Dual fabric deployment - ha and dek cluster – Brocade Fabric OS Encryption Administrator’s Guide Supporting HP Secure Key Manager (SKM) and HP Enterprise Secure Key Manager (ESKM) Environments (Supporting Fabric OS v7.2.0) User Manual
Page 227
Fabric OS Encryption Administrator’s Guide (SKM/ESKM)
207
53-1002923-01
Dual fabric deployment - HA and DEK cluster
4
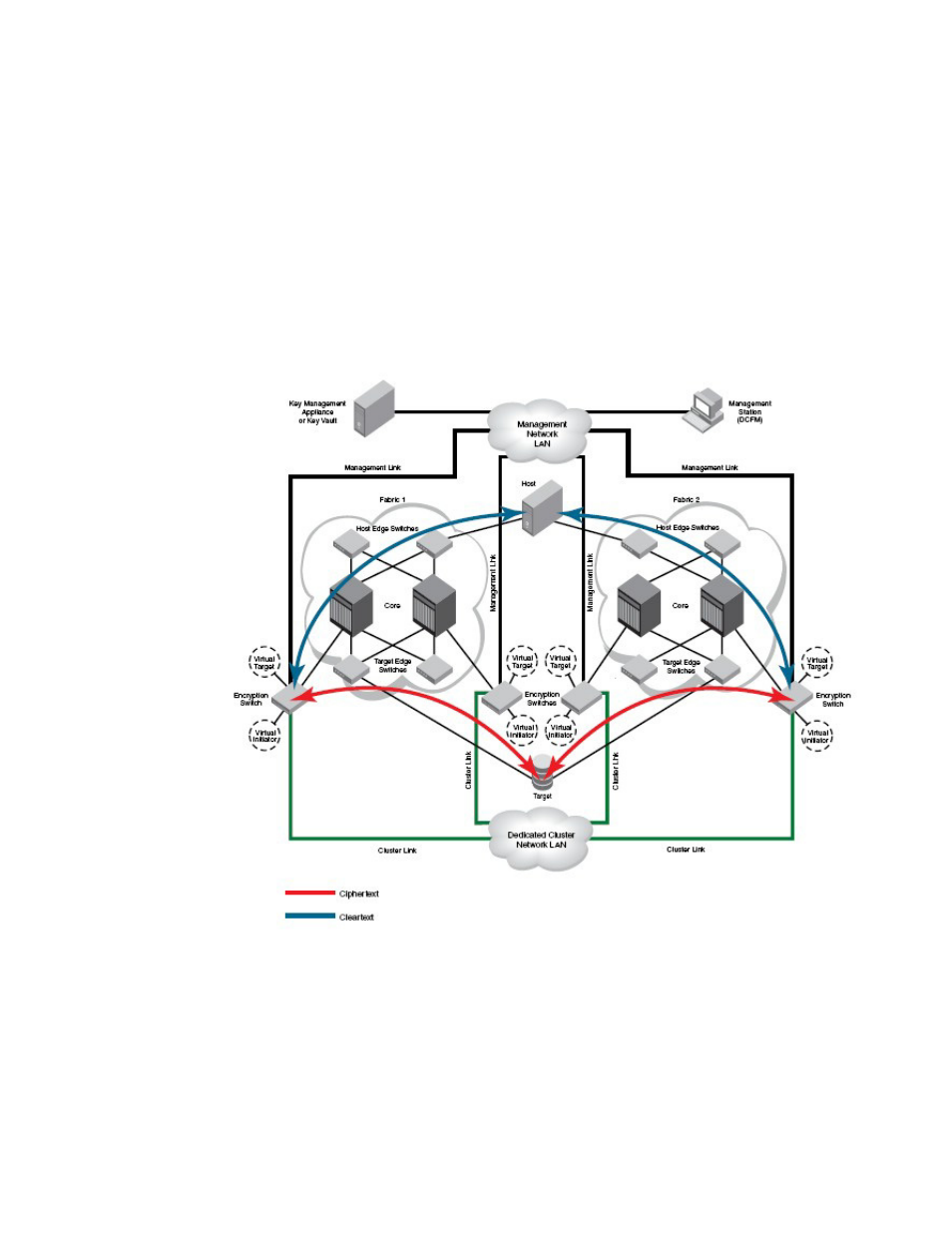
In
, two encryption switches are required, one for each target path. The path from host
port 1 to target port 1 is defined in a CryptoTarget container on one encryption switch, and the path
from host port 2 to target port 2 is defined in a CryptoTarget container on the other encryption
switch. This forms a DEK cluster between encryption switches for both target paths. The DEK
cluster handles the target/host path failover along with the failure of either encryption switch.
Dual fabric deployment - HA and DEK cluster
shows an encryption deployment in a dual fabric SAN. Both fabrics have dual core
directors and several host and target edge switches in a highly redundant core-edge topology.
FIGURE 94
Dual fabric deployment - HA and DEK cluster
shows two paths to the target device, one in each fabric. The host also has a path to
each fabric. There are two encryption switches in each fabric, interconnected through a dedicated
cluster LAN. The Ge1 and Ge0 gigabit Ethernet ports on each of these switches are attached to this
LAN. encryption switches 1 and 3 act as a high availability cluster in fabric 1, providing automatic
