Load sharing, Load sharing and primary and secondary connections – Fortinet FortiGate-800 User Manual
Page 53
NAT/Route mode installation
Configuration example: Multiple connections to the Internet
FortiGate-800 Installation and Configuration Guide
53
Load sharing
You can also configure destination routing to direct traffic through both gateways at
the same time. If users on the internal network connect to the networks of ISP1 and
ISP2, you can add routes for each of these destinations. Each route can include a
backup destination to the network of the other ISP.
The first route directs all traffic destined for the 100.100.100.0 network out the external
interface to gateway 1 with the IP address 1.1.1.1. If this router is down, traffic
destined for the 100.100.100.0 network is redirected out the DMZ interface to gateway
2 with the IP address 2.2.2.1.
Load sharing and primary and secondary connections
You can combine these routes into a more complete multiple Internet connection
configuration. In the topology shown in
Figure 9 on page 51
, users on the internal
network connect to the Internet to access web pages and other Internet resources.
However, they can also connect to services, such as email, provided by their ISPs.
You can combine the routes described in the previous examples to provide users with
a primary and backup connection to the Internet, while at the same time routing traffic
to each ISP network as required.
The routing described below allows a user on the internal network to connect to the
Internet through gateway 1 and ISP1. At the same time, this user can also connect
through gateway 2 to access a mail server maintained by ISP2.
To add the routes using the web-based manager
1
Go to System > Network > Routing Table.
2
Select New to add the default route for primary and backup links to the Internet.
• Destination IP: 0.0.0.0
• Mask: 0.0.0.0
• Gateway #1: 1.1.1.1
• Gateway #2: 2.2.2.1
• Device #1: external
• Device #2: dmz
• Select OK.
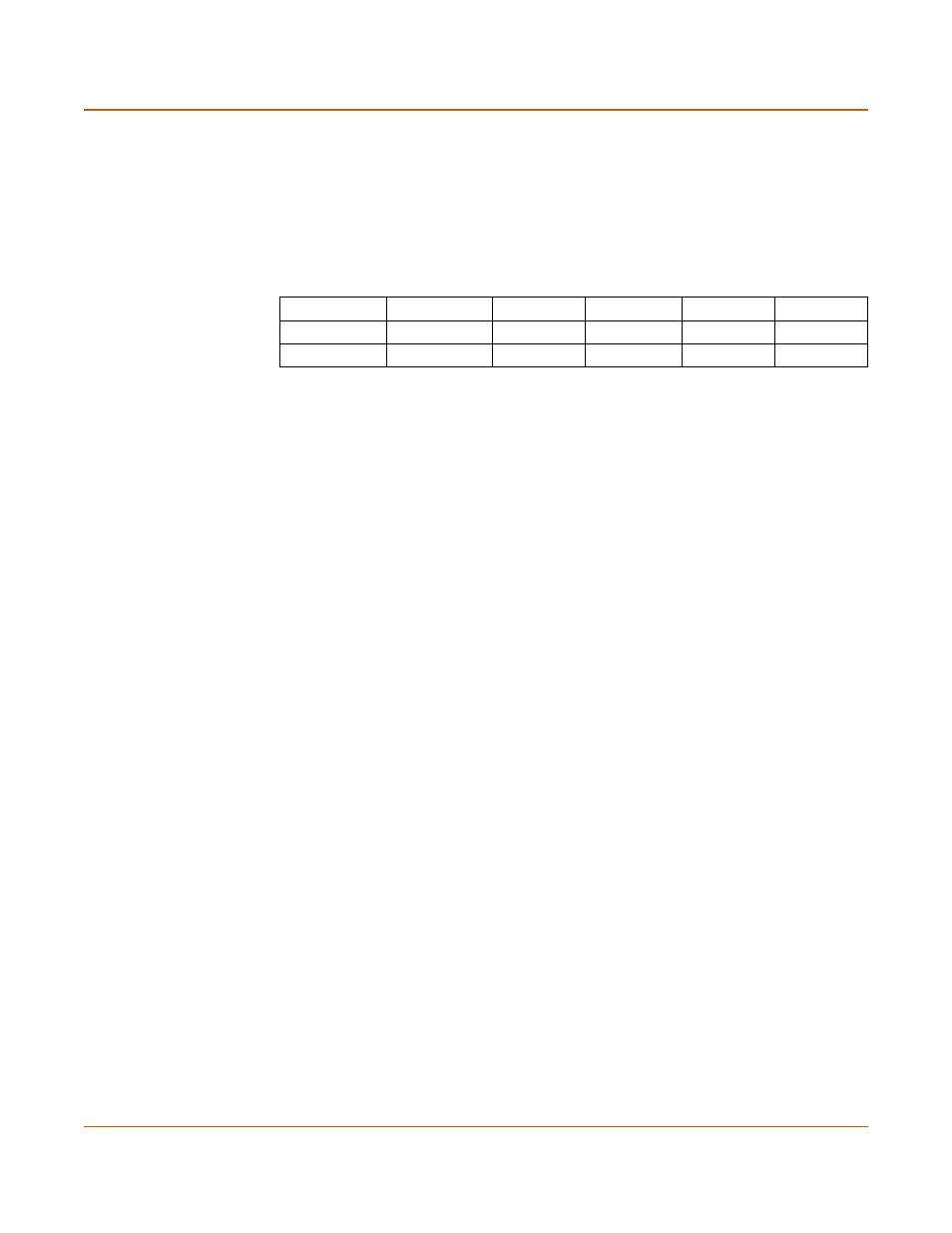
Table 14: Load sharing routes
Destination IP‘ Mask
Gateway #1
Device #1
Gateway #2
Device #2
100.100.100.0
255.255.255.0
1.1.1.1
external
2.2.2.1
dmz
200.200.200.0
255.255.255.0
2.2.2.1
dmz
1.1.1.1
external
