How dhcp snooping works, Dhcp binding database – Brocade FastIron Ethernet Switch Security Configuration Guide User Manual
Page 337
other users. DHCP snooping can also stop unauthorized DHCP servers and prevent errors due to user
mis-configuration of DHCP servers.
Often DHCP snooping is used together with Dynamic ARP Inspection and IP Source Guard.
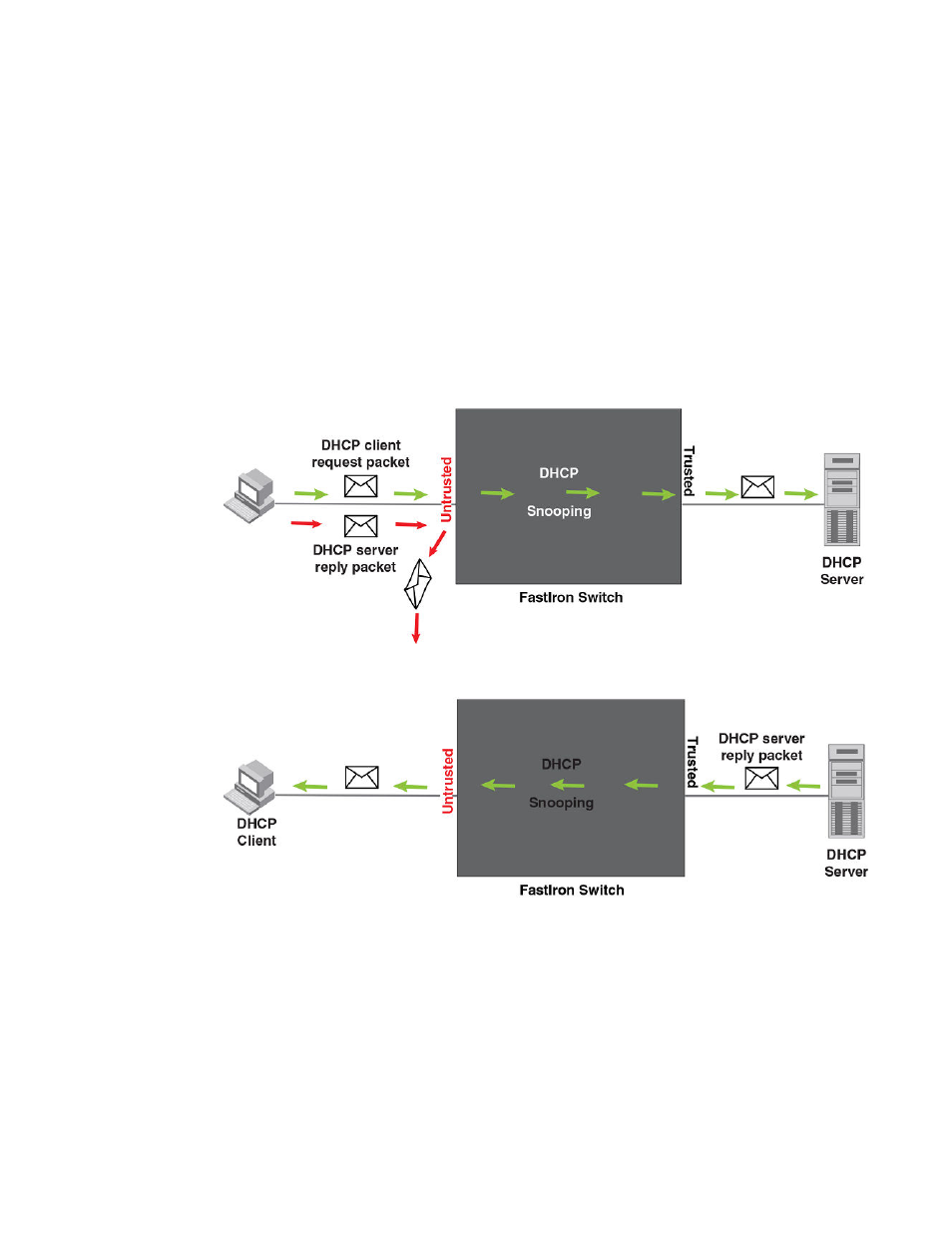
How DHCP snooping works
When enabled on a VLAN, DHCP snooping stands between untrusted ports (those connected to host
ports) and trusted ports (those connected to DHCP servers). A VLAN with DHCP snooping enabled
forwards DHCP request packets from clients and discards DHCP server reply packets on untrusted
ports, and it forwards DHCP server reply packets on trusted ports to DHCP clients, as shown in the
following figures
FIGURE 24 DHCP snooping at work - on an untrusted port
FIGURE 25 DHCP snooping at work - on a trusted port
DHCP binding database
On trusted ports, DHCP server reply packets are forwarded to DHCP clients. The DHCP server reply
packets collect client IP to MAC address binding information, which is saved in the DHCP binding
database. This information includes MAC address, IP address, lease time, VLAN number, and port
number.
In the Brocade device, the DHCP binding database is integrated with the enhanced ARP table, which is
used by Dynamic ARP Inspection. For more information, refer to
How DHCP snooping works
FastIron Ethernet Switch Security Configuration Guide
337
53-1003088-03
