Transparent mode, Configuration options, Setup wizard – Fortinet FortiGate 50A User Manual
Page 28: Transparent mode configuration options
28
Fortinet Inc.
Planning the FortiGate configuration
Getting started
You typically use NAT/Route mode when the FortiGate unit is operating as a gateway
between private and public networks. In this configuration, you would create NAT
mode policies to control traffic flowing between the internal, private network and the
external, public network (usually the Internet).
Figure 3: Example NAT/Route mode network configuration
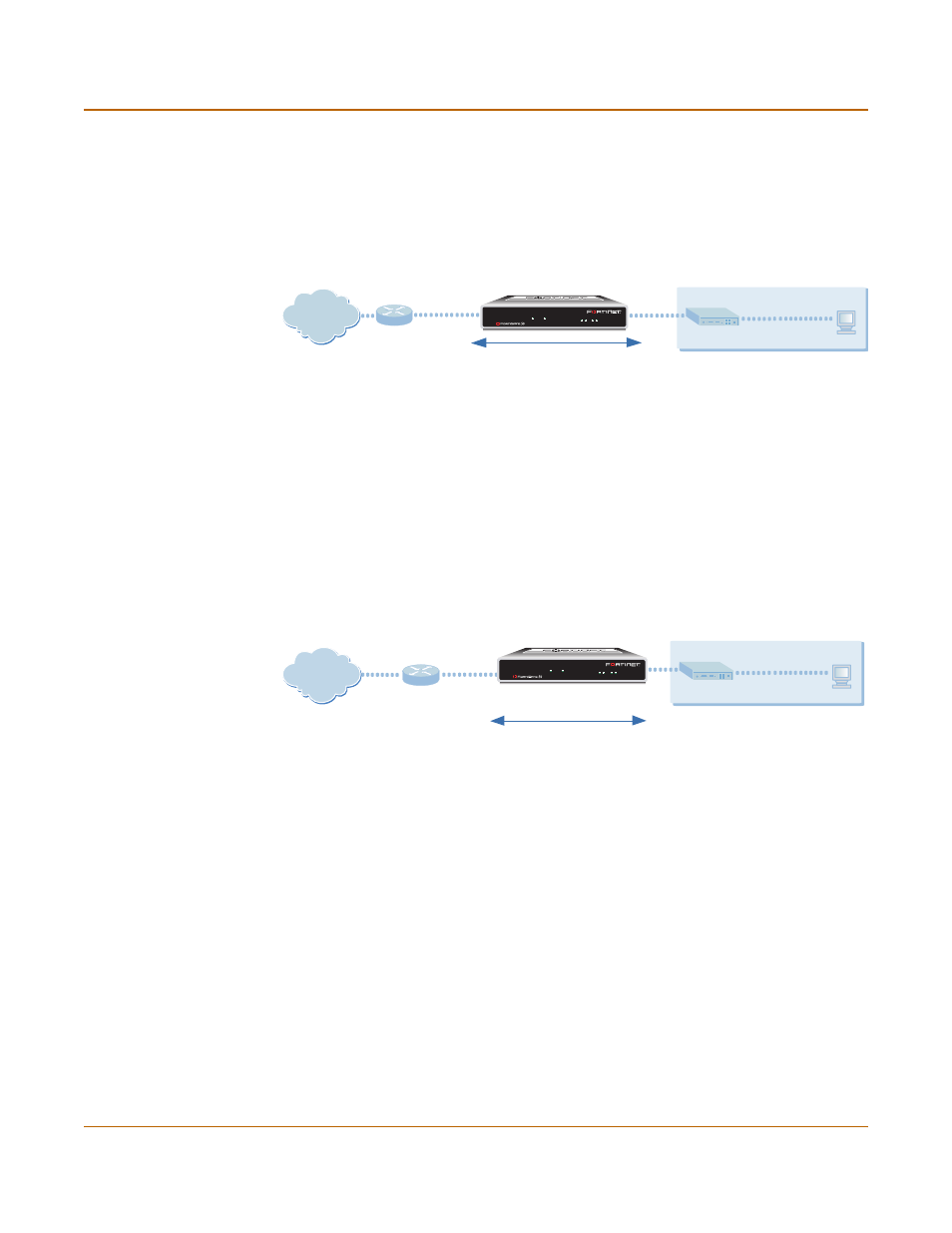
Transparent mode
In Transparent mode, the FortiGate unit is invisible to the network. Similar to a
network bridge, all FortiGate interfaces must be on the same subnet. You only have to
configure a management IP address so that you can make configuration changes.
The management IP address is also used for antivirus and attack definition updates.
You typically use the FortiGate unit in Transparent mode on a private network behind
an existing firewall or behind a router. The FortiGate unit performs firewall functions as
well as antivirus and content scanning but not VPN.
Figure 4: Example Transparent mode network configuration
Configuration options
Once you have selected Transparent or NAT/Route mode operation, you can
complete the configuration plan and begin to configure the FortiGate unit.
You can use the web-based manager setup wizard or the command line interface
(CLI) for the basic configuration of the FortiGate unit.
Setup wizard
If you are configuring the FortiGate unit to operate in NAT/Route mode (the default),
the setup wizard prompts you to add the administration password and internal
interface address. The setup wizard also prompts you to choose either a manual
(static) or a dynamic (DHCP or PPPoE) address for the external interface. Using the
wizard, you can also add DNS server IP addresses and a default route for the external
interface.
FortiGate-50A Unit
in NAT/Route mode
Internal network
Internal
192.168.1.99
192.168.1.3
External
204.23.1.5
NAT mode policies controlling
traffic between internal and
external networks.
POWER
Internet
INTERNAL
EXTERNAL
LINK 100
LINK 100
PWR
STATUS
A
Internal network
10.10.10.3
FortiGate-50A Unit
in Transparent mode
10.10.10.1
Management IP
External
Internal
10.10.10.2
Transparent mode policies
controlling traffic between
internal and external networks
204.23.1.5
(firewall, router)
Gateway to
public network
Internet
INTERNAL
EXTERNAL
LINK 100
LINK 100
PWR
STATUS
A
