Aaa for multi-vpns, Protocols and standards, Radius attributes – H3C Technologies H3C SecBlade LB Cards User Manual
Page 57
46
•
Command accounting—Allows the accounting server to record all commands executed on the
device or all authorized commands successfully executed. For more information about command
accounting, see System Management Configuration Guide.
•
Level switching authentication—Allows the authentication server to authenticate users who perform
privilege level switching. As long as passing level switching authentication, users can switch their
user privilege levels, without logging out and disconnecting current connections. For more
information about user privilege level switching, see System Management Configuration Guide.
You can configure different AAA methods for different types of users in a domain. See "
AAA for multi-VPNs
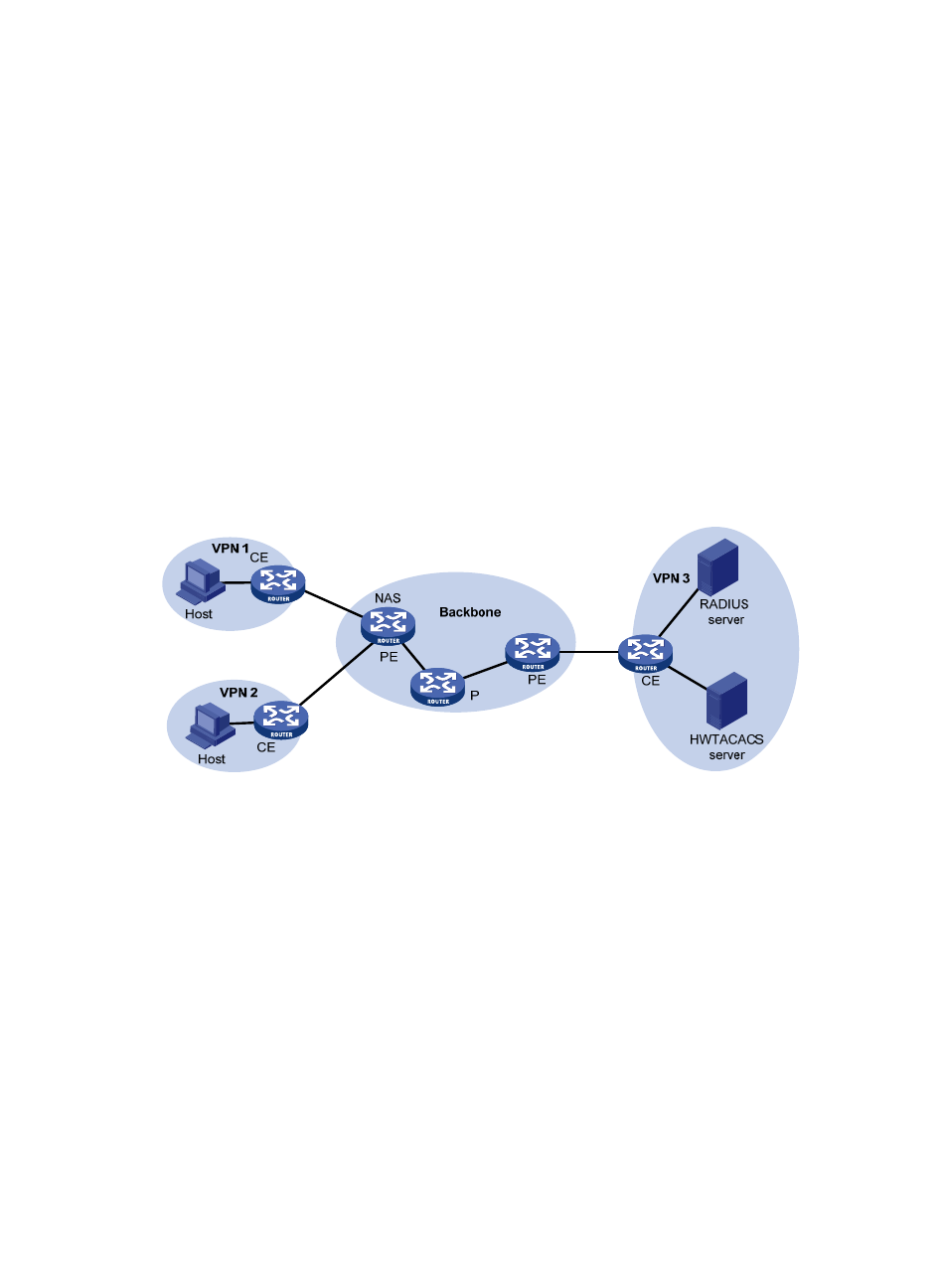
In a scenario where clients in different VPNs are centrally authenticated, you can deploy AAA across
VPNs to enable forwarding of RADIUS and HWTACACS packets across VPNs. With this feature, the PE
at the left side of the backbone serves as a NAS and transparently delivers the AAA packets of private
users in VPN 1 and VPN 2 to the AAA servers in VPN 3 for centralized authentication, as shown in
. Authentication packets of private users in different VPNs do not affect each other.
Figure 27 Network diagram
Protocols and standards
The following protocols and standards are related to AAA, RADIUS, and HWTACACS:
•
RFC 2865, Remote Authentication Dial In User Service (RADIUS)
•
RFC 2866, RADIUS Accounting
•
RFC 2867, RADIUS Accounting Modifications for Tunnel Protocol Support
•
RFC 2868, RADIUS Attributes for Tunnel Protocol Support
•
RFC 2869, RADIUS Extensions
•
RFC 1492, An Access Control Protocol, Sometimes Called TACACS
RADIUS attributes
This section provides tables of commonly used standard RADIUS attributes and H3C proprietary RADIUS
sub-attributes.
