Arp entries – Brocade FastIron Ethernet Switch Security Configuration Guide User Manual
Page 333
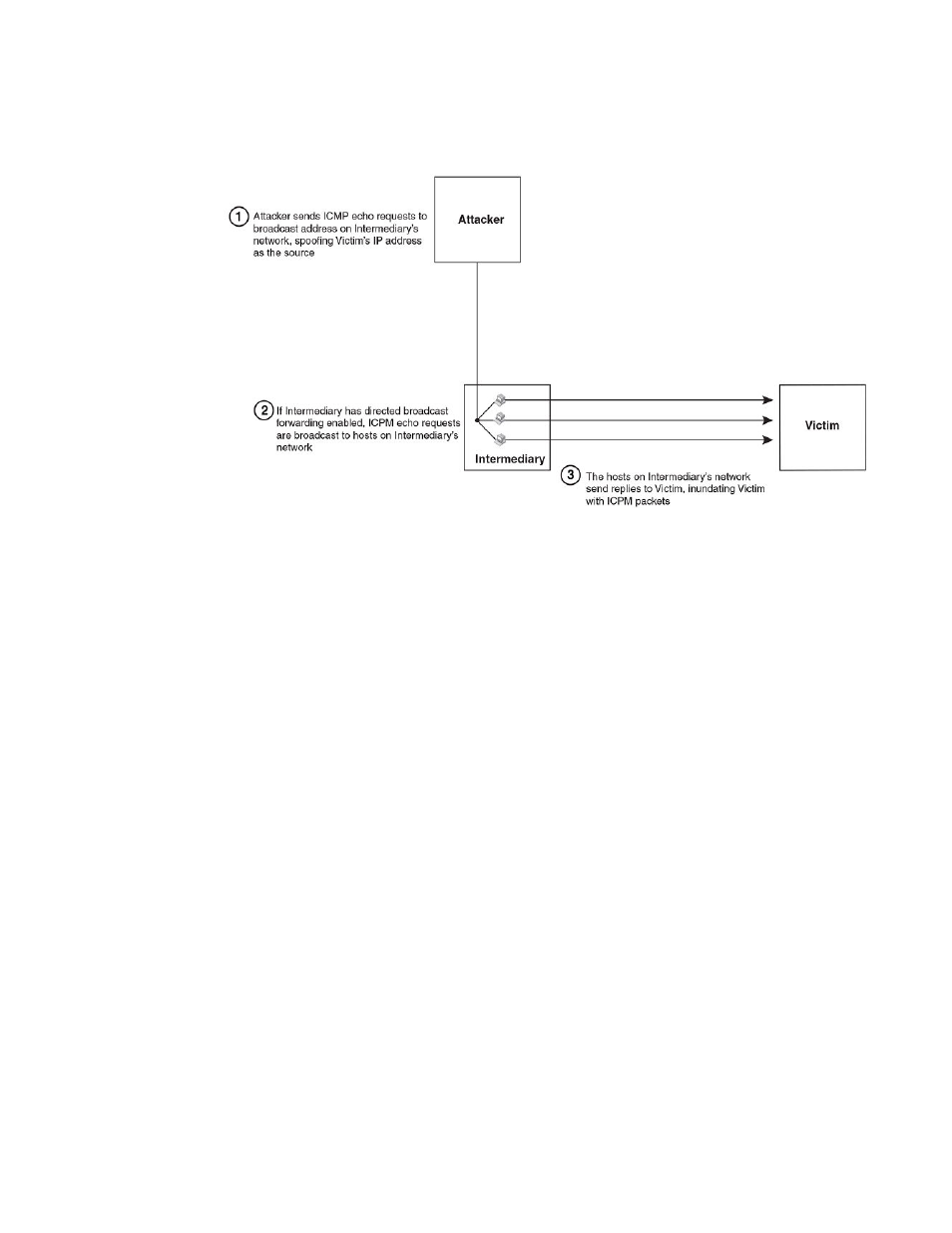
FIGURE 23 Dynamic ARP inspection at work
ARP entries
DAI uses the IP/MAC mappings in the ARP table to validate ARP packets received on untrusted ports.
ARP entries in the ARP table derive from the following:
• Dynamic ARP - normal ARP learned from trusted ports.
• Static ARP - statically configured IP/MAC/port mapping.
• Inspection ARP - statically configured IP/MAC mapping, where the port is initially unspecified. The
actual physical port mapping will be resolved and updated from validated ARP packets.Refer to
Configuring an inspection ARP entry
on page 334.
• DHCP-Snooping ARP - information collected from snooping DHCP packets when DHCP snooping is
enabled on VLANs.
The status of an ARP entry is either pending or valid:
• Valid - the mapping is valid, and the port is resolved. This is always the case for static ARP entries.
• Pending - for normal dynamic and inspection ARP entries before they are resolved, and the port
mapped. Their status changes to valid when they are resolved, and the port mapped.
Refer to also
System reboot and the binding database
Configuration notes and feature limitations for DAI
The following limits and restrictions apply when configuring DAI:
• To run Dynamic ARP Inspection, you must first enable support for ACL filtering based on VLAN
membership or VE port membership. To do so, enter the following commands at the Global CONFIG
Level of the CLI.
device(config)#enable ACL-per-port-per-vlan
device(config)#write memory
device(config)#exit
device#reload
ARP entries
FastIron Ethernet Switch Security Configuration Guide
333
53-1003088-03
