Multi-path lun configuration example – Brocade Fabric OS Encryption Administrator’s Guide Supporting HP Secure Key Manager (SKM) and HP Enterprise Secure Key Manager (ESKM) Environments (Supporting Fabric OS v7.2.0) User Manual
Page 202
182
Fabric OS Encryption Administrator’s Guide (SKM/ESKM)
53-1002923-01
Configuring a multi-path Crypto LUN
3
To avoid the risk of data corruption, you must observe the following rules when configuring
multi-path LUNs:
•
During the initiator-target zoning phase, complete in sequence all zoning for ALL hosts that
should gain access to the targets before committing the zoning configuration.
•
Complete the CryptoTarget container configuration for ALL target ports in sequence and add
the hosts that should gain access to these ports before committing the container
configuration. Upon commit, the hosts lose access to all LUNs until the LUNs are explicitly
added to the CryptoTarget containers.
•
When configuring the LUNs, the same LUN policies must be configured for ALL paths of ALL
LUNs. Failure to configure all LUN paths with the same LUN policies results in data corruption.
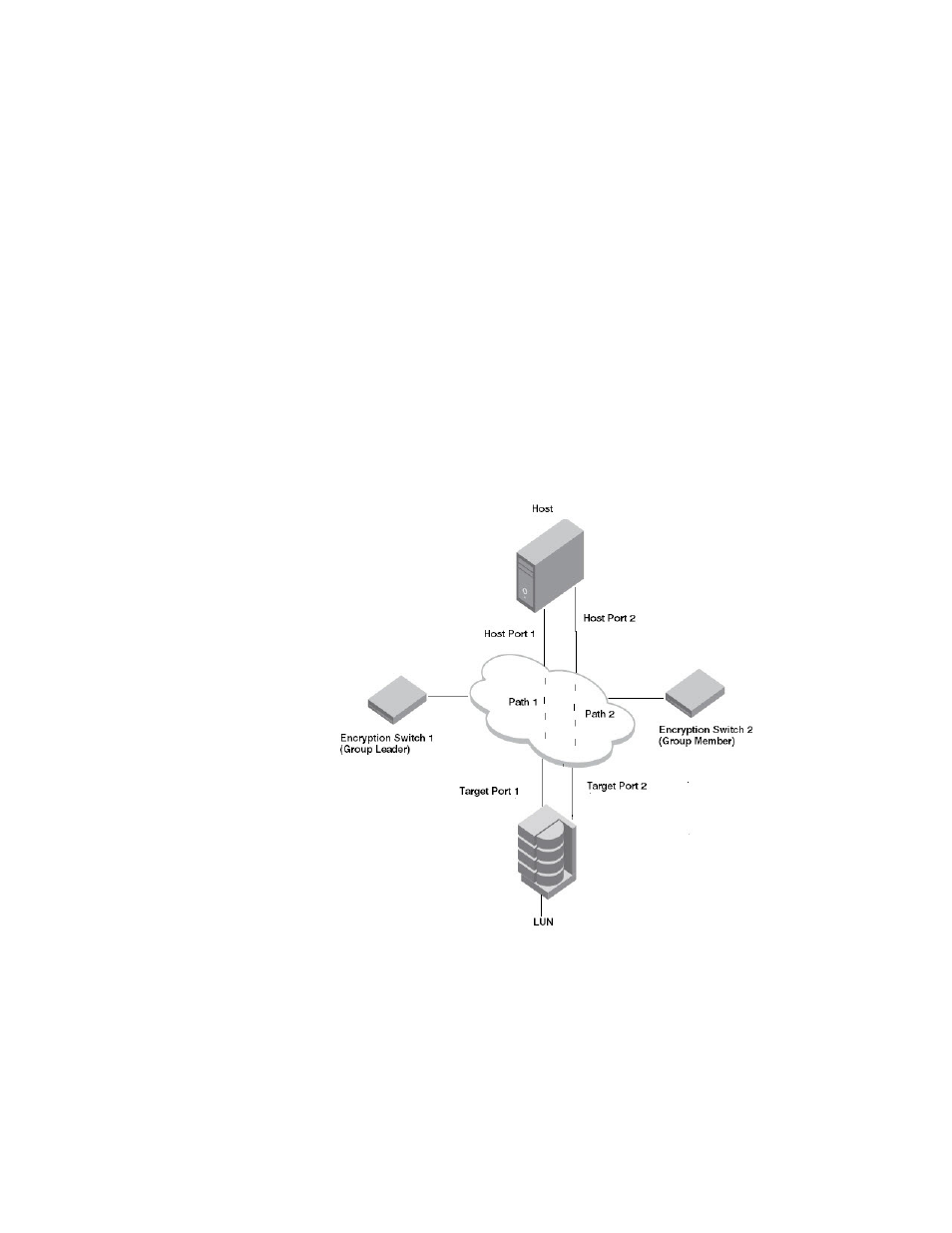
Multi-path LUN configuration example
on page 182 shows a single LUN on a dual-port target that is accessed over two paths by
a dual-port host. The two encryption switches form an encryption group and an HA cluster. The
following example illustrates a simplified version of a multi-path LUN configuration.
FIGURE 90
A LUN accessible through multiple paths
The following steps may be used to configure multiple path access to the LUN in
.
1. Create zoning between host port 1 and target port 1. Refer to the section
on page 164 for instructions.
2. Create zoning between host port 2 and target port 2. Refer to the section
on page 164 for instructions.
