Verifying the configuration, Figure 123 – H3C Technologies H3C SecBlade LB Cards User Manual
Page 242
231
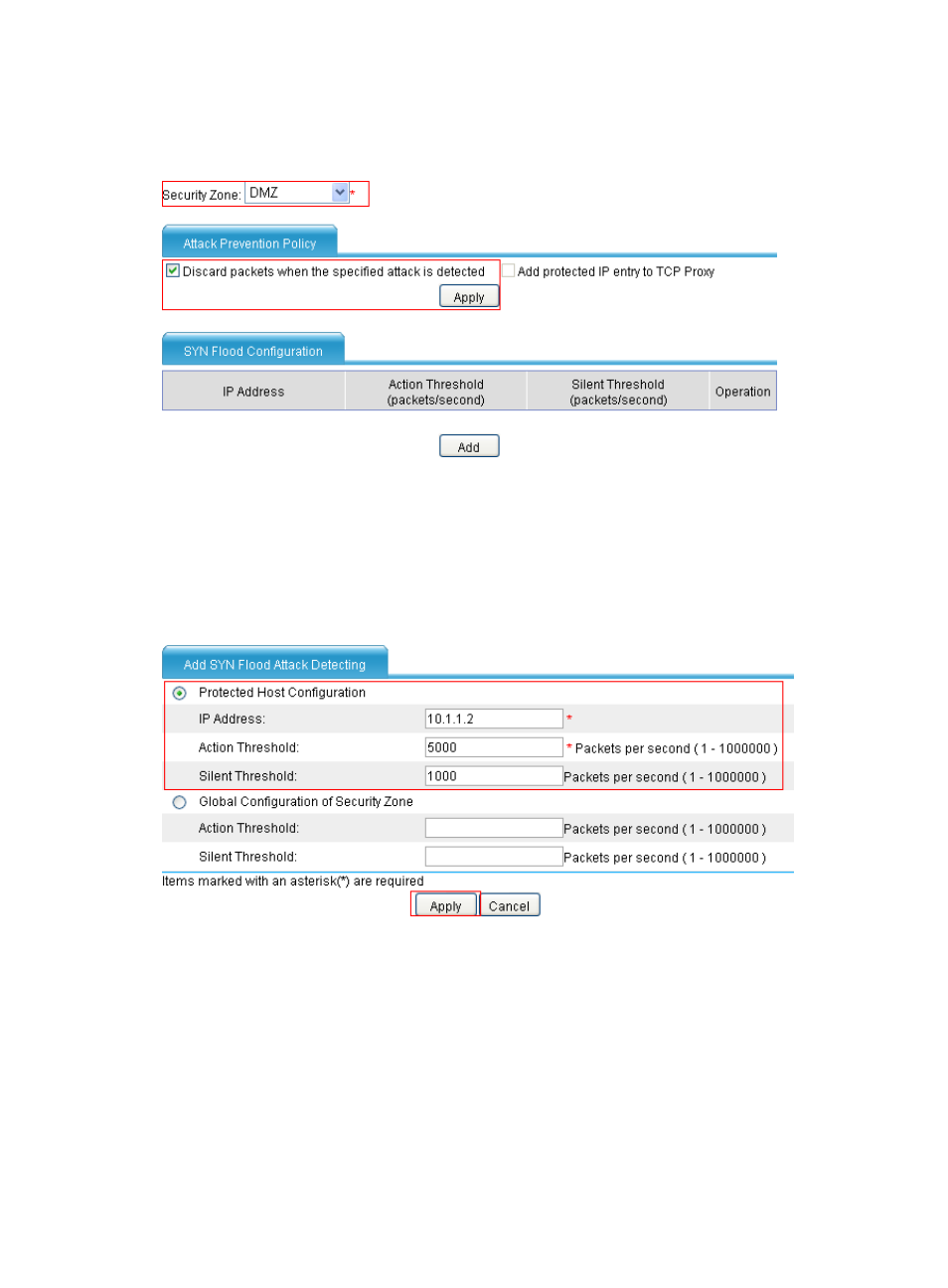
c.
In the Attack Prevention Policy area, select Discard packets when the specified attack is
detected. Click Apply.
Figure 123 Configuring SYN flood detection for the DMZ
d.
In the SYN Flood Configuration area, click Add.
The SYN flood attack detection page appears, as shown in
e.
Select Protected Host Configuration. Enter the IP address 10.1.1.2. Set the action threshold to
5000 packets per second and the silent threshold to 1000 packets per second.
f.
Click Apply.
Figure 124 Configuring a SYN flood attack detection rule for the server
Verifying the configuration
•
After a scanning attack packet is received from zone Untrust, the device outputs alarm logs and
adds the IP address of the attacker to the blacklist. You can select Security > Intrusion Detection >
Blacklist from the navigation tree to view whether the attacker's IP address is on the blacklist.
•
If a host in zone Trust initiates 100 or more connections, the device outputs alarm logs and discards
subsequent connection request packets from the host. You can select Security > Intrusion Detection >
Statistics from the navigation tree to view how many times that a connection limit per source IP
address has been exceeded and the number of packets dropped.
•
If the number of connections to the server in the DMZ reaches or exceeds 10000, the device outputs
alarm logs and discards subsequent connection request packets. You can select Security > Intrusion
