Configuring the secure shell, Configuring the secure shell -40 – Asus GigaX2024SX User Manual
Page 65
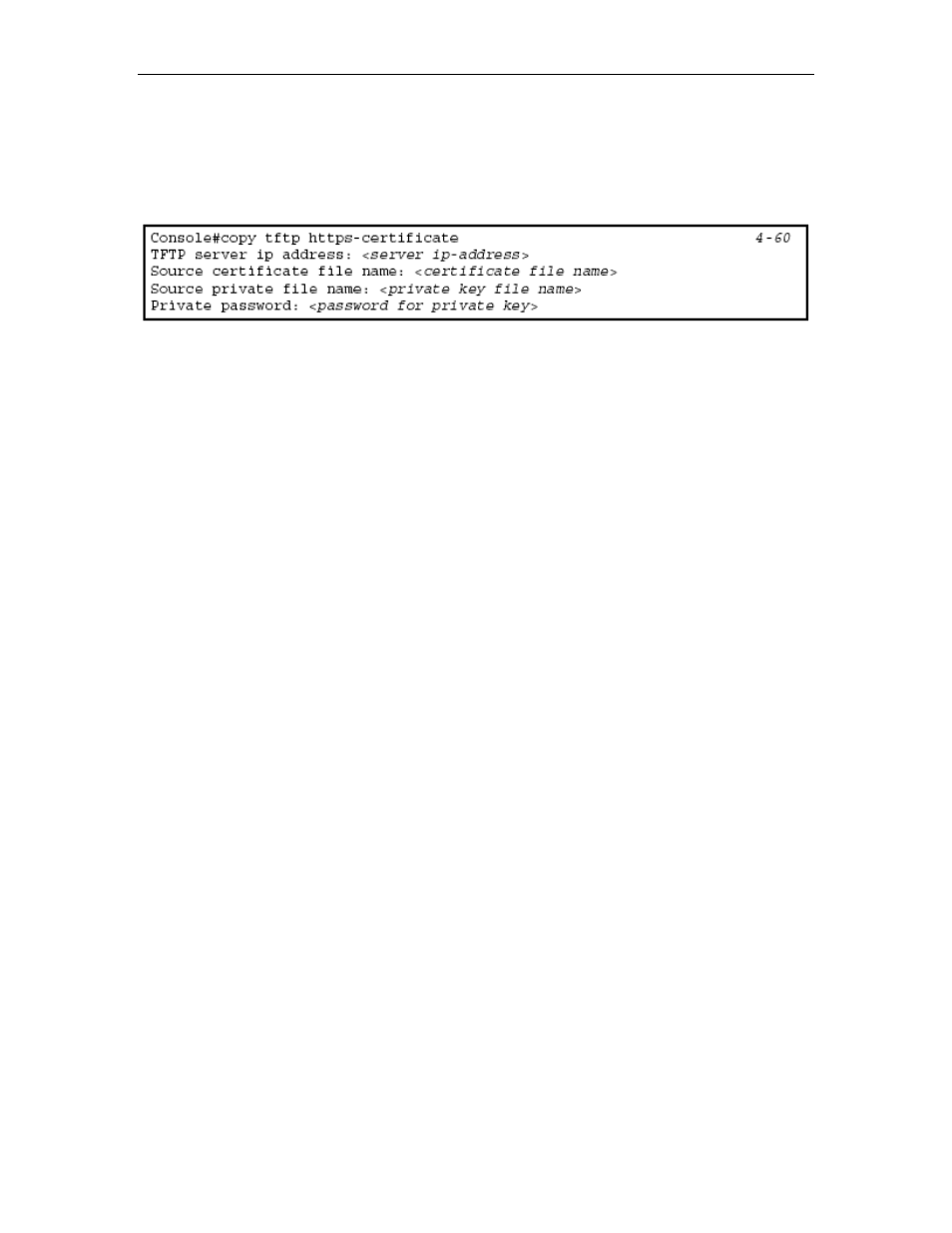
certificate for the switch is not unique to the hardware you have purchased.
When you have obtained these, place them on your TFTP server, and use the
following command at the switch's command-line interface to replace the default
(unrecognized) certificate with an authorized one:
Note: The switch must be reset for the new certificate to be activated. To reset the
switch, type: Console#reload
The Berkley-standard includes remote access tools originally designed for Unix
agement access to this switch as a secure replacement for Telnet.
ensures that data
rotocol.
y
the Authentication Settings page
st
the switch (SSH
ings).
Configuring the Secure Shell
systems. Some of these tools have also been implemented for Microsoft Windows
and other environments. These tools, including commands such as rlogin (remote
e shell), and rcp (remote copy), are not secure from hostile
login), rsh (remot
attacks.
The Secure Shell (SSH) includes server/client applications intended as a secure
t for the older Berkley remote access tools. SSH can also provide
replacemen
emote man
r
When the client contacts the switch via the SSH protocol, the switch generates a
public-key that the client uses along with a local user name and password for
access authentication. SSH also encrypts all data transfers passing between the
witch and SSH-enabled management station clients, and
s
traveling over the network arrives unaltered.
Note that you need to install an SSH client on the management station to access
e switch for management via the SSH p
th
Note: The switch supports both SSH Version 1.5 and 2.0.
Command Usage
he SSH server on this switch supports both password and public ke
T
authentication. If password authentication is specified by the SSH client, then the
lly or via a RADIUS or TACACS+
password can be authenticated either loca
emote authentication server, as specified on
r
(page 3-33). If public key authentication is specified by the client, then you mu
the switch as described in the
configure authentication keys on both the client and
hat regardless of whether you use public key or password
following section. Note t
authentication, you still have to generate authentication keys on
Host Key Settings) and enable the SSH server (Authentication Sett
To use the SSH server, complete these steps:
3-40
