PLANET FGSW-2840 User Manual
Page 95
User’s Manual of FGSW-2840 / FGSW-4840S
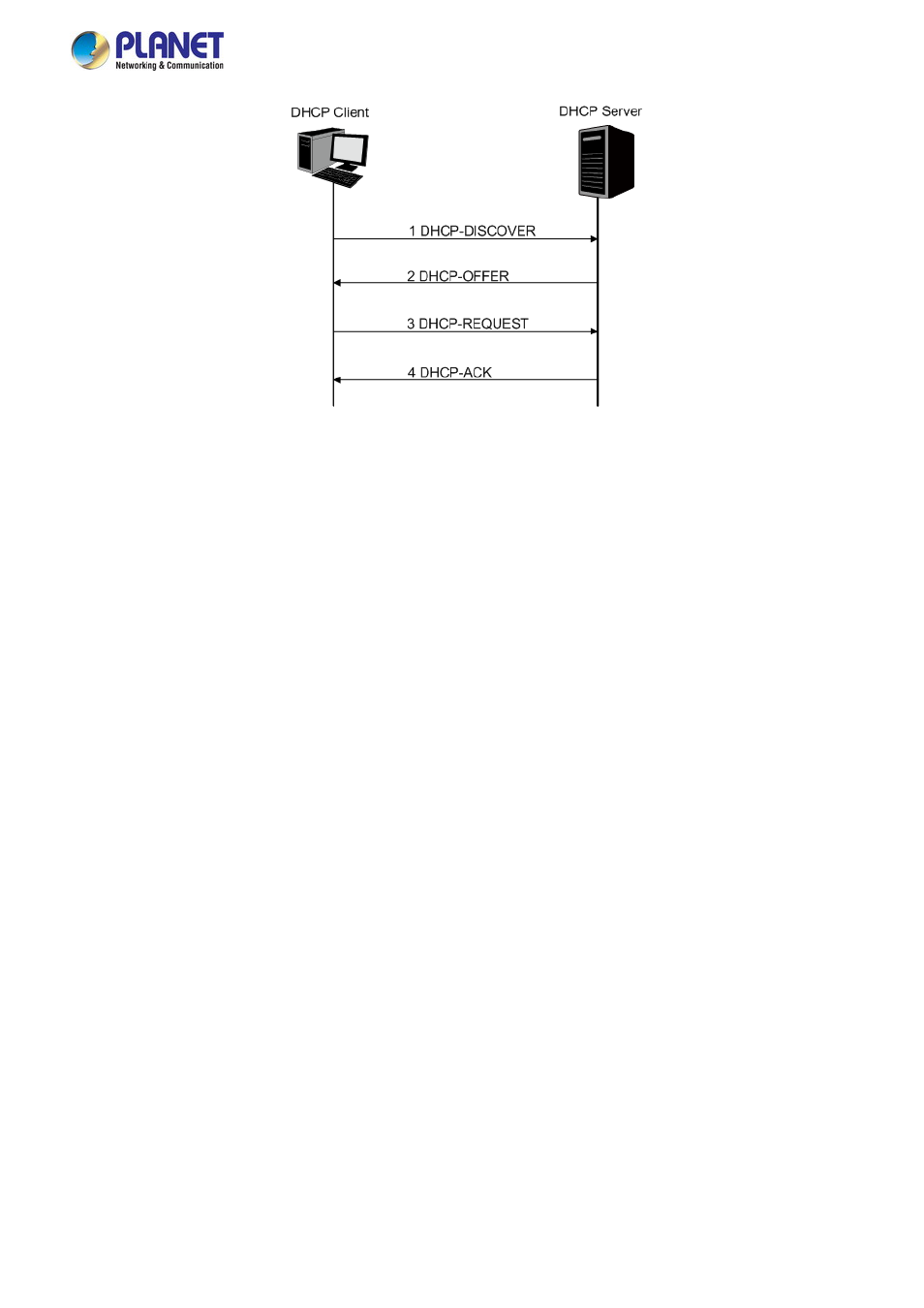
Figure 4-3-22:
Interaction between a DHCP Client and a DHCP Serve
r
(
1)
DHCP-DISCOVER Stage:
The Client broadcasts the DHCP-DISCOVER packet to find the DHCP server.
(
2)
DHCP-OFFER Stage:
Upon receiving the DHCP-DISCOVER packet, the DHCP server selects an IP address from the
IP pool according to the assigning priority of the IP addresses and replies to the client with DHCP-OFFER packet
carrying the IP address and other information.
(
3)
DHCP-REQUEST Stage:
In the situation that there are several DHCP servers sending the DHCP-OFFER packets, the
client will only respond to the first received DHCP-OFFER packet and broadcast the DHCP-REQUEST packet which
includes the assigned IP address of the DHCP-OFFER packet.
(
4)
DHCP-ACK Stage:
Since the DHCP-REQUEST packet is broadcasted, all DHCP servers on the network segment can
receive it. However, only the requested server processes the request. If the DHCP server acknowledges assigning this
IP address to the client, it will send the DHCP-ACK packet back to the client. Otherwise, the Server will send the
DHCP-NAK packet to refuse assigning this IP address to the client.
DHCP Cheating Attack
During the working process of DHCP, generally there is no authentication mechanism between Server and Client. If there are
several DHCP servers in the network, network confusion and security problem will happen. The common cases incurring the
illegal DHCP servers are the following two:
(
1)
It’s common that the illegal DHCP server is manually configured by the user by mistake.
(
2)
Hacker exhausted the IP addresses of the normal DHCP server and then pretended to be a legal DHCP server to
assign the IP addresses and the other parameters to Clients. For example, hacker used the pretended DHCP server to
assign a modified DNS server address to users so as to induce the users to the evil financial website or electronic
trading website and cheat the users of their accounts and passwords. The following figure illustrates the DHCP
Cheating Attack implementation procedure.
95
