Understanding and creating attribute sets, Understanding and creating attribute sets -16 – Alcatel-Lucent 8950 AAA User Manual
Page 156
............................................................................................................................................................................................................................................................
Understanding and Creating Attribute Sets
Using the 8950 AAA Policy Assistant in Server
Management Tool
9-16
365-360-001R6.0
Issue 1, December 2008
............................................................................................................................................................................................................................................................
Understanding and Creating Attribute Sets
About Attribute Set
8950 AAA uses two key actions during Access-Request processing to authorize users and
configure user sessions upon successful authentications: performing authorization checks
and session provisioning. Attributes contain the information used to support these actions.
Other RADIUS servers generally require that you set this type of information as part of
each user’s profile. With the PolicyAssistant it is possible to create an attribute set for a
policy which contains the information that the server applies to all users of the policy.
Authorization checks are logical tests of information that accompany a user’s access
request or that are known about the request (for example, the date and time a request is
received) against a set of authorization rules. The server tests the information it receives
against verification attributes, also called check-items, stored in an attribute set or possibly
a user’s profile. By including appropriate verification attributes in a policy, a variety of
rules can be enforced. For example, users might be permitted to use ISDN connections,
required to dial-in to a particular phone number, or use a specific access protocol, such as
PPP.
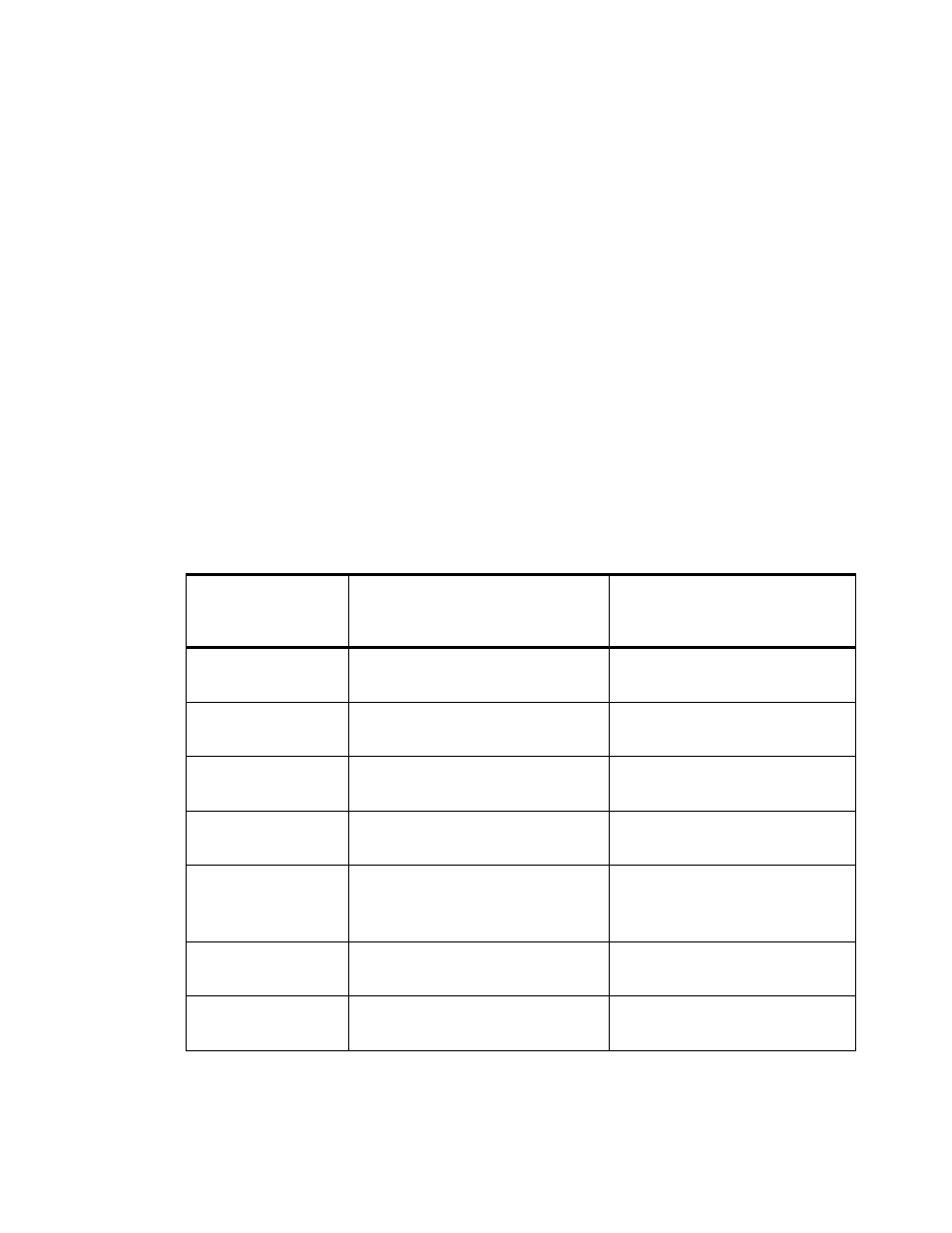
lists attributes commonly used as verification attributes.
Figure 9-9 Sample List of Verification Attributes
Attribute Name
Description of Use of this
Attribute as a Verification
Attribute
Example
NAS-IP-Address
Limits access to requests sent from
a NAS at this IP Address
NAS-IP-Address =
10.0.1.2
Service-Type
Only allow requests of this service
type
Service-Type = Framed-
Protocol
Framed-Protocol
Only allows requests that only use
the specified Framed-Protocol
Framed-Protocol = PPP
Called-Station-Id
Limits access to sessions that were
made through this phone number.
Called-Station-Id =
5105551212
NAS-Port-Type
Only accept this type of
connection. (i.e., ISDN or Async—
Analog).
NAS-Port-Type = Async
Expiration
Rejects Access-Requests placed
after the specified date.
Expiration = “Mar 27
2005”
Activation
Rejects Access-Requests placed
before the specified date.
Activation = “Dec 25
2005”
