Available operations and ikeys required – Nortel Networks NN46120-104 User Manual
Page 31
Available Operations and iKeys Required
31
by the Setup utility, the wrap key is split onto these two iKeys. When
adding an additional ASA 310-FIPS to the cluster, the CODE-SO and the
CODE-USER iKeys are used to transfer the wrap key to the HSM cards
on NVG device(s) that have been added. Once the wrap key has been
transferred, all synchronization of sensitive information within the cluster
takes place transparently to the user.
No passwords are associated with the CODE-SO and CODE-USER
iKeys. However, for all operations that involves using the CODE-SO and
CODE-USER iKeys, these keys are used in addition to the HSM-SO
and HSM-USER iKeys (which in turn require the correct passwords for
successful authentication).
CAUTION
If you enter the wrong password for the HSM-USER fifteen (15) times in a row,
the HSM-USER iKey will be rendered unusable. This is due to the strict security
specifications placed on the ASA 310-FIPS.
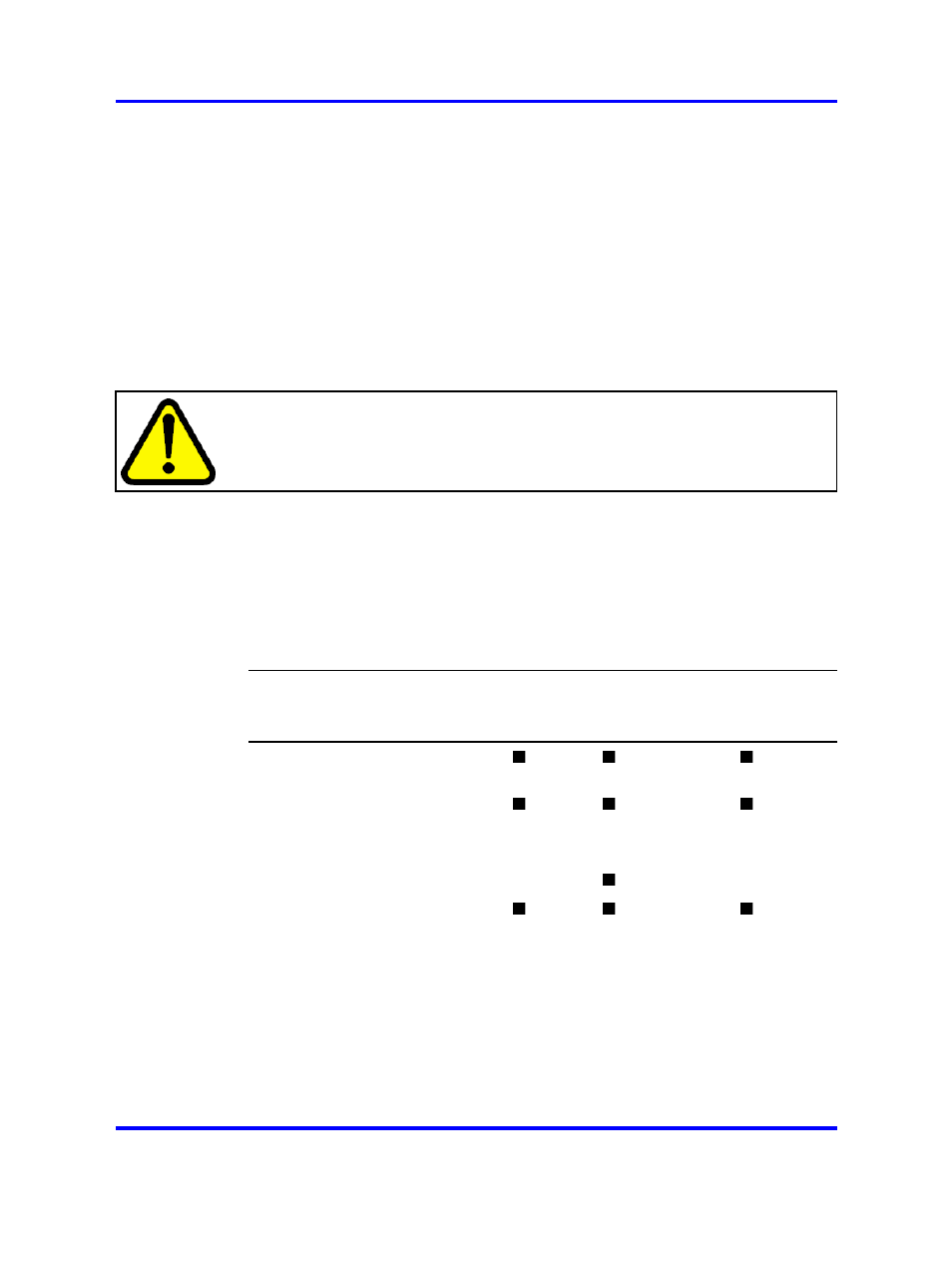
Available Operations and iKeys Required
For information about the type of iKeys required to perform a specific
operation, see
Table 2 "Available Operations and iKeys Required" (page
.
Table 2
Available Operations and iKeys Required
Type of iKey Required
Operation Performed
HSM-SO
HSM-US
ER
CODE-SO and
CODE-USER
Installing a new ASA
310-FIPS in a new cluster
Adding an ASA 310-FIPS to
an existing cluster
Logging in to the HSM card
Splitting the wrap key onto a
pair of CODE iKeys
Nortel VPN Gateway
User Guide
NN46120-104
02.01
Standard
14 April 2008
Copyright © 2007-2008 Nortel Networks
.
