0 roles and services 243 – Nortel Networks NN46120-104 User Manual
Page 243
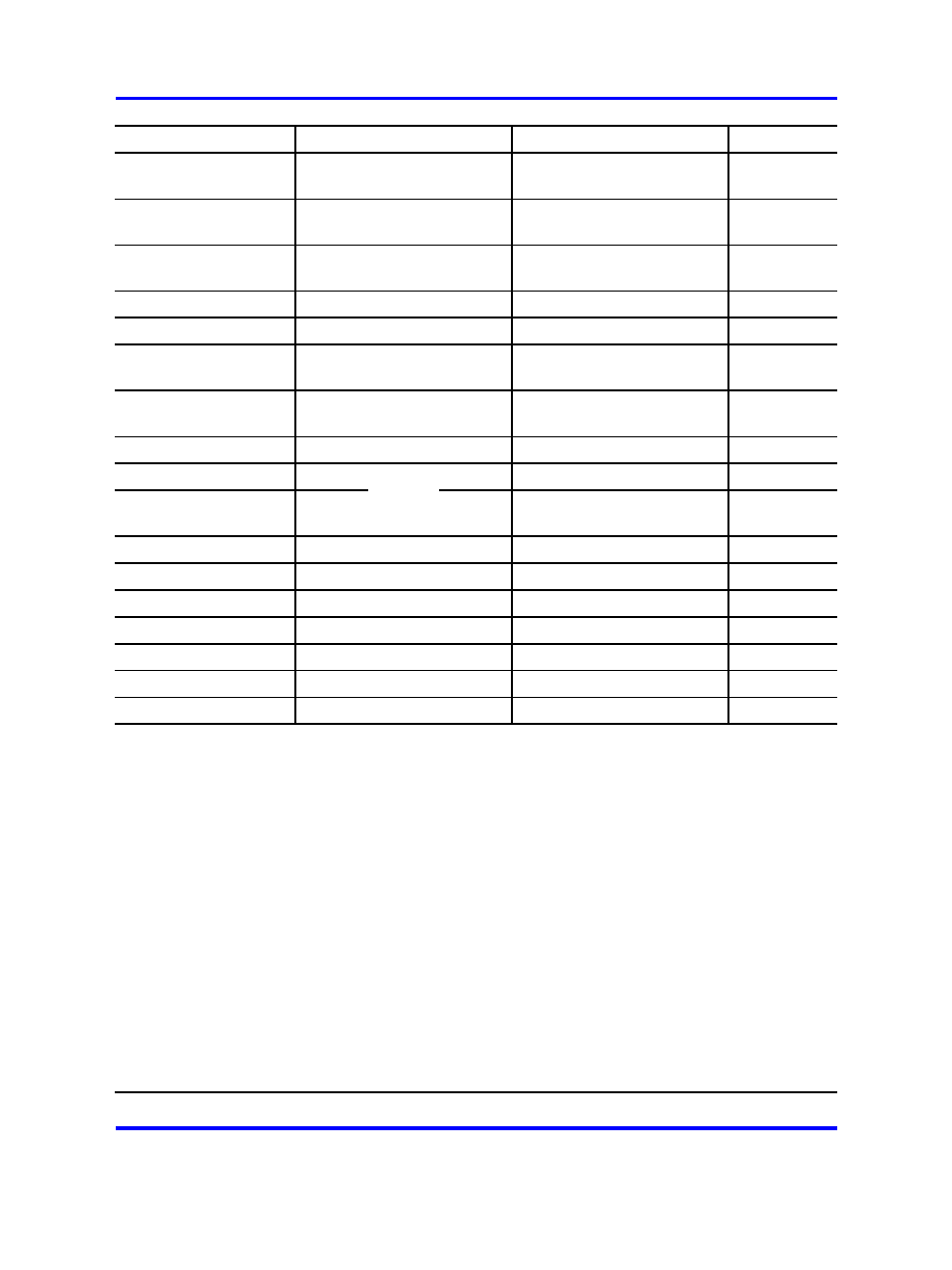
9.0 Roles and Services
243
Service
FIPS140-1 Level 3 Mode
Non- FIPS140-1 Mode
Not auth
enticated
User
Role
SO Role
Not auth
enticated
User
Role
SO Role
SRDIs Access
ed
Modular Exponentiation
using CRT (note 3)
YES
YES
YES
YES
YES
Yes
None
Modular Exponentiation
(note 3)
YES
YES
YES
YES
YES
YES
None
RSA Encrypt (note 8)
NO
NO
NO
NO
YES
YES
EPK (use)
RSA Decrypt (note 8)
NO
NO
NO
NO
YES
YES
DPK (use)
Digital Signature Standard
Sign (note 1)
NO
NO
NO
YES
YES
YES
None
Digital Signature Standard
Verification (note 1)
NO
NO
NO
YES
YES
YES
None
Self-test
YES
YES
YES
YES
YES
YES
None
Firmware Update
NO
NO
YES
NO
NO
YES
None
Generate Random Number
YES
YES
YES
YES
YES
YES
PRNGKey (crea
te, destroy)
Get Configuration
YES
YES
YES
YES
YES
YES
None
Get Status
YES
YES
YES
YES
YES
YES
None
Verify Firmware
Image
NO
NO
YES
NO
NO
YES
SHA1 Hash
NO
YES
YES
YES
YES
YES
None
SHA1 HMAC (note 1)
NO
NO
NO
YES
YES
YES
None
MD5 Hash
NO
NO
NO
YES
YES
YES
None
MD5 HMAC (note 1)
NO
NO
NO
YES
YES
YES
None
Note 1 =
The key for these commands is input through the PCI bus (data input interface)
Note 2 =
This is a PKCS 12 method for deriving a 3DES key from a password, salt and iteration count.
Note 3 =
The Exponentiation Using CRT and Exponentiation functions are generic math functions; all
parameters are input through the PCI interface (data input interface).
Note 4 =
When operating in the FIPS140-1 mode, it is not possible for secret keys, private keys or critical
security parameters to cross the PCI bus without being wrapped (encrypted) using the Key-Wrapping
Key.
Note 5 =
User Login is the process that takes the board from an unauthenticated state to the authenticated
state. Only one user may be authenticated at a particular time. Consequently, the User Login process
cannot be started from the authenticated state. Nonetheless, the User Login process cannot be
completed successfully without authentication.
Note 6 =
This command is used for generating the key-wrapping-key.
Note 7 =
When the board is in the zeroized state, it is possible to for an unauthenticated user to uninitialize
the board.
Note 8 =
These operations must access stored cryptographic keys. The keys may not be input through the
PCI interface.
Nortel VPN Gateway
User Guide
NN46120-104
02.01
Standard
14 April 2008
Copyright © 2007-2008 Nortel Networks
.
