H3C Technologies H3C SecBlade LB Cards User Manual
Page 253
242
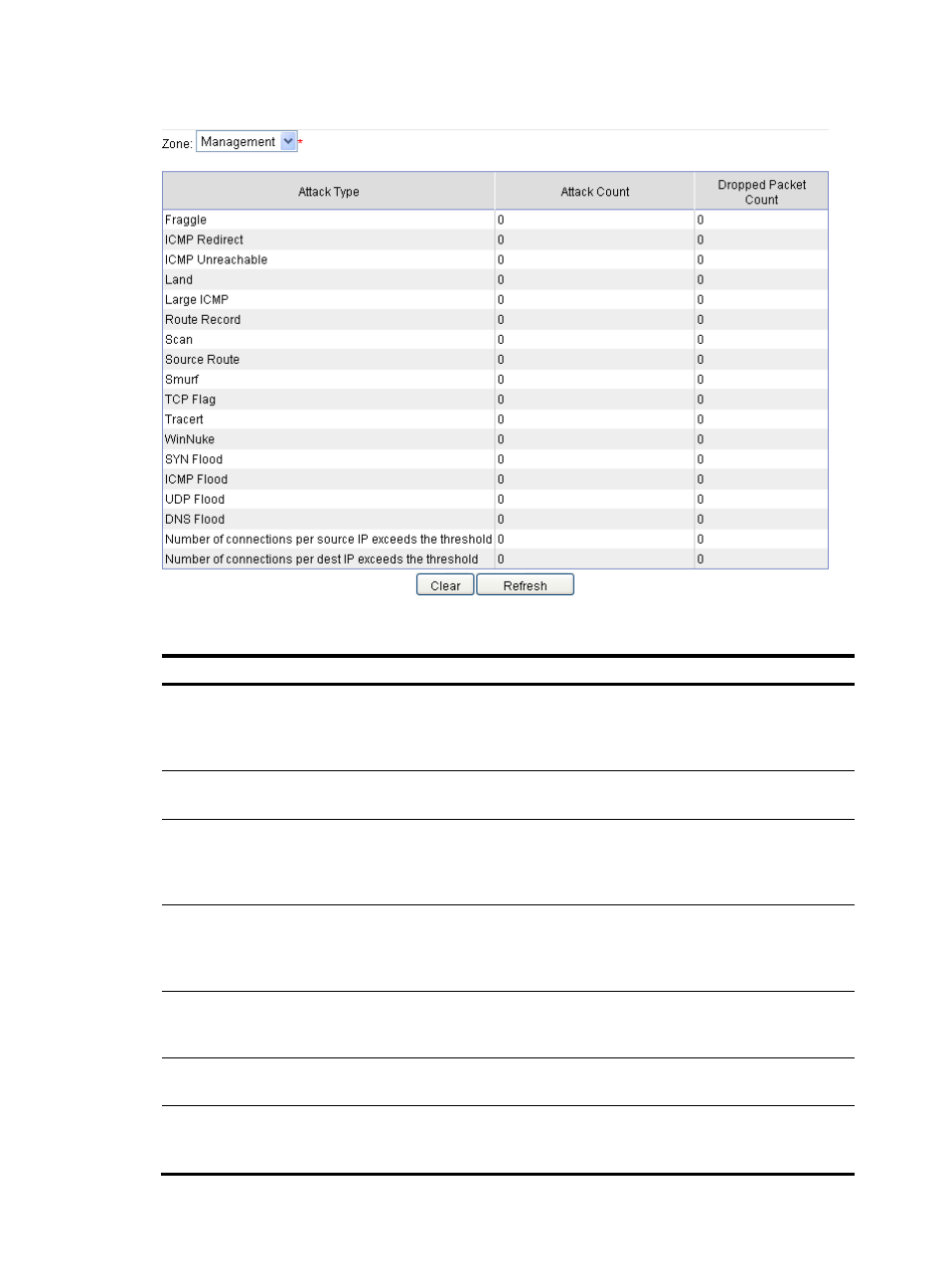
Figure 140 Intrusion detection statistics
Table 34 Attack types description
Attack type
Description
Fraggle
A Fraggle attack occurs when an attacker sends a large number of UDP echo requests
with the UDP port number of 7 or Chargen packets with the UDP port number of 19.
This results in a large quantity of junk replies, and finally exhausts the bandwidth of the
target network.
ICMP Redirect
An ICMP redirect attacker sends ICMP redirect messages to a target to modify its
routing table. This interferes with the normal forwarding of IP packets.
ICMP Unreachable
Upon receiving an ICMP unreachable response, some systems conclude that the
destination is unreachable and drop all subsequent packets destined for the
destination. By sending ICMP unreachable packets, an ICMP unreachable attacker
can cut off the connection between the target host and the network.
Land
A Land attack occurs when an attacker sends a great number of TCP SYN packets with
both the source and destination IP addresses specified as the IP address of the target.
This exhausts the half-open resources of the victim, and disables the target from
working properly.
Large ICMP
For some hosts and devices, large ICMP packets cause a memory allocation error and
crash down the protocol stack. A large ICMP attacker sends large ICMP packets to a
target to make it crash down.
Route Record
A route record attack exploits the route record option in the IP header to probe the
topology of a network.
Scan
A scanning attack probes the addresses and ports on a network to identify the hosts
attached to the network and the application ports available on the hosts. Then, it
figures out the topology of the network, enabling it to prepare for further attacks.
