Network requirements, Configuration procedure – H3C Technologies H3C SecPath F1000-E User Manual
Page 177
13
[DeviceB] ipsec policy policy 10 isakmp
# Configure the IPsec policy to reference the IKE peer.
[DeviceB-ipsec-policy-isakmp-policy-10] ike-peer peer
# Configure the IPsec policy to reference ACL 3101.
[DeviceB-ipsec-policy-isakmp-policy-10] security acl 3101
# Configure the IPsec policy to reference IPsec proposal prop.
[DeviceB-ipsec-policy-isakmp-policy-10] proposal prop
[DeviceB-ipsec-policy-isakmp-policy-10] quit
# Configure dynamic IP address negotiation for interface Serial 2/0.
[DeviceB] interface serial 2/0
[DeviceB-Serial2/0] ip address ppp-negotiate
# Apply the IPsec policy group to interface Serial 2/0.
[DeviceB-Serial2/0] ipsec policy policy
Example for Configuring IPsec/IKE to Work with ADSL
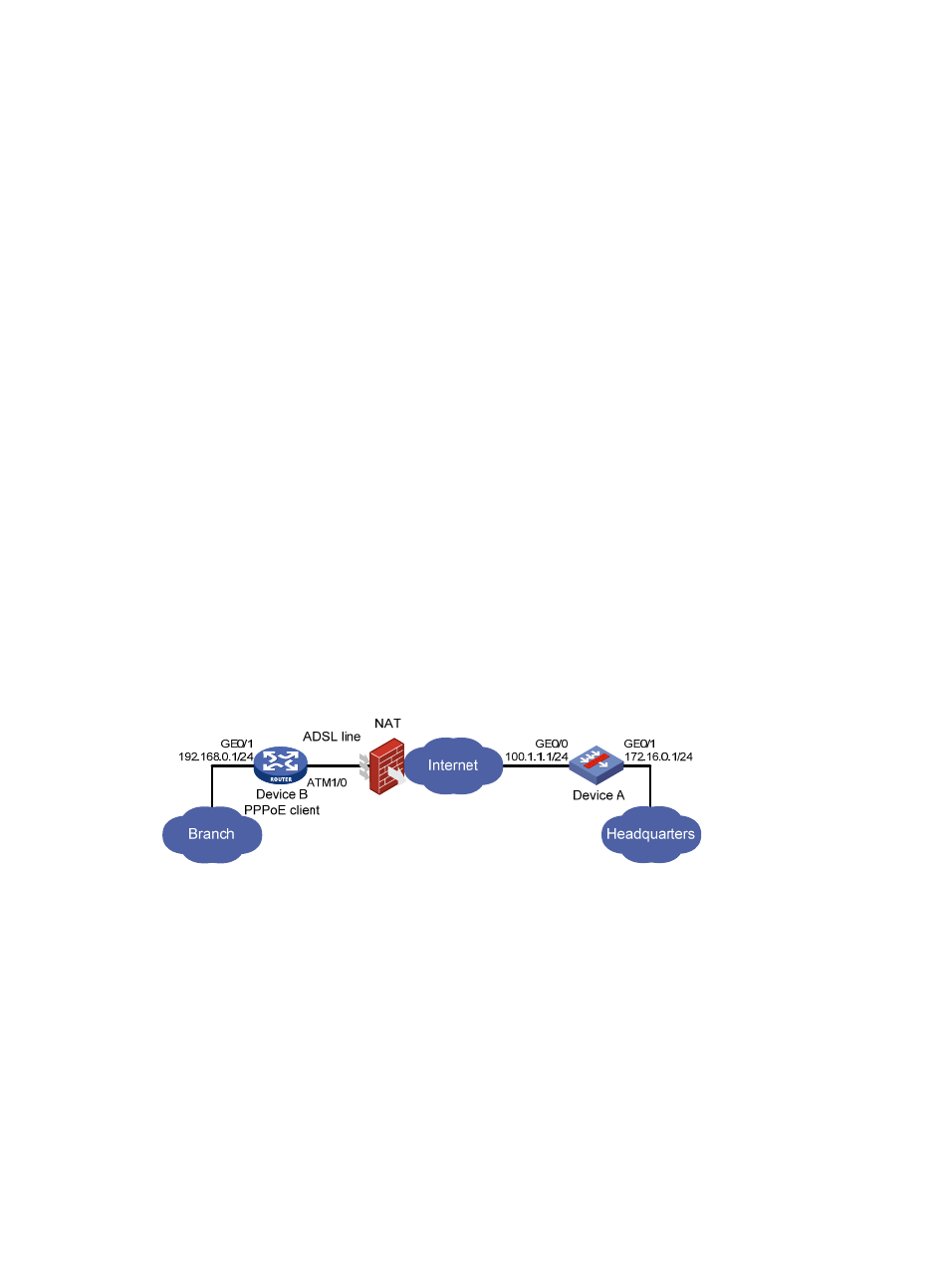
Network requirements
Deploying IPsec in combination with ADSL, this example reflects a popular application of IPsec.
•
As shown in
, Device B is connected to the DLSAM access side of the public network
directly through ADSL as the client of PPPoE. Because Device B can obtain only private address from
its ISP, you need to configure NAT traversal on both Device A and Device B.
•
The headquarters LAN is connected to the network through Device A.
•
To ensure information security, IPsec/IKE is adopted to create an IPsec tunnel.
Figure 13 Network diagram of IPsec/IKE with ADSL
Configuration procedure
1.
Configure Device A
# Specify a name for the local security gateway.
[DeviceA] ike local-name devicea
# Configure an ACL.
[DeviceA] acl number 3101
[DeviceA-acl-adv-3101] rule 0 permit ip source 172.16.0.0 0.0.0.255 destination
192.168.0.0 0.0.0.255
[DeviceA-acl-adv-3101] quit
# Configure an IKE proposal.
