Domain-based user management – H3C Technologies H3C SecBlade LB Cards User Manual
Page 56
45
9.
The user enters the password.
10.
After receiving the login password, the HWTACACS client sends the HWTACACS server a
continue-authentication packet that carries the login password.
11.
The HWTACACS server sends back an authentication response to indicate that the user has
passed authentication.
12.
The HWTACACS client sends the user authorization request packet to the HWTACACS server.
13.
The HWTACACS server sends back the authorization response, indicating that the user is now
authorized.
14.
Knowing that the user is now authorized, the HWTACACS client pushes its CLI to the user.
15.
The HWTACACS client sends a start-accounting request to the HWTACACS server.
16.
The HWTACACS server sends back an accounting response, indicating that it has received the
start-accounting request.
17.
The user logs off.
18.
The HWTACACS client sends a stop-accounting request to the HWTACACS server.
19.
The HWTACACS server sends back a stop-accounting response, indicating that the
stop-accounting request has been received.
Domain-based user management
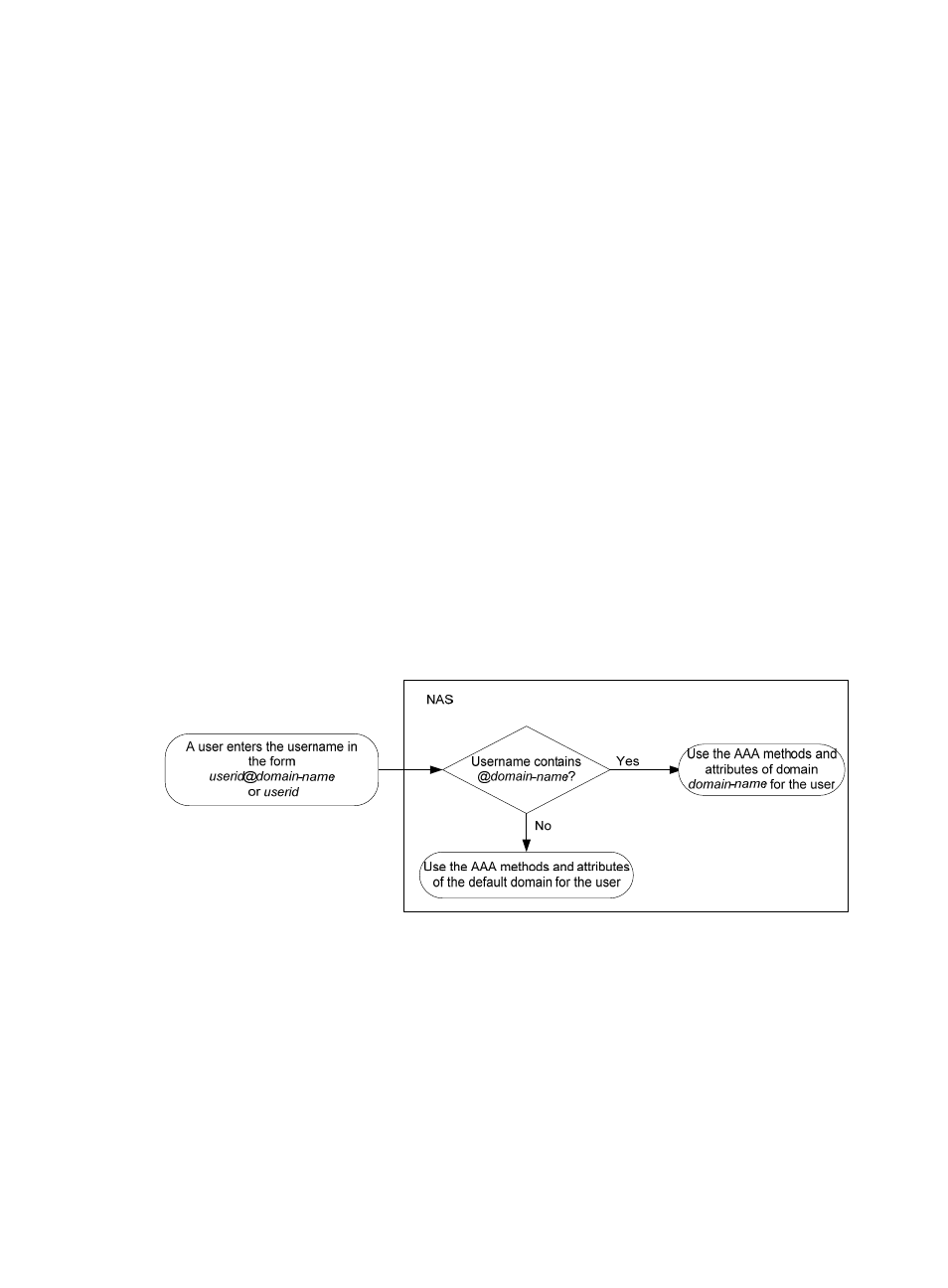
A NAS manages users based on ISP domains. On a NAS, each user belongs to one ISP domain. A NAS
determines the ISP domain for a user by the username entered by the user at login, as shown in
.
Figure 26 Determining the ISP domain of a user by the username
Authentication, authorization, and accounting of a user depends on the AAA methods configured for the
domain that the user belongs to. If no specific AAA methods are configured for the domain, the default
methods are used. By default, a domain uses local authentication, local authorization, and local
accounting.
AAA allows you to manage login users, including SSH, Telnet, Web, FTP, and terminal users.
In addition, AAA provides the following services for login users to enhance device security:
•
Command authorization—Enables the NAS to defer to the authorization server to determine
whether a command entered by a login user is permitted, and allows login users to execute only
authorized commands. For more information about command authorization, see System
Management Configuration Guide.
