2 dhcp snooping typical applications – Amer Networks SS2R48G4i V2 User Manual
Page 177
SS2R24G4i/SS2R48G4i
166
19.2.2 DHCP Snooping Typical Applications
非信任端口
非信任端口
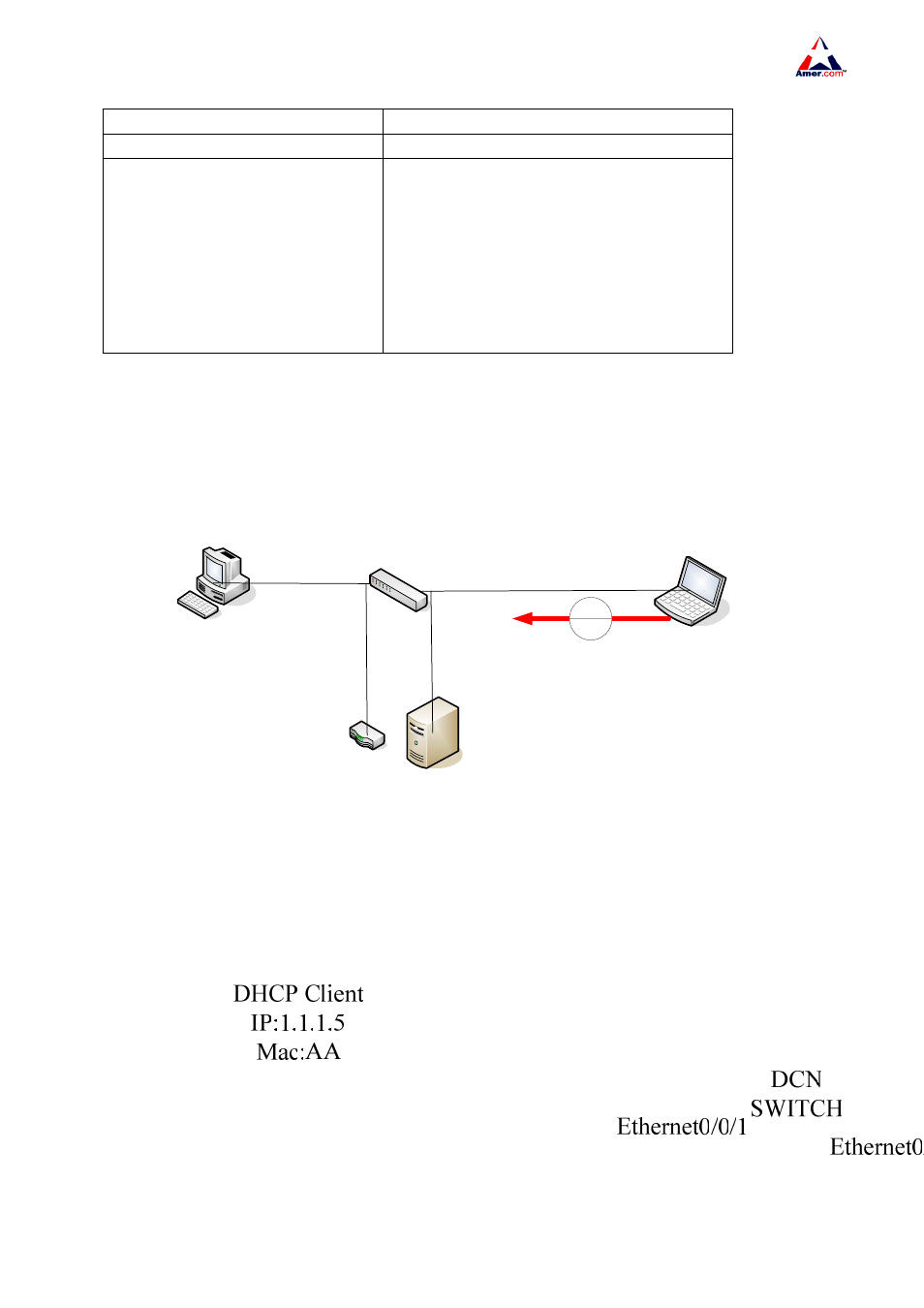
Fig18-1
As showed in the above picture, Mac-AA device is the normal user,connected to the un-trusted
port 0/0/1 of the DCN switch. It acts as DHCP Client, and its IP is 1.1.1.5;DHCP Server and GateWay
connect to the trusted ports 0/0/11 and 0/0/12 of the DCN switch; malicious user Mac-BB connects to
the un-trusted port 0/0/10, trying to fake a DHCP Server(by sending DHCPACK). Configuring DHCP
Snooping on the switch will effectively discover and block such network attacks.
The followings are the configuration sequence
switch#
switch#config
switch(Config)#ip dhcp snooping
switch(Config)#interface ethernet 0/0/11
switch(Config-Ethernet0/0/11)#ip dhcp snooping trust
switch(Config-Ethernet0/0/11)#exit
switch(Config)#interface ethernet 0/0/12
switch(Config-Ethernet0/0/12)#ip dhcp snooping trust
switch(Config-Ethernet0/0/12)#exit
switch(Config)#interface ethernet 0/0/1-10
switch(Config-Port-Range)#ip dhcp snooping action shutdown
Command Explanation
Admin Mode
Login on
logging source {default |
m_shell|sys_event|anti_attack}
channel { console | logbuff |
loghost | monitor } [ level
{ critical | debugging |
notifications | warnings } [state
{ on | off } ] ]
Please refer to the chapter on system log
