Rsh configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 53
2
.
NOTE:
If RSH daemon authentication is enabled on the remote host, you must provide the username configured
on the remote host in advance
RSH Configuration Example
Network requirements
As shown in
, Device acts as the RSH client. The remote host runs Windows 2000 and has had
RSH daemon service started. The requirement is to set the time of the host remotely from Device.
NOTE:
Windows NT, 2000, XP, and 2003 are shipped with no RSH daemon. Therefore, the RSH daemon must
be separately obtained and installed on the remote host.
Figure 2 Network diagram for RSH configuration
Configuration Procedure
On the remote host, check that the RSH daemon has been installed and started properly:
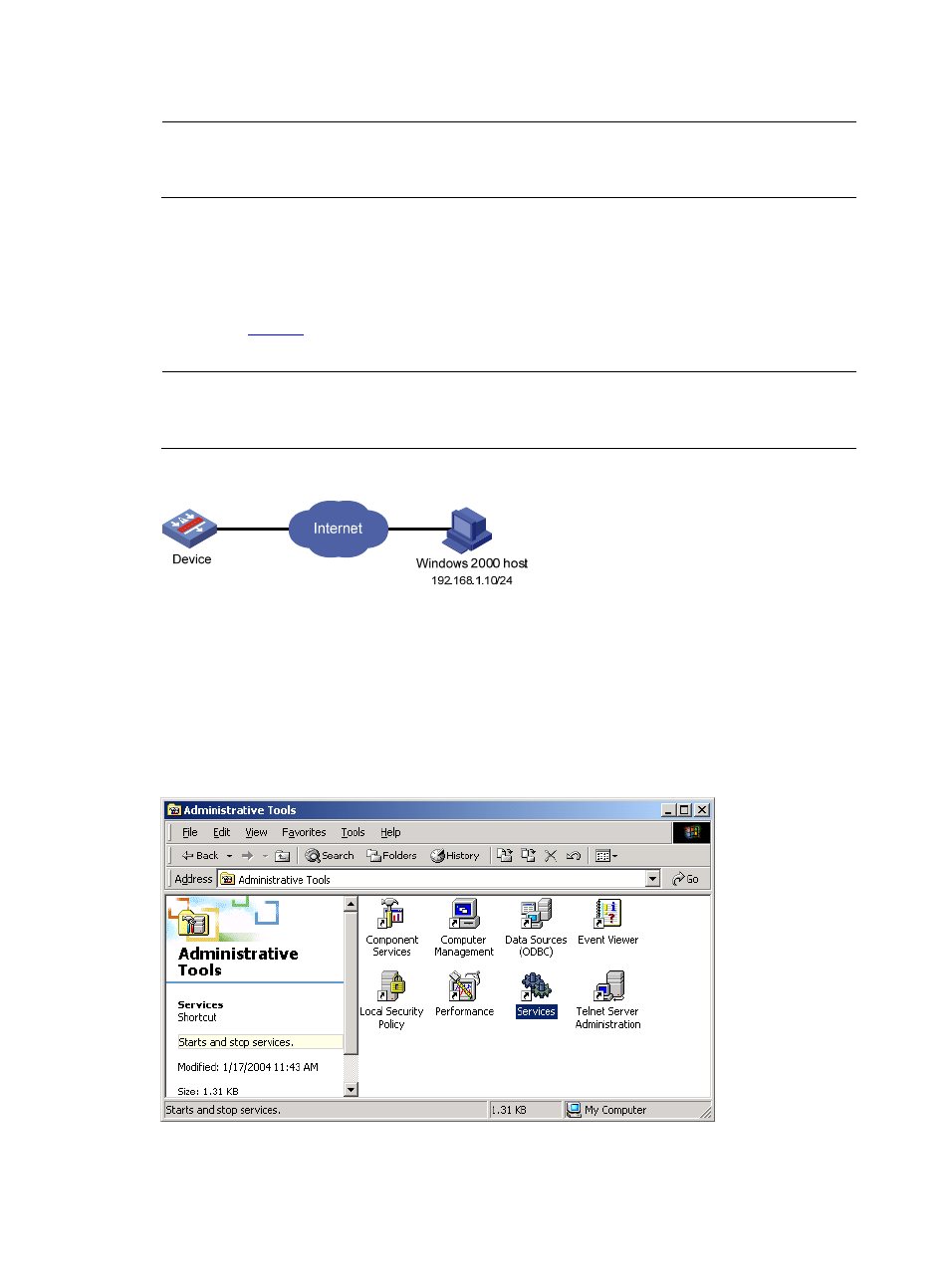
Step1
From the Windows Control Panel, open the Administrative Tools folder. (For Windows XP, if you use
the category view of the Control Panel window, select Administrative Tools from Performance
and Maintenance.)
Figure 3 Administrative Tools folder
Step2
Double-click the Services icon to display the Services window.
