Ipsec configuration examples, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 152
24
To do…
Use the command…
Remarks
Clear IPsec statistics
reset ipsec statistics
Available in user view
IPsec Configuration Examples
Example for Establishing an IPsec Tunnel in Manual Mode
Network requirements
•
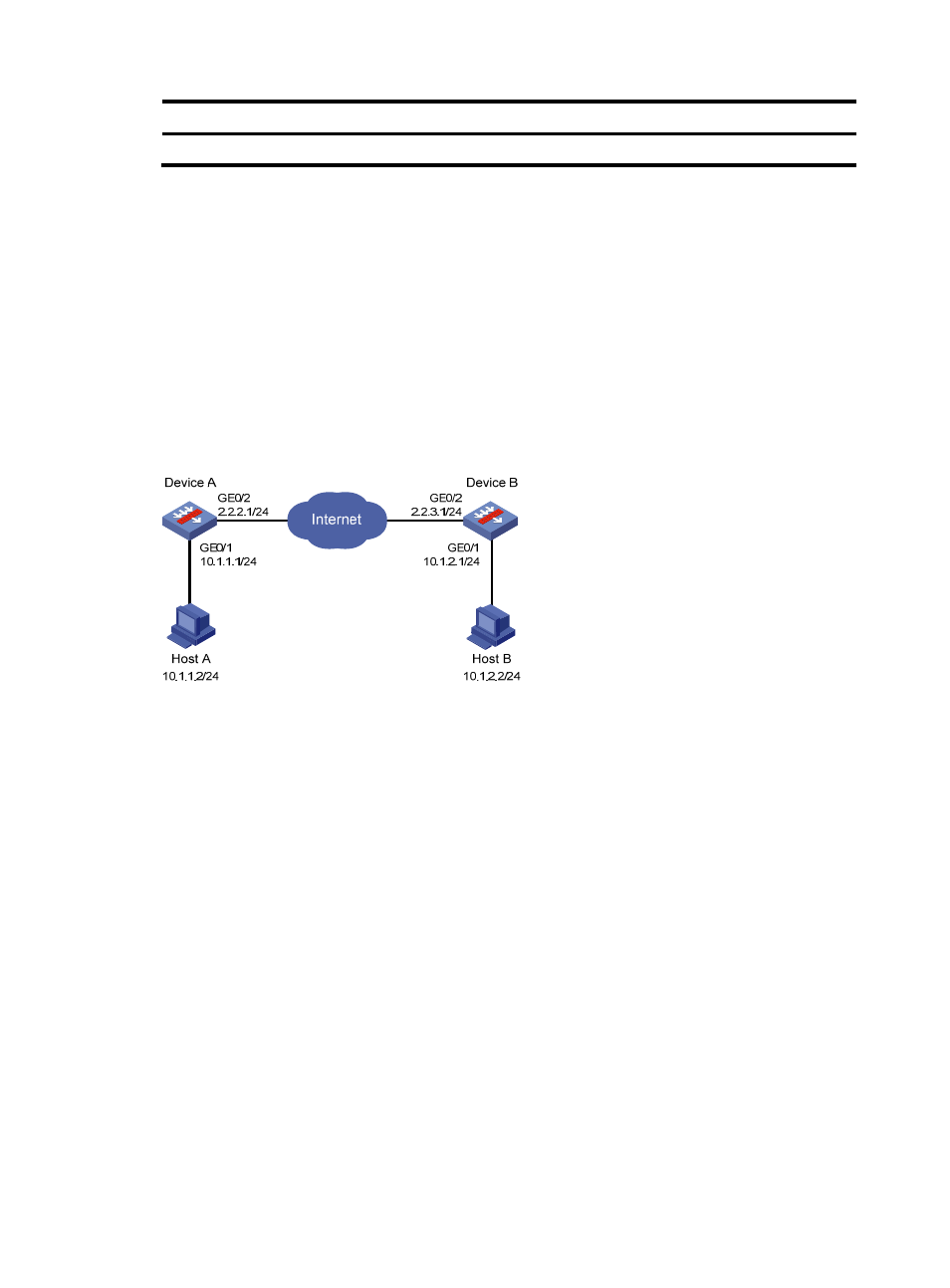
As shown in
, an IPsec tunnel is established between Device A and Device B to protect data
flows between subnet 10.1.1.0/24 and subnet 10.1.2.0/24.
•
The security protocol to be used is ESP, encryption algorithm is DES, and authentication algorithm
is SHA1-HMAC-96.
Figure 6 Network diagram for IPsec configuration
Configuration procedure
1.
Configure Device A
# Define an ACL to identify data flows from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
[DeviceA] acl number 3101
[DeviceA-acl-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0
0.0.0.255
[DeviceA-acl-adv-3101] quit
# Configure a static route to Host B.
[DeviceA] ip route-static 10.1.2.0 255.255.255.0 2.2.2.2
# Create an IPsec proposal named tran1.
[DeviceA] ipsec proposal tran1
# Specify the encapsulation mode as tunnel.
[DeviceA-ipsec-proposal-tran1] encapsulation-mode tunnel
# Specify the security protocol as ESP.
[DeviceA-ipsec-proposal-tran1] transform esp
# Specify the algorithms for the proposal.
[DeviceA-ipsec-proposal-tran1] esp encryption-algorithm des
