H3C Technologies H3C SecBlade LB Cards User Manual
Page 236
225
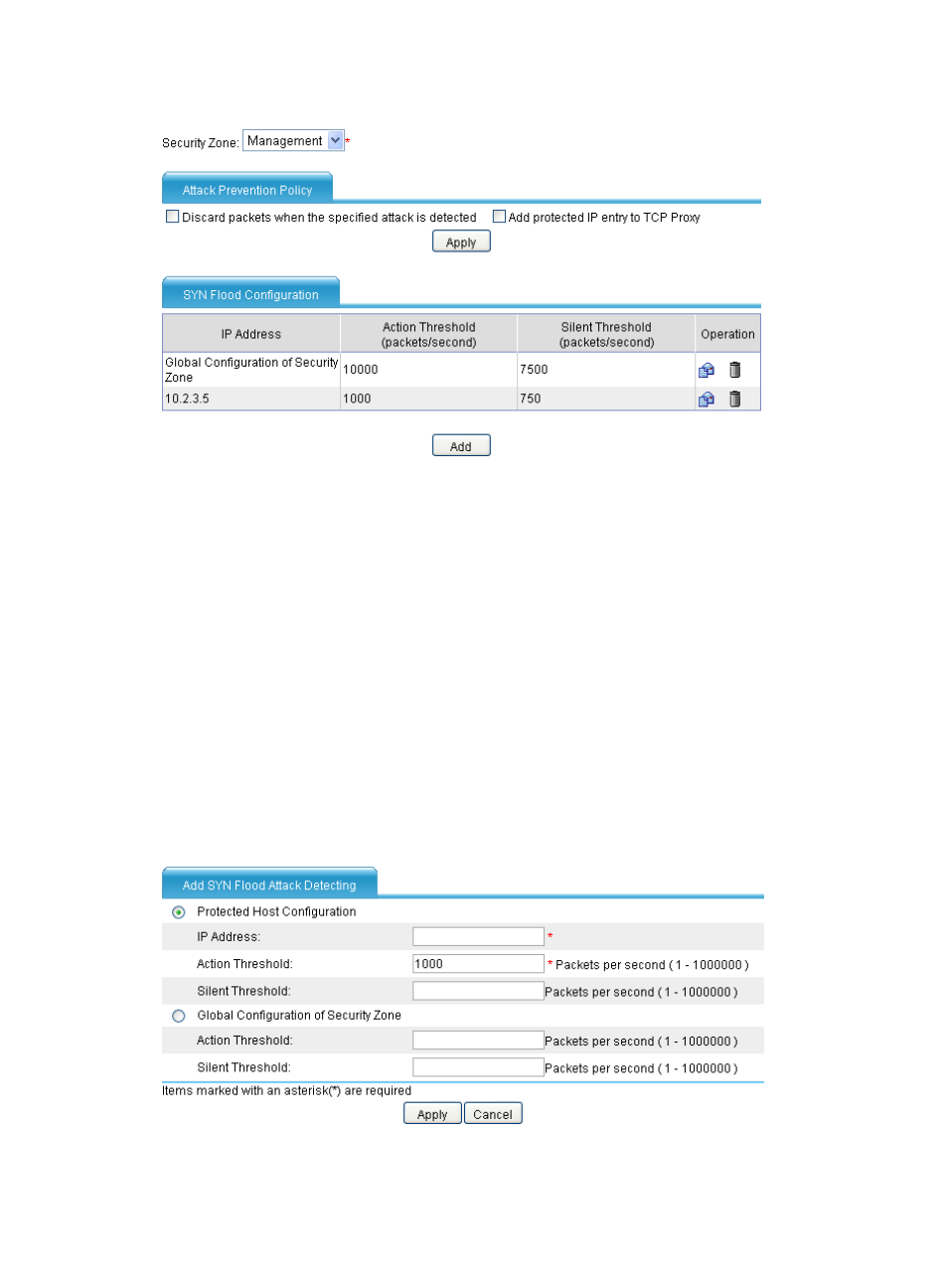
Figure 114 SYN flood detection configuration page
2.
Select a security zone.
3.
In the Attack Prevention Policy area, specify the protection actions to be taken upon detection of a
SYN flood attack for the specified security zone. Click Apply.
If you do not select any option, the device only collects SYN flood attack statistics depending on
your configuration. The available protection actions include:
{
Discard packets when the specified attack is detected. If detecting that a protected object in the
security zone is under SYN flood attack, the device drops the TCP connection requests to the
protected host to block subsequent TCP connections.
{
Add protected IP entry to TCP Proxy. If detecting that a protected object in the security zone is
under SYN flood attack, the device adds the target IP address to the protected IP list on the TCP
proxy as a dynamic one, setting the port number as any. If TCP proxy is configured for the
security zone, all TCP connection requests to the IP address will be processes by the TCP proxy
until the protected IP entry gets aged out. If you select this option, configure the TCP proxy
feature on the page you can enter after selecting Security > Intrusion Detection > TCP Proxy.
4.
In the SYN Flood Configuration area, click Add.
Figure 115 Adding a SYN flood detection rule
5.
Configure a SYN flood detection rule, as described in
.
