brocade FastIron Ethernet Switch Security Configuration Guide User Manual
Page 70
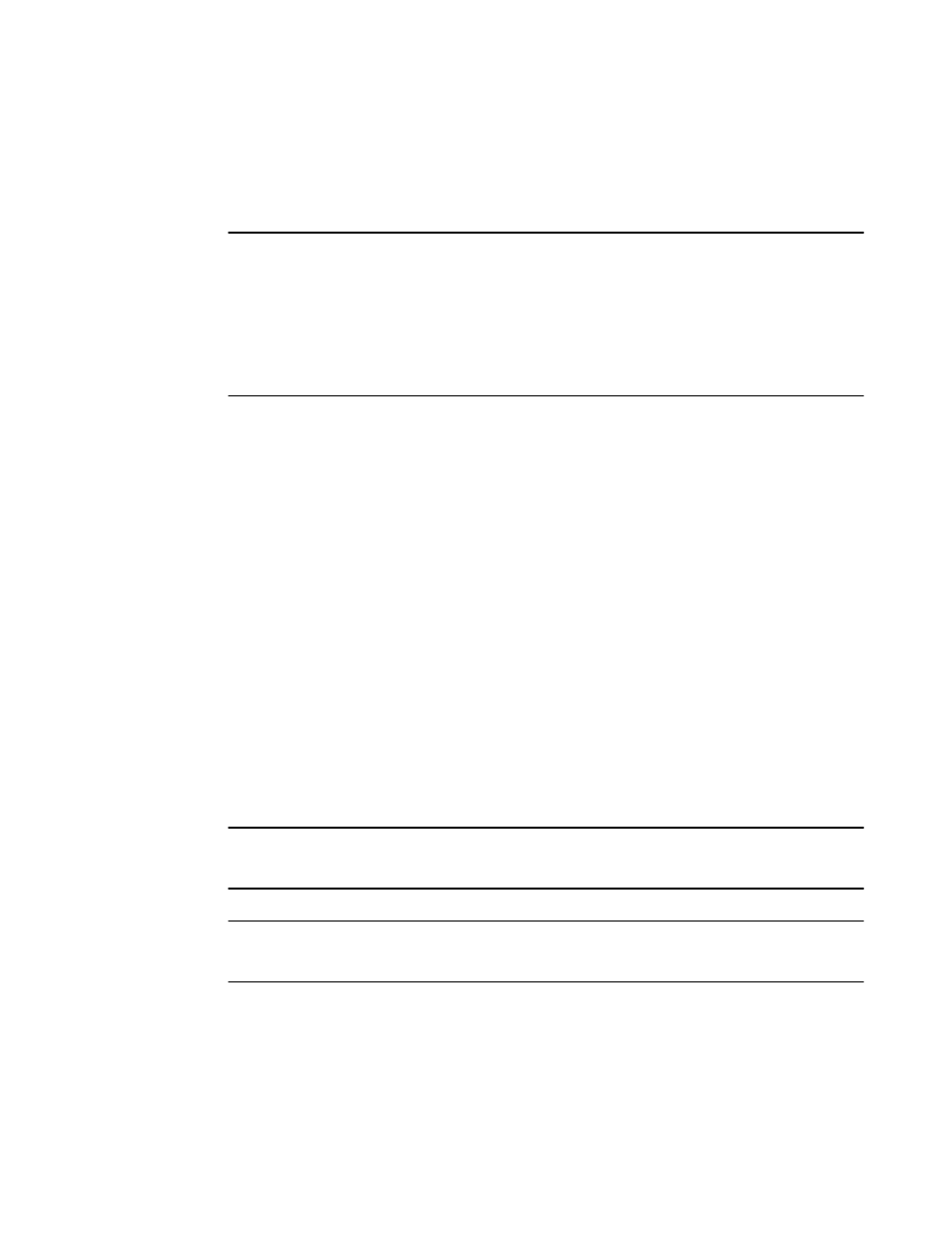
Syntax: aaa authorization exec default [ radius | none ]
If you specify none , or omit the aaa authorization exec command from the device configuration, no
exec authorization is performed.
NOTE
If the aaa authorization exec default radius command exists in the configuration, following
successful authentication the device assigns the user the privilege level specified by the foundry-
privilege-level attribute received from the RADIUS server. If the aaa authorization exec default
radius command does not exist in the configuration, then the value in the foundry-privilege-level
attribute is ignored, and the user is granted Super User access.Also note that in order for the aaa
authorization exec default radius command to work, either theaaa authentication enable default
radius command, or the aaa authentication login privilege-mode command must also exist in the
configuration.
Configuring command authorization
When RADIUS command authorization is enabled, the Brocade device consults the list of commands
supplied by the RADIUS server during authentication to determine whether a user can issue a
command he or she has entered.
You enable RADIUS command authorization by specifying a privilege level whose commands require
authorization. For example, to configure the Brocade device to perform authorization for the
commands available at the Super User privilege level (that is; all commands on the device), enter the
following command.
device(config)#aaa authorization commands 0 default radius
Syntax: aaa authorization commands privilege-level default [ tacacs+ | radius | none ]
The privilege-level parameter can be one of the following:
• 0 - Authorization is performed (that is, the Brocade device looks at the command list) for commands
available at the Super User level (all commands)
• 4 - Authorization is performed for commands available at the Port Configuration level (port-config
and read-only commands)
• 5 - Authorization is performed for commands available at the Read Only level (read-only
commands)
NOTE
RADIUS command authorization can be performed only for commands entered from Telnet or SSH
sessions, or from the console.
NOTE
Since RADIUS command authorization relies on the command list supplied by the RADIUS server
during authentication, you cannot perform RADIUS authorization without RADIUS authentication.
Configuring command authorization
70
FastIron Ethernet Switch Security Configuration Guide
53-1003088-03
