Network requirements, Configuration procedure – H3C Technologies H3C SecBlade LB Cards User Manual
Page 265
254
Configuring attack protection functions on security zones
Network requirements
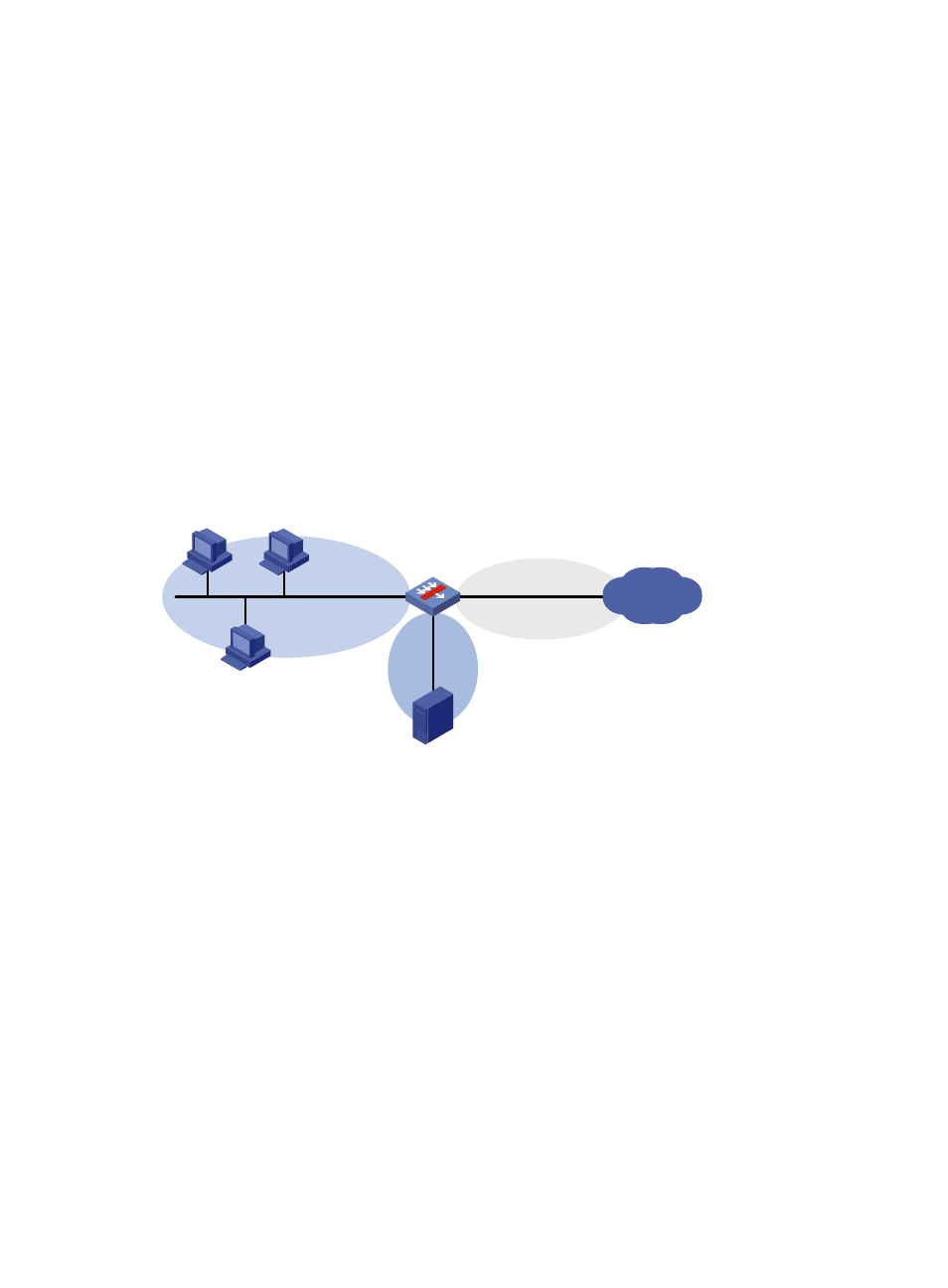
As shown in
, security zone Trust on LB is connected to the internal network, security zone
Untrust is connected to the external network, and security zone DMZ is connected to an internal server.
Protect internal hosts against Smurf attacks and scanning attacks from the external network. Protect the
internal server against SYN flood attacks from the external network. To meet the requirements, perform
the following configurations:
•
In security zone Untrust, configure Smurf attack protection and scanning attack protection, enable
the blacklist function for scanning attack protection, and set the connection rate threshold that
triggers the scanning attack protection to 4500 connections per second.
•
In security zone DMZ, configure SYN flood attack protection, so that LB drops subsequent SYN
packets when the SYN packet sending rate to a server constantly reaches or exceeds 5000 packets
per second, and permits SYN packets to be sent to the server again when this rate drops below
1000 packets per second.
Figure 141 Network diagram
Configuration procedure
# Assign IP addresses to the interfaces. (Details not shown.)
# Add interface GigabitEthernet 0/1 to security zone Trust.
[LB] zone name Trust
[LB-zone-Trust] import interface gigabitethernet 0/1
[LB-zone-Trust] quit
# Add interface GigabitEthernet 0/3 to security zone DMZ.
[LB] zone name DMZ
[LB-zone-DMZ] import interface gigabitethernet 0/3
[LB-zone-DMZ] quit
# Add interface GigabitEthernet 0/2 to security zone Untrust.
[LB] zone name Untrust
[LB-zone-Untrust] import interface gigabitethernet 0/2
[LB-zone-Untrust] quit
Internet
LB
Server
Host C
GE0/2
GE0/1
GE0/3
Host A
Host B
202.1.0.1/16
192.168.1.1/16
10.1.1.2/24
10.1.1.1/24
Trust
DMZ
Untrust
