Java blocking configuration example, Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 105
6
Java Blocking Configuration Example
Network requirements
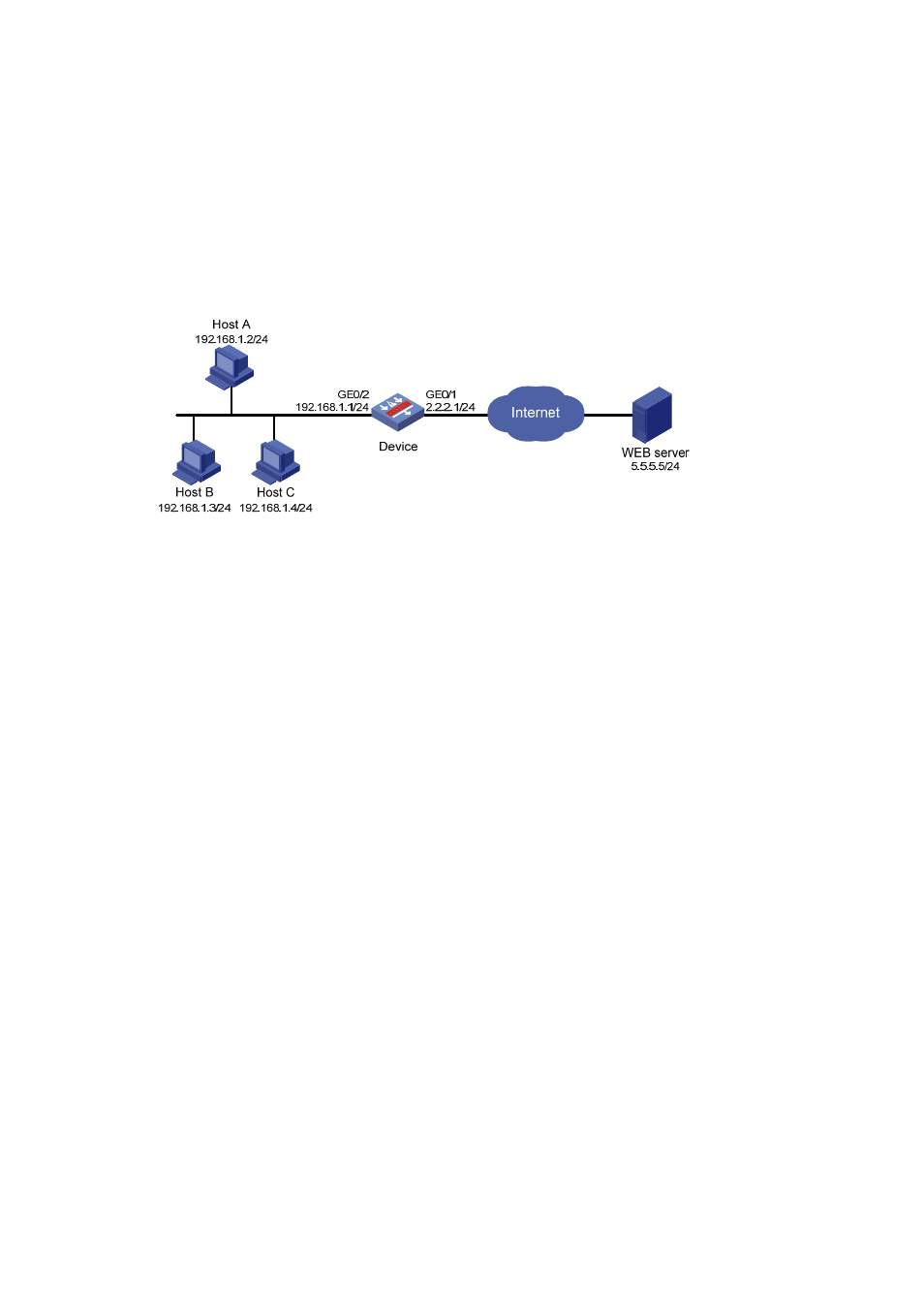
The hosts in the network segment 192.168.1.0/24 access the Internet through Device. Enable Java
blocking on the device, add suffix keyword .js, and configure the device to allow only Java applet
requests to the website at 5.5.5.5.
Figure 2 Network diagram for Java blocking configuration
Configuration procedure
# Configure IP addresses for the interfaces. (Omitted)
# Configure the NAT policy for the outbound interface.
[Device] acl number 2200
[Device-acl-basic-2200] rule 0 permit source 192.168.1.0 0.0.0.255
[Device-acl-basic-2200] rule 1 deny source any
[Device-acl-basic-2200] quit
[Device] nat address-group 1 2.2.2.10 2.2.2.11
[Device] interface gigabitethernet 0/1
[Device-GigabitEthernet0/1] nat outbound 2200 address-group 1
[Device-GigabitEthernet0/1] quit
# Configure an ACL numbered 2100 for Java blocking.
[Device] acl number 2100
[Device-acl-basic-2100] rule 0 permit source 5.5.5.5 0.0.0.0
[Device-acl-basic-2100] rule 1 deny source any
[Device-acl-basic-2100] quit
# Enable the Java blocking function, add blocking suffix keyword .js, and specify ACL 2100 for Java
blocking.
[Device] firewall http java-blocking enable
[Device] firewall http java-blocking suffix .js
[Device] firewall http java-blocking acl 2100
Use the display firewall http java-blocking verbose command to display detailed Java
blocking information.
[Device] display firewall http java-blocking verbose
Java blocking is enabled.
