4 802.1x settings – Planet Technology WGSD-8000 User Manual
Page 80
User’s Manual of WGSD-1022/WGSD-8000
- 80 –
4.7.4 802.1x settings
Understanding IEEE 802.1X Port-Based Authentication
The IEEE 802.1X standard defines a client-server-based access control and authentication protocol that restricts unauthorized
clients from connecting to a LAN through publicly accessible ports. The authentication server authenticates each client
connected to a switch port before making available any services offered by the switch or the LAN.
Until the client is authenticated, 802.1X access control allows only Extensible Authentication Protocol over LAN (EAPOL) traffic
through the port to which the client is connected. After authentication is successful, normal traffic can pass through the port.
This section includes this conceptual information:
• Authentication Initiation and Message Exchange
• Ports in Authorized and Unauthorized States
Device Roles
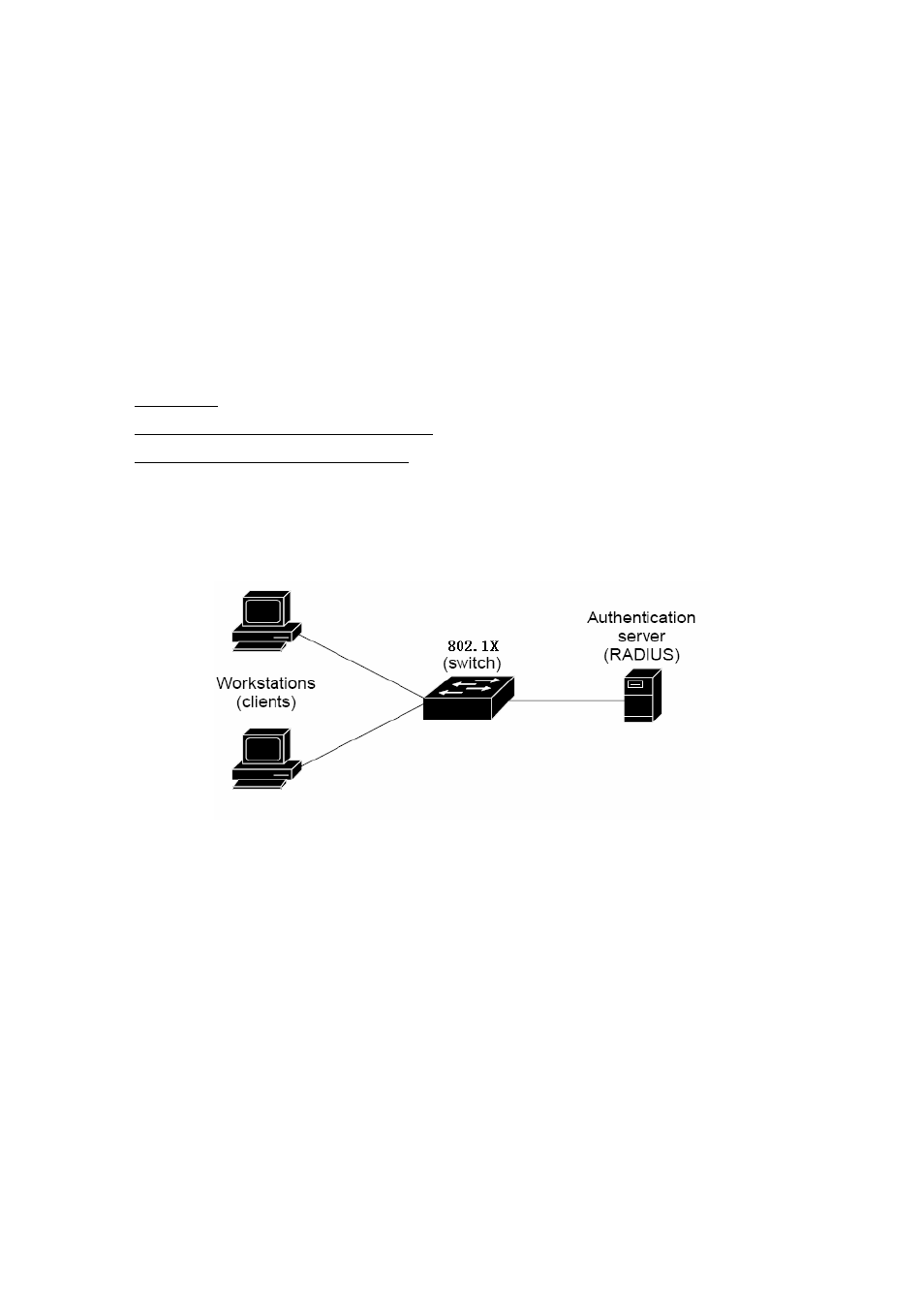
With 802.1X port-based authentication, the devices in the network have specific roles as shown below.
z
Client
—the device (workstation) that requests access to the LAN and switch services and responds to requests from
the switch. The workstation must be running 802.1X-compliant client software such as that offered in the Microsoft
Windows XP operating system. (The client is the supplicant in the IEEE 802.1X specification.)
z
Authentication server
—performs the actual authentication of the client. The authentication server validates the
identity of the client and notifies the switch whether or not the client is authorized to access the LAN and switch services.
Because the switch acts as the proxy, the authentication service is transparent to the client. In this release, the Remote
Authentication Dial-In User Service (RADIUS) security system with Extensible Authentication Protocol (EAP)
extensions is the only supported authentication server; it is available in Cisco Secure Access Control Server version 3.0.
RADIUS operates in a client/server model in which secure authentication information is exchanged between the
RADIUS server and one or more RADIUS clients.
z
Switch (802.1X device)
—controls the physical access to the network based on the authentication status of the client.
The switch acts as an intermediary (proxy) between the client and the authentication server, requesting identity
information from the client, verifying that information with the authentication server, and relaying a response to the client.
