Brocade FastIron Ethernet Switch Security Configuration Guide User Manual
Page 189
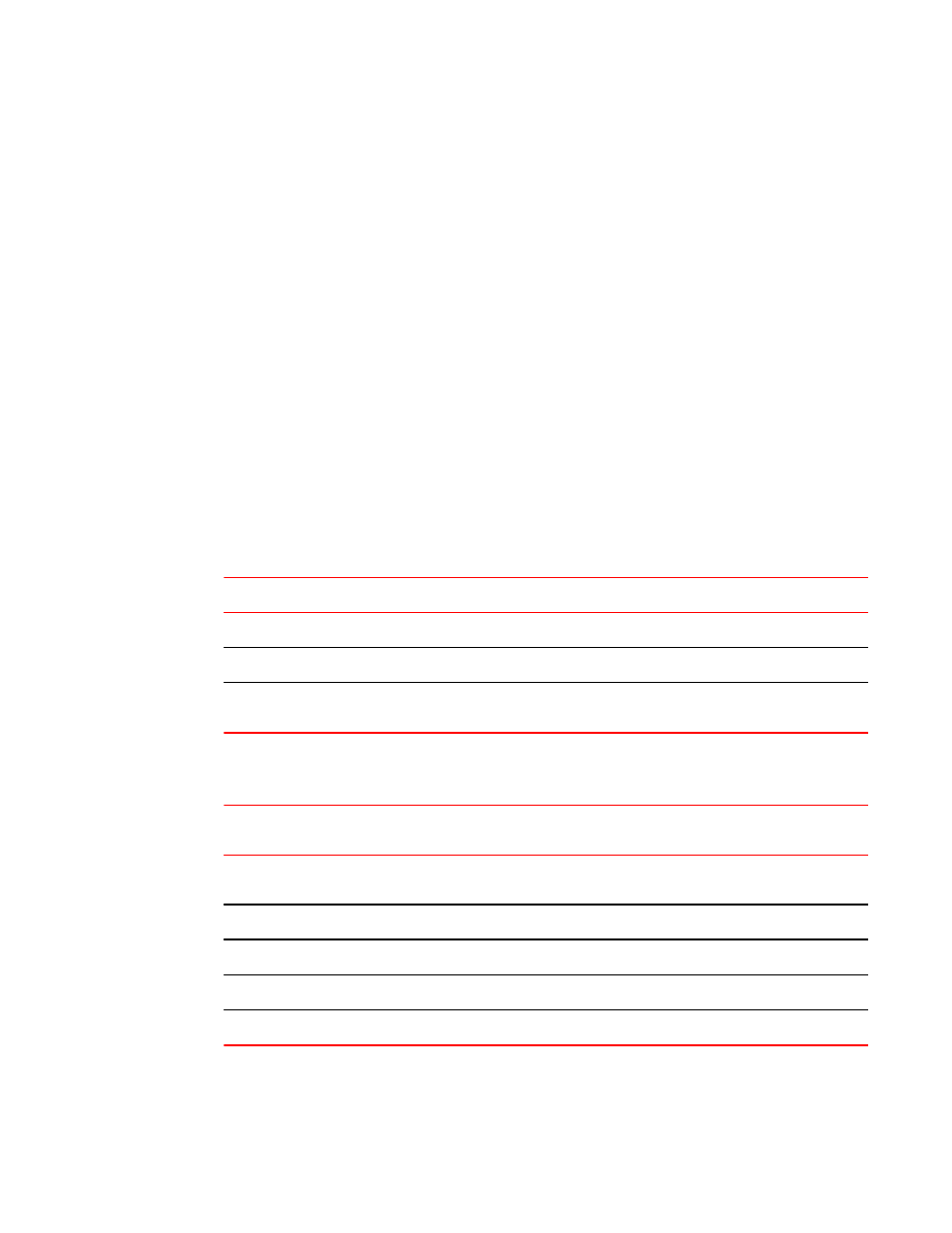
Syntax: [no] global-filter-strict-security
To disable strict security mode for a specific interface, enter commands such as the following.
device(config)#interface e 1
device(config-if-e1000-1)#dot1x disable-filter-strict-security
To re-enable strict security mode for an interface, enter the following command.
device(config-if-e1000-1)#no dot1x disable-filter-strict-security
Syntax: [no] dot1x disable-filter-strict-security
The output of the show dot1x and show dot1x config commands has been enhanced to indicate
whether strict security mode is enabled or disabled globally and on an interface. Refer to
status of strict security mode
on page 208.
Dynamically applying existing ACLs or MAC address filters
When a port is authenticated using 802.1X security, an IP ACL or MAC address filter that exists in the
running-config on the Brocade device can be dynamically applied to the port. To do this, you configure
the Filter-ID (type 11) attribute on the RADIUS server. The Filter-ID attribute specifies the name or
number of the Brocade IP ACL or MAC address filter.
The following is the syntax for configuring the Filter-ID attribute to refer to a Brocade IP ACL or MAC
address filter.
Value
Description
ip.number .in
Applies the specified numbered ACL to the 802.1X authenticated port in the inbound direction.
ip.name .in
Applies the specified named ACL to the 802.1X authenticated port in the inbound direction.
mac.number .in Applies the specified numbered MAC address filter to the 802.1X authenticated port in the
inbound direction.
The following table lists examples of values you can assign to the Filter-ID attribute on the RADIUS
server to refer to IP ACLs and MAC address filters configured on a Brocade device.
Possible values for the filter ID
attribute on the RADIUS server
ACL or MAC address filter configured on the Brocade device
ip.2.in
access-list 2 permit host 10.48.0.3access-list 2 permit 10.0.0.0
0.255.255.255
ip.102.in
access-list 102 permit ip 10.0.0.0 0.255.255.255 any
ip.fdry_filter.in
ip access-list standard fdry_filter permit host 10.48.0.3
mac.2.in
mac filter 2 permit 3333.3333.3333 ffff.ffff.ffff any
mac.3.in
mac filter 3 permit 2222.2222.2222 ffff.ffff.ffff any
Dynamically applying existing ACLs or MAC address filters
FastIron Ethernet Switch Security Configuration Guide
189
53-1003088-03
