Data encryption key life cycle management – Brocade Fabric OS Encryption Administrator’s Guide Supporting HP Secure Key Manager (SKM) and HP Enterprise Secure Key Manager (ESKM) Environments (Supporting Fabric OS v7.2.0) User Manual
Page 29
Fabric OS Encryption Administrator’s Guide (SKM/ESKM)
9
53-1002923-01
Data encryption key life cycle management
1
Data encryption key life cycle management
Data encryption keys (DEKs) are generated by the encryption engine. Data is encrypted and
decrypted using the same DEK, so a DEK must be preserved at least long enough to decrypt the
ciphertext that it created. The length of time data is stored before it is retrieved can vary greatly,
and some data may be stored for years or decades before it is accessed. To be sure the data
remains accessible, DEKs may also need to be stored for years or decades. Key management
systems provide life-cycle management for all DEKs created by the encryption engine. Key
management systems are provided by third-party vendors.
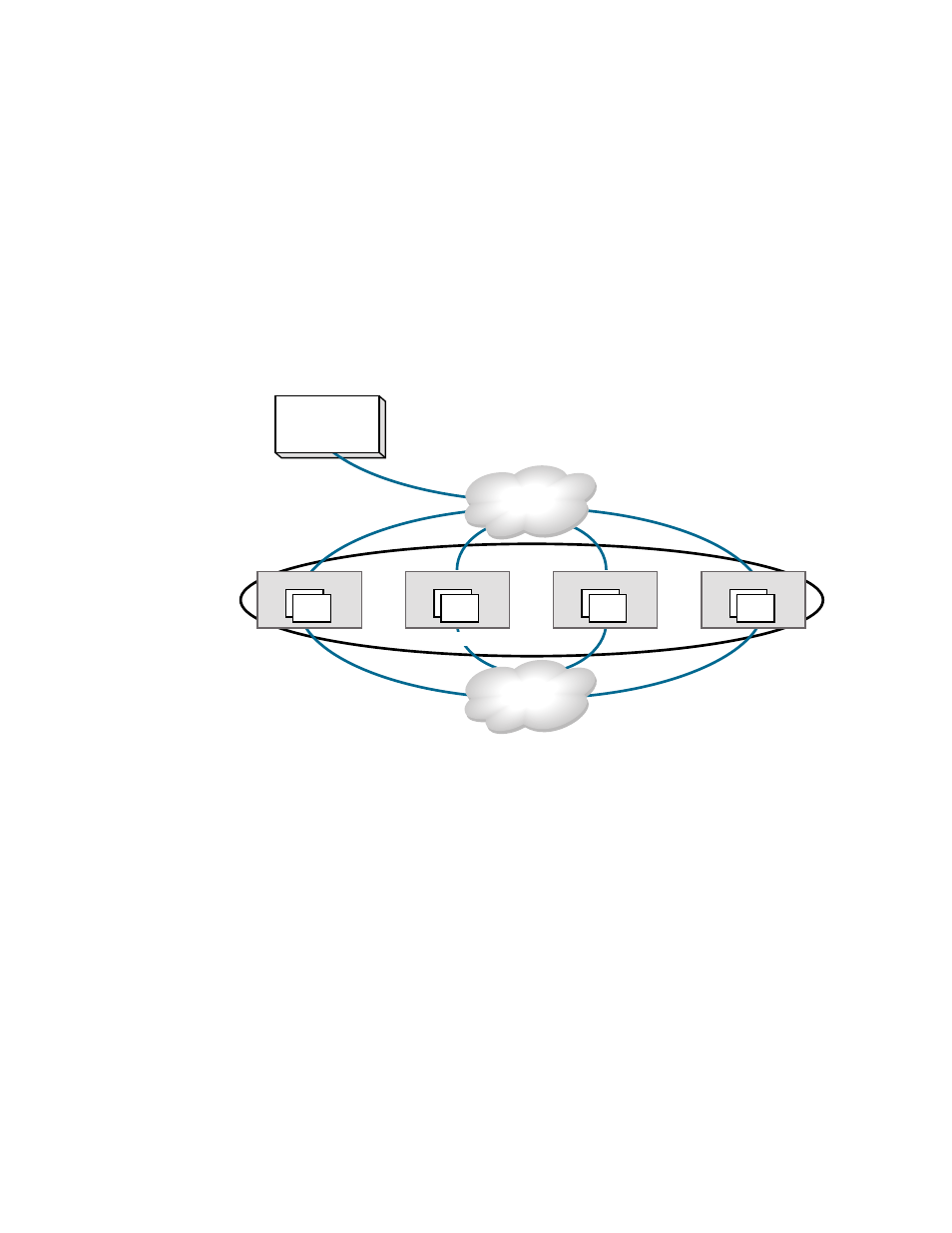
shows the relationship of the LAN connections to the key vault and between encryption
nodes.
FIGURE 4
LAN connections to the key vault, and between encryption nodes
Regardless of the length of the life cycle, there are four stages in the life of a DEK, as shown in
. A DEK is created by an encryption engine, distributed, then stored in a key vault. The key
is used to encrypt and decrypt data at least once, and possibly many times. A DEK may be
configured to expire in a certain time frame to avoid becoming compromised. Under those
conditions, it must be used one more time to decrypt the data, and the resulting cleartext is
encrypted with a new key (rekeyed).
Node 1
Key Management
System
EE
Node 2
Group Leader
Encryption Group
EE
Node 3
EE
Node 4
EE
IO Sync LAN
LAN
