Encapsulation modes, Figure 1 – H3C Technologies H3C SecPath F1000-E User Manual
Page 131
3
•
Traffic-based lifetime: Defines the maximum traffic that an SA is allowed to process.
An SA becomes invalid when its lifetime expires. Before an existing SA expires, IKE negotiates a new SA
and, once created, the new SA takes over the responsibility immediately.
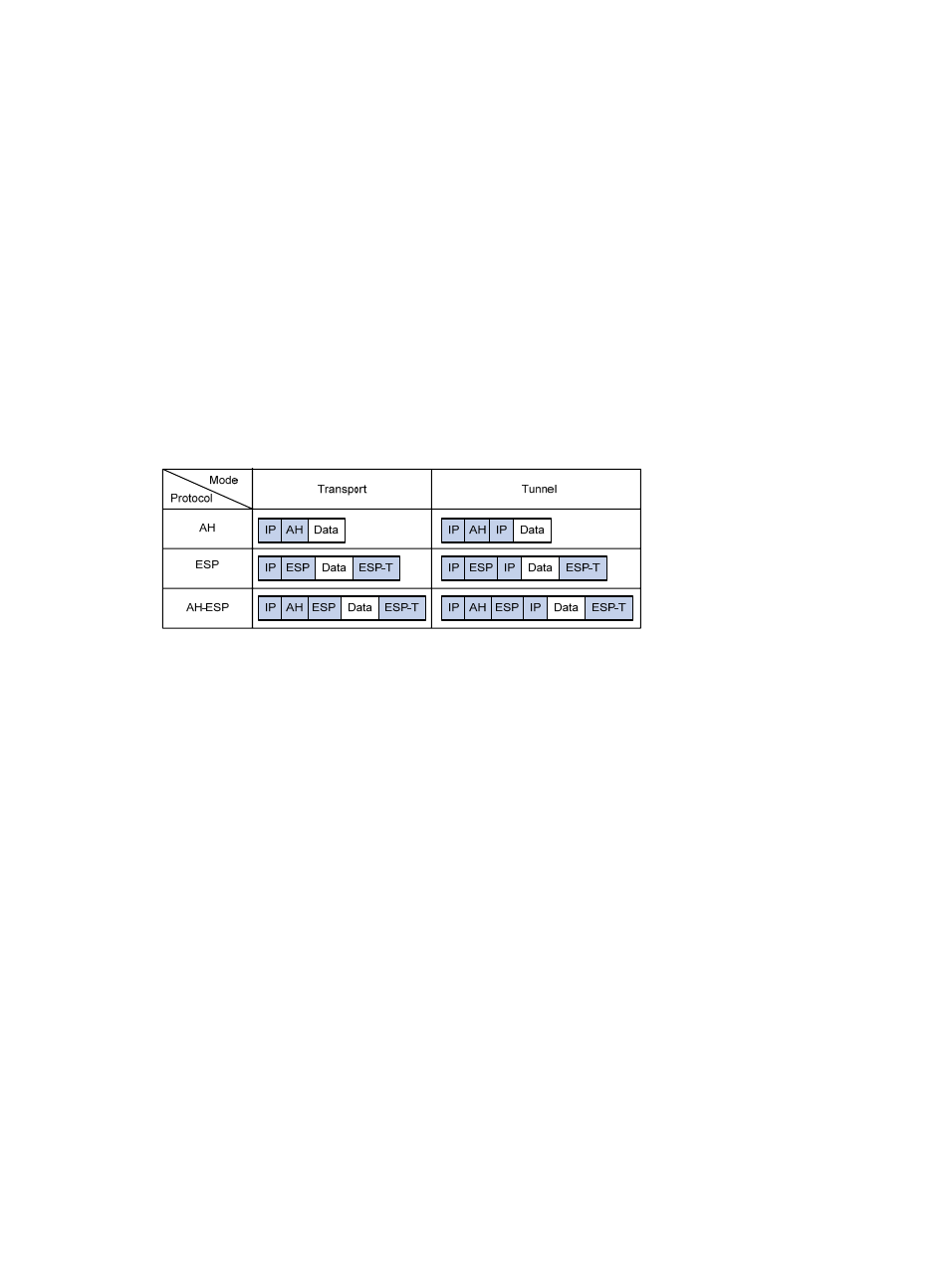
Encapsulation modes
IPsec can work in the following two modes:
•
Tunnel mode: The whole IP packet is used to calculate the AH/ESP header, which will be
encapsulated into a new IP packet together with the ESP-encrypted data. Generally, tunnel mode is
used for communication between two security gateways.
•
Transport mode: Only the transport layer data is used to calculate the AH/ESP header, which will
be put after the original IP header and before the ESP-encrypted data. Generally, transport mode is
used for communication between two hosts or a host and a security gateway.
illustrates how data are encapsulated by different security protocols in tunnel and transport
modes. Here, the term data refers to the transport layer data.
Figure 1 Encapsulation by security protocols in different modes
Authentication algorithms and encryption algorithms
1.
Authentication algorithms
Authentication algorithms are implemented through hash functions. A hash function takes a message of
arbitrary length and generates a message digest of fixed length. IPsec peers calculate the message
digests respectively. If the resulting digests are identical, the packet is considered intact and not
tampered.
There are two types of IPsec authentication algorithms:
•
MD5: Takes a message of arbitrary length and generates a 128-bit message digest.
•
SHA-1: Takes a message of a length less than the 64th power of 2 in bits and generates a 160-bit
message digest.
Slower than MD5, SHA-1 provides higher security.
2.
Encryption algorithms
Most encryption algorithms depend on symmetric key systems, which decrypt data by using the same
keys for encryption. Currently, three encryption algorithms are available for IPsec on the device:
•
DES: Data encryption standard, encrypts a 64-bit block of plain text with a 56-bit key.
•
3DES: Triple DES, encrypts a plain text with three 56-bit DES keys, which total up to 168 bits.
•
AES: Advanced encryption standard, encrypts a plain text with a 128-bit, 192-bit, or 256-bit key.
AES, 3DES, and DES are in descending order in terms of security. Higher security means more complex
implementation and lower speed. DES is enough to meet general requirements.
