Certificate request from an rsa keon ca server – H3C Technologies H3C SecBlade LB Cards User Manual
Page 138
127
Certificate request from an RSA Keon CA server
1.
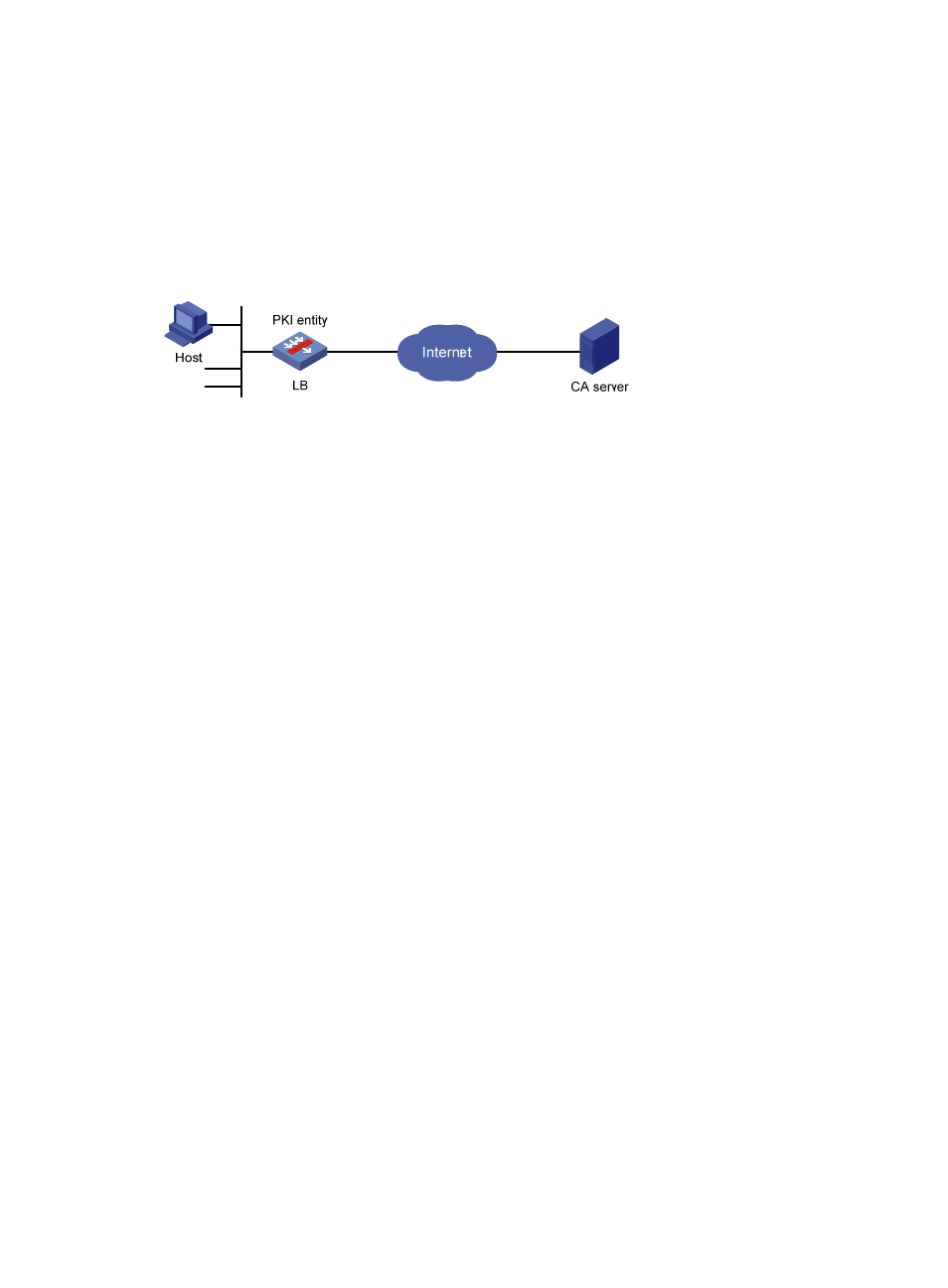
Network requirements
As shown in
, configure the LB product working as the PKI entity, so that:
•
The LB product submits a local certificate request to the CA server, which runs the RSA Keon
software.
•
The LB product retrieves CRLs for certificate verification.
Figure 60 Network diagram
2.
Configuring the CA server
a.
Create a CA server named myca.
In this example, you must first configure the basic attributes of Nickname and Subject DN on the
CA server: the nickname is the name of the trusted CA, and the subject DN is the DN attributes
of the CA, including the common name (CN), organization unit (OU), organization (O), and
country (C). Leave the default values of the other attributes.
b.
Configure extended attributes.
After configuring the basic attributes, configure the parameters on the Jurisdiction
Configuration page of the CA server. This includes selecting the proper extension profiles,
enabling the SCEP autovetting function, and adding the IP address list for SCEP autovetting.
c.
Configure the CRL publishing behavior.
After completing the configuration, perform CRL related configurations.
In this example, select the local CRL publishing mode of HTTP and set the HTTP URL to
http://4.4.4.133:447/myca.crl.
After the configuration, make sure the system clock of the LB product is synchronous to that of the CA, so
that the LB product can request the certificate and retrieve the CRLs properly.
3.
Configure the LB product
a.
Create a PKI entity:
{
From the navigation tree, select Security > Certificate Management > Entity.
{
Click Add.
{
Enter aaa as the PKI entity name, enter device as the common name, and click Apply.
