Setting the shared keys for radius packets – H3C Technologies H3C S7500E Series Switches User Manual
Page 39
2-10
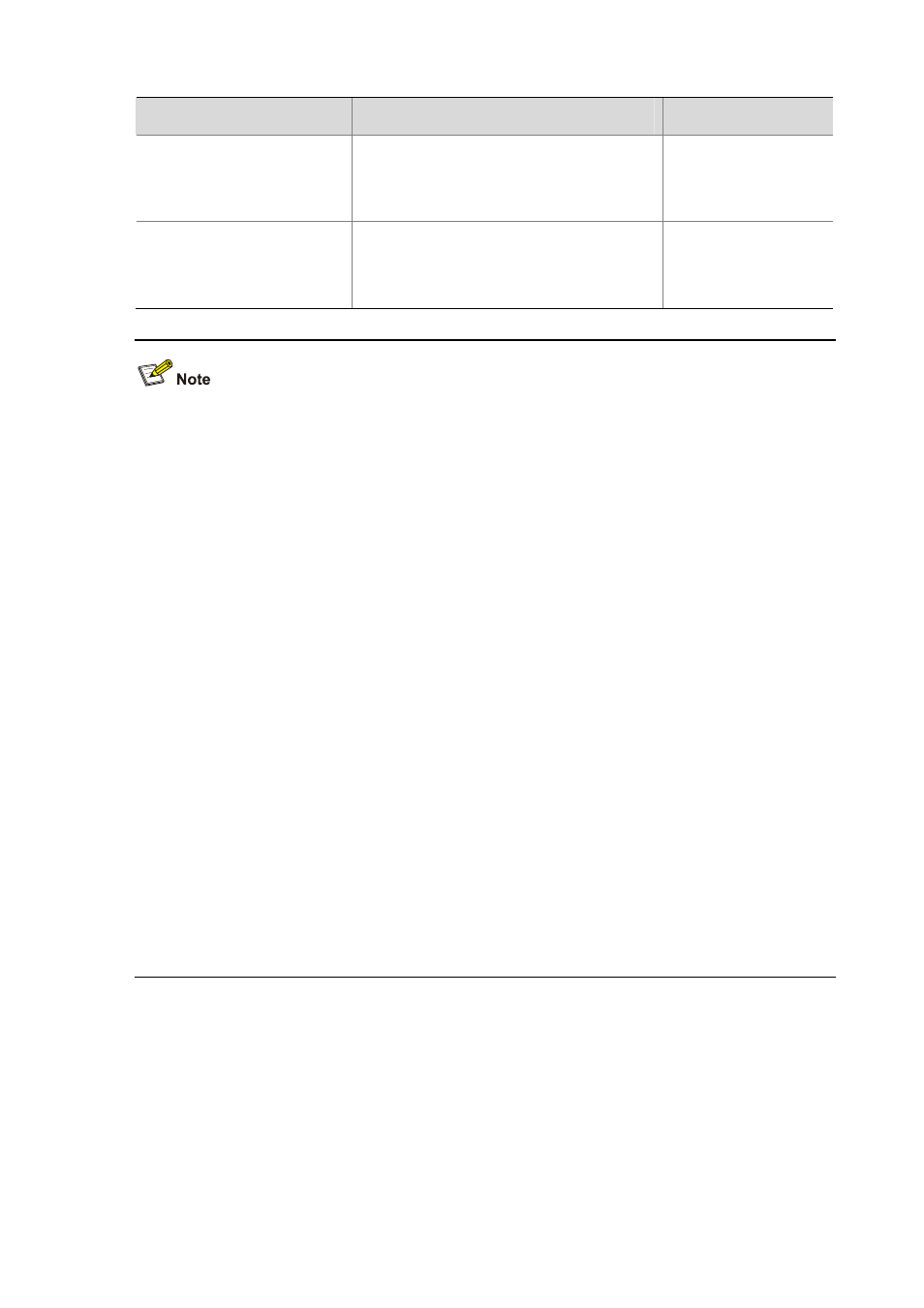
To do…
Use the command…
Remarks
Set the maximum number of
stop-accounting request
transmission attempts
retry stop-accounting retry-times
Optional
500 by default
Set the maximum number of
real-time accounting request
transmission attempts
retry realtime-accounting retry-times
Optional
5 by default
z
If both the primary and secondary accounting servers are specified, the secondary one is used
when the primary one is not reachable.
z
It is recommended to specify only the primary RADIUS accounting server if backup is not
required.
z
In practice, you can specify two RADIUS servers as the primary and secondary accounting
servers respectively, or specify one server to function as the primary accounting server in a
scheme and the secondary accounting server in another scheme. Besides, because RADIUS
uses different UDP ports to receive authentication/authorization and accounting packets, the port
for authentication/authorization must be different from that for accounting.
z
You can enable the device to buffer stop-accounting requests to which no responses are received,
allowing the device to buffer and resend a stop-accounting request until it receives a response or
the number of transmission attempts reaches the configured limit. In the latter case, the device
discards the packet.
z
You can set the maximum number of real-time accounting request transmission attempts on the
device, allowing the device to disconnect a user when the number of accounting request
transmission attempts for the user reaches the limit but it still receives no response to the
accounting request.
z
The IP addresses of the primary and secondary accounting servers cannot be the same.
Otherwise, the configuration fails.
z
Currently, RADIUS does not support keeping accounts on FTP users.
z
All servers for authentication/authorization and accountings, primary or secondary, must use IP
addresses of the same IP version.
Setting the shared keys for RADIUS packets
The RADIUS client and RADIUS server use the MD5 algorithm to encrypt packets exchanged
between them and use shared keys to verify the packets. They must use the same shared key for the
same type of packets.
Follow these steps to set the shared keys for RADIUS packets:
