Security zone configuration example, Network requirements, Configuration considerations – H3C Technologies H3C SecBlade LB Cards User Manual
Page 20: Configuration procedure
9
Security zone configuration example
Network requirements
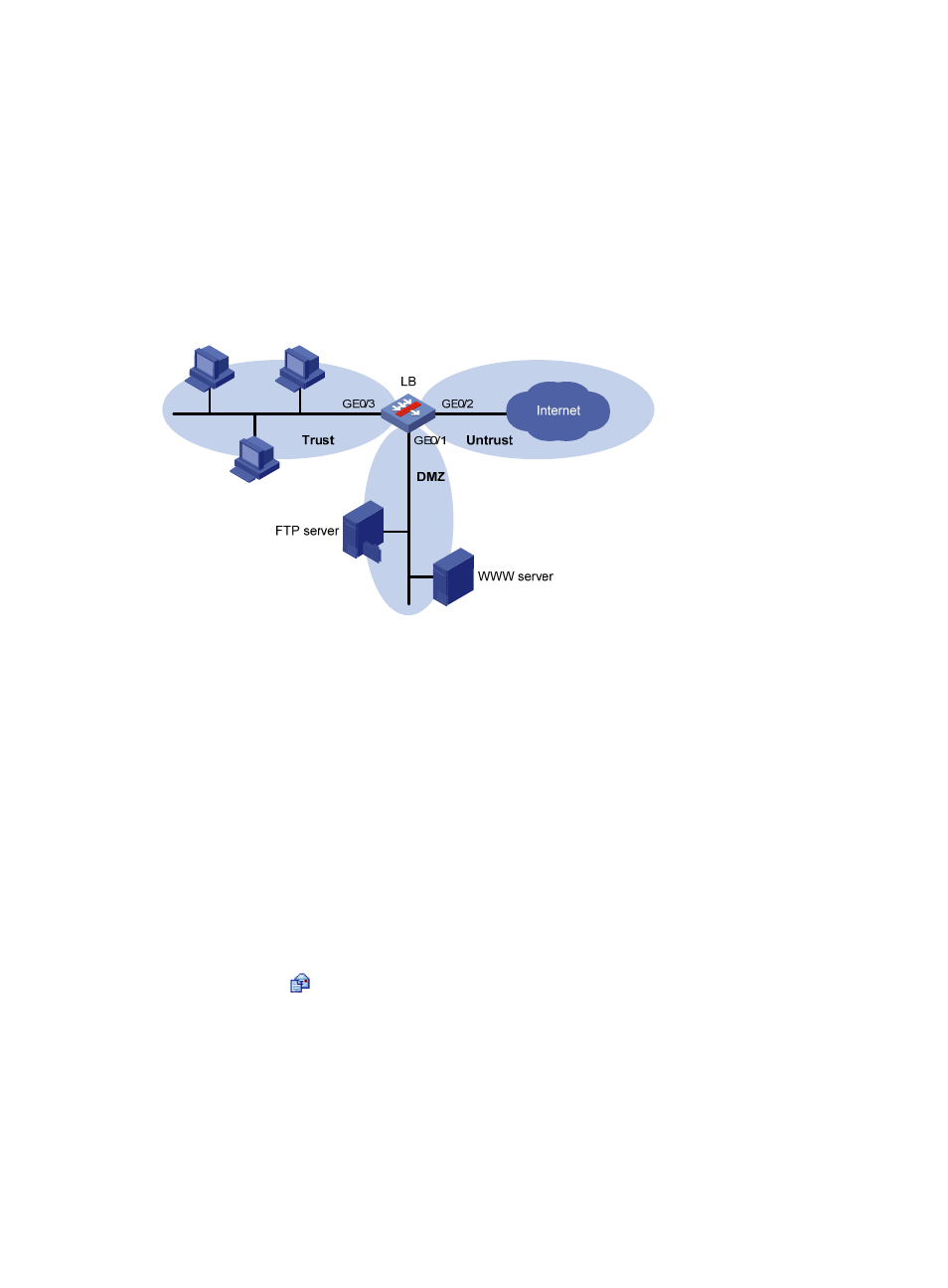
A company deploys a firewall (LB in
) to connect its internal network to the Internet, and it needs
to provide WWW service and FTP service for external users. The security policy is to allow internal users
to access the WWW and FTP servers and the Internet and to allow external users to access only the
servers.
Prepare LB for zone-based security policy deployment.
Figure 5 Network diagram
Configuration considerations
Three security zones are needed: one for the internal users, one for the servers, and one for the external
users, in the order of priority (from high to low). The default zones Trust, DMZ, and Untrust can answer
the requirements for security zones.
To prepare the firewall for zone-based security policy deployment, configure the firewall as follows:
•
Add the port connected to the internal network (GigabitEthernet 0/3) to security zone Trust.
•
Add the port connected to the Internet (GigabitEthernet 0/2) to security zone Untrust.
•
Deploy the servers in security zone DMZ, and add the port connected to the servers
(GigabitEthernet 0/1) to security zone DMZ.
Configuration procedure
1.
Add interface GigabitEthernet 0/3 to security zone Trust:
a.
Select Security > Zone from the navigation tree to enter the security zone management page.
b.
Click the
icon for security zone Trust.
c.
Select interface GigabitEthernet0/3.
d.
Click Apply.
e.
Click Back to return to the security zone management page.
