Message exchange during authentication – Brocade FastIron Ethernet Switch Security Configuration Guide User Manual
Page 173
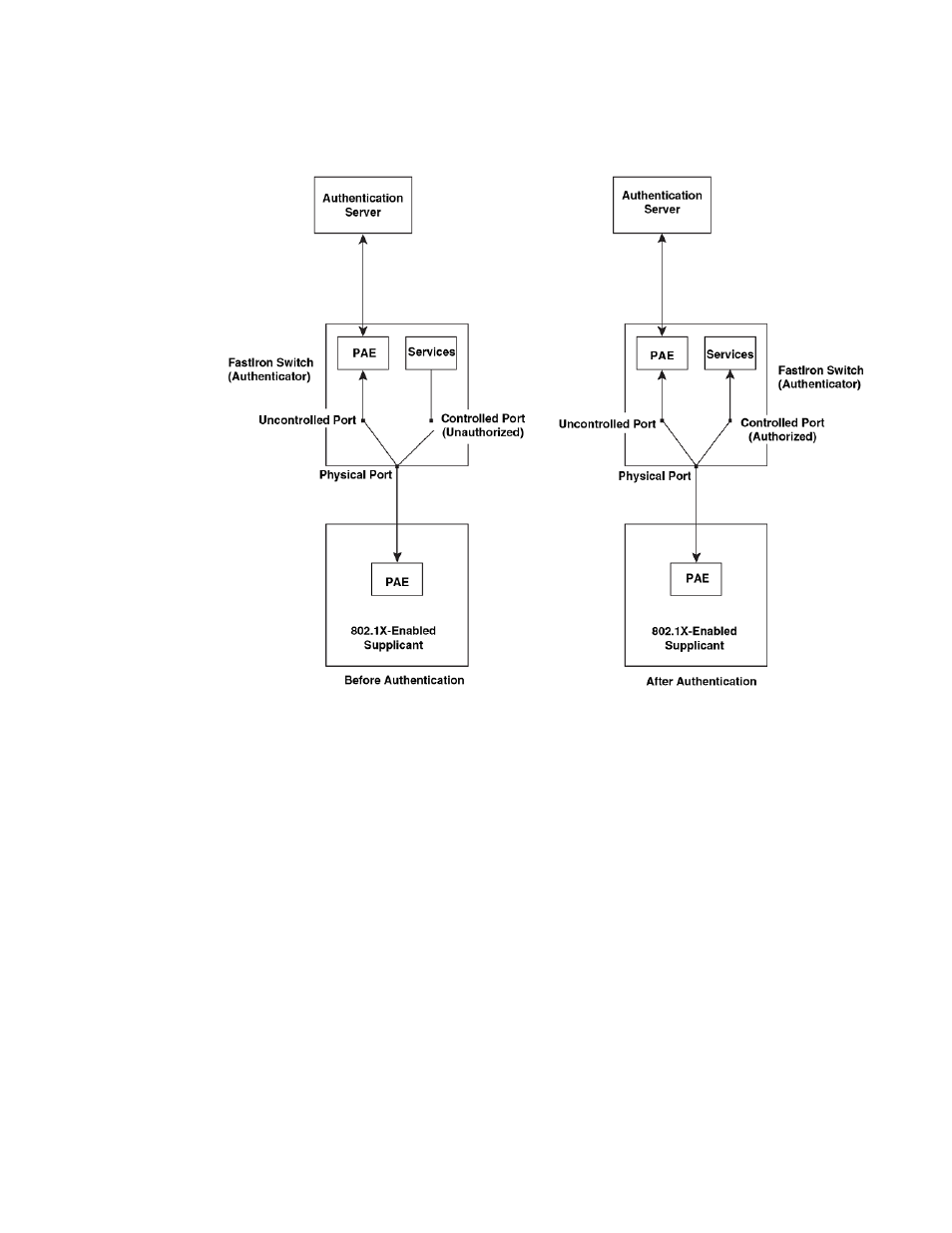
FIGURE 3 Controlled and uncontrolled ports before and after client authentication
Before a Client is authenticated, only the uncontrolled port on the Authenticator is open. The
uncontrolled port allows only EAPOL frames to be exchanged between the Client and the
Authentication Server. The controlled port is in the unauthorized state and allows no traffic to pass
through.
During authentication, EAPOL messages are exchanged between the Supplicant PAE and the
Authenticator PAE, and RADIUS messages are exchanged between the Authenticator PAE and the
Authentication Server.Refer to
Message exchange during authentication
on page 173 for an example
of this process. If the Client is successfully authenticated, the controlled port becomes authorized, and
traffic from the Client can flow through the port normally.
By default, all controlled ports on the Brocade device are placed in the authorized state, allowing all
traffic. When authentication is activated on an 802.1X-enabled interface, the interface controlled port is
placed initially in the unauthorized state. When a Client connected to the port is successfully
authenticated, the controlled port is then placed in the authorized state until the Client logs off. Refer to
on page 191 for more information.
Message exchange during authentication
The following figure illustrates a sample exchange of messages between an 802.1X-enabled Client, a
FastIron switch acting as Authenticator, and a RADIUS server acting as an Authentication Server.
Message exchange during authentication
FastIron Ethernet Switch Security Configuration Guide
173
53-1003088-03
