Fortinet FortiGate-800 User Manual
Page 151
Network configuration
Virtual domains in Transparent mode
FortiGate-800 Installation and Configuration Guide
151
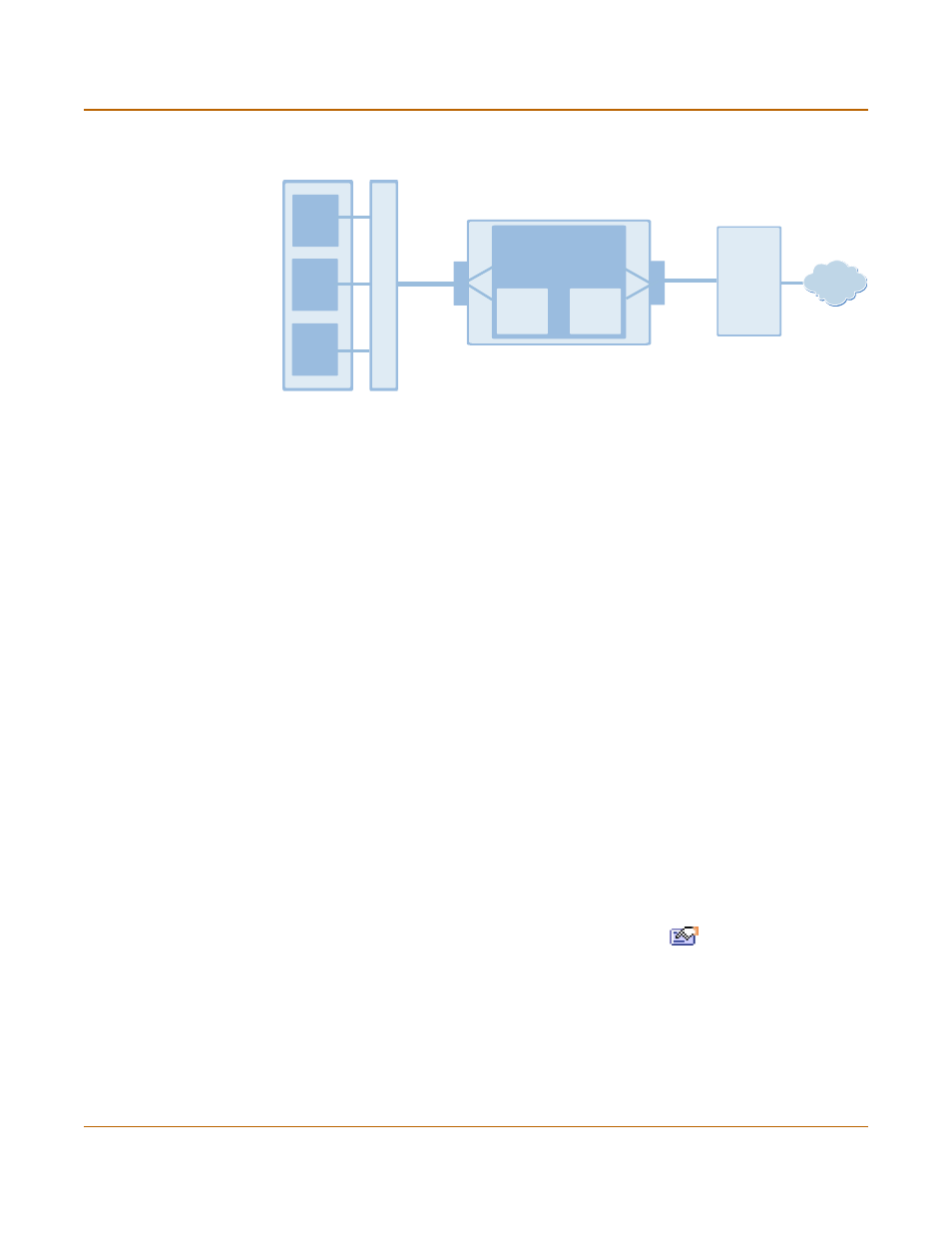
Figure 32: FortiGate unit containing a virtual domain with zones
Multiple zones in a single virtual domain cannot be connected to a single VLAN trunk.
This configuration is correct because each zone is connected to a different VLAN
trunk (zone1 connected to the VLAN trunk on the internal interface and zone2
connected to the VLAN trunk on the external interface). If you were to add another
zone (for example, zone3 connected to the VLAN trunk on the internal interface) the
FortiGate unit would not be able to successfully differentiate between traffic for zone1
and zone3. This is the case because both zone 1 and zone3 traffic would be routed to
the same MAC address.
To add a zone to a virtual domain
1
Go to System > Network > Zone.
2
Select New to add a zone.
3
Type a Name for the zone.
4
Select the Virtual Domain to add the zone to.
5
Optionally select Block intra-zone traffic to block traffic between VLAN subinterfaces
in the same zone.
6
Select OK to add the zone.
To add VLAN subinterfaces to a zone
1
Go to System > Network > VLAN.
2
Set Virtual Domain to All or to the virtual domain containing the VLAN subinterfaces to
add to a zone.
3
Select List to list all of VLAN subinterfaces added to the FortiGate unit or to the
selected virtual domain.
4
For a VLAN subinterface to add to a zone, select Modify
.
5
From the zone list, select the name of the zone to add the VLAN subinterface to.
6
Select OK to save your changes.
You can also use the procedure
“Adding VLAN subinterfaces” on page 147
to add a
VLAN subinterface to a zone if you are adding new VLAN subinterfaces to a virtual
domain to which you have already added zones.
VLAN1
VLAN1
VLAN2
VLAN2
VLAN3
VLAN3
Virtual Domain
Internal
External
VLAN1
VLAN Switch
or router
VLAN Switch or router
VLAN trunk
VLAN1
VLAN2
VLAN3
VLAN trunk
FortiGate unit
VLAN1
Internet
VLAN3
VLAN2
zone1
zone2
VLAN3
VLAN2
