Verifying the configuration, Displaying intrusion detection statistics, Figure 139 – H3C Technologies H3C SecBlade LB Cards User Manual
Page 252
241
d.
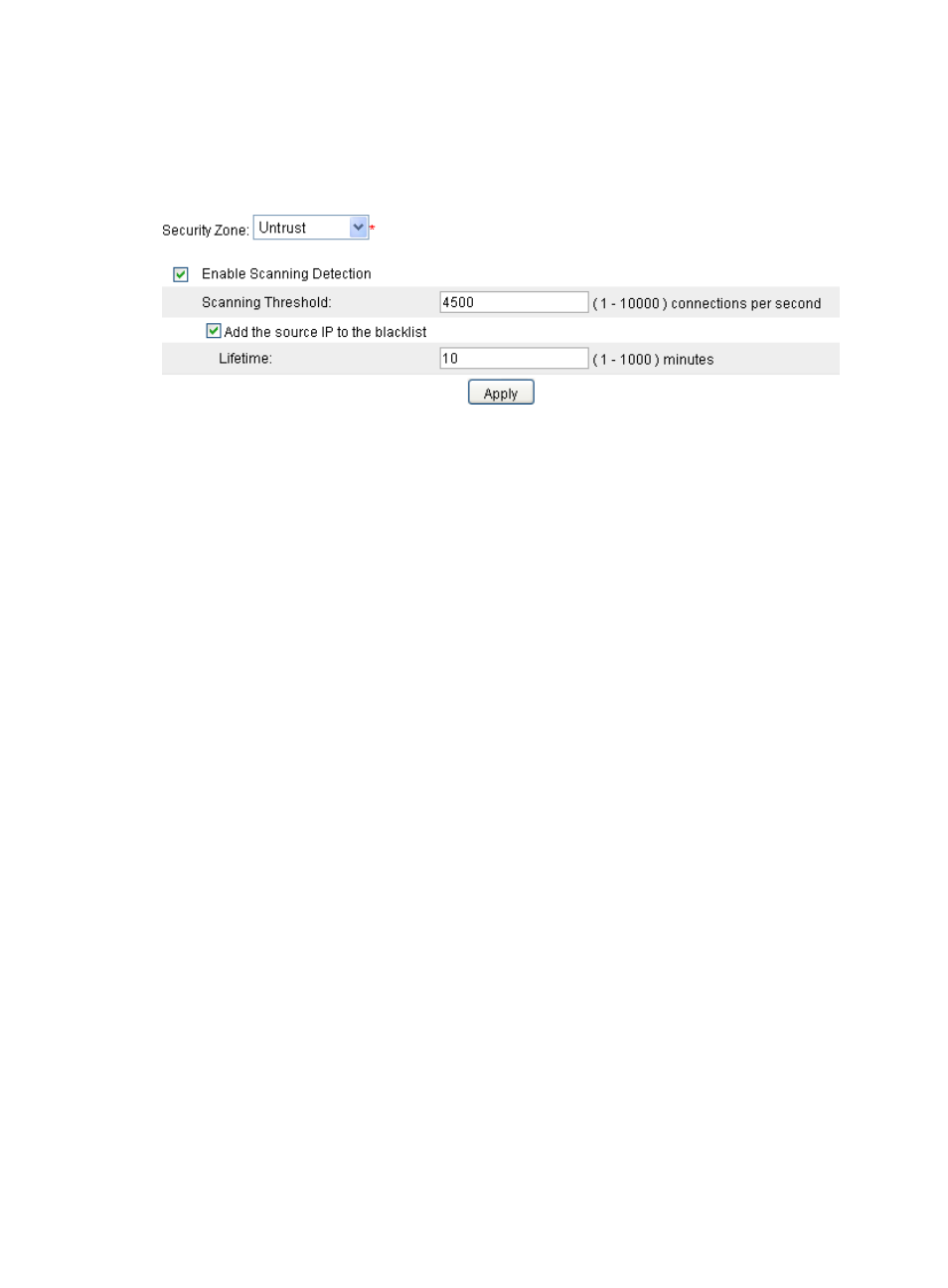
Set the scanning threshold to 4500.
e.
Select Add the source IP to the blacklist.
f.
Click Apply.
Figure 139 Configuring scanning detection for the untrusted zone
Verifying the configuration
Select Security > Intrusion Detection > Blacklist from the navigation tree to view the manually added
blacklist entries.
The device discards all packets from Host D before you remove the blacklist entry for the host. If the device
receives packets from Host C, the device discards all packets from Host C within 50 minutes. After 50
minutes, the device forwards packets from Host C normally.
The device outputs an alarm log and adds the IP address to the blacklist when detecting a scanning
attack from the untrusted zone. You can select Security > Intrusion Detection > Blacklist from the
navigation tree to view the blacklist entry automatically added by scanning attack protection.
Displaying intrusion detection statistics
To display intrusion detection statistics:
1.
From the navigation tree, select Security > Intrusion Detection > Statistics to enter the intrusion
detection statistics page, as shown in
.
2.
Select a zone to view the counts of attacks and the counts of dropped packets in the security zone.
Descriptions of attack types are shown in
.
